
The key rate shift technique amounts to: Pick several key rates; e.g., 2, 5 10 and 30 year; Make a rule about treating neighbor rates; e.g., linear interpolation; Re-price the bond based on shocking only the key rate (plus its neighbors) but leave the rest of the curve alone. This is the e
From playlist Bonds: Sensitivities

Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

From playlist Cryptography Lectures
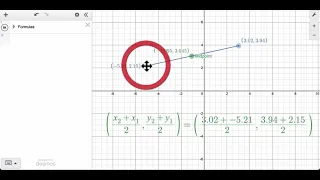
In this video, we show work the goal of the midpoint challenge looks like. @shaunteaches
From playlist desmos

Correctness And Security - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

FRM: Key rate shift: calculation
Yesterday I talked about the conceptual difference between traditional duration and key rate shift; i.e., duration assumes all rates shift in parallel, but a key rate shift assumes only a local key rate shift (and neighboring rates). In this screencast, I show an actual key rate duration c
From playlist Bonds: Sensitivities

SHSAT - reading passage 5 (#29 - #32)
more practice from the reading comprehension section of the SHSAT more at https://sites.google.com/site/teachshsat/
From playlist SHSAT - 8th Grade Test 1

Welcome The Queen! Reel 2 (1954)
Part 2. 01:14:03 Ceylon (Sri Lanka). Sequence showing traditional Sri Lankan images: a statue of a Buddha, paddy fields, a small village. Various shots of women picking tea with a woman speaking on the soundtrack explaining the work she does. Various shots of Buddhist shrines and paper
From playlist The Woman under the Crown: Key Films from Her Life

Xi Chen: The Cost of Keeping up With the Joneses in China
December 3, 2013 Xi Chen, an Assistant Professor at Yale’s School of Public Health. Professor Chen’s research interests involve health and development economics. His work explores how social interactions affect health behavior and outcomes, and how socioeconomic status drives social compet
From playlist The MacMillan Report

Certificates - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

EASTERN PHILOSOPHY - Sen no Rikyu
Sen no Rikyū was a Japanese philosopher who understood the role of a cup of tea in a wise and calm life. SUBSCRIBE to our channel for new films every week: http://tinyurl.com/o28mut7 If you like our films take a look at our shop (we ship worldwide): http://www.theschooloflife.com/shop/all/
From playlist GREAT IDEAS

Prince Charles: Investiture of the Prince of Wales aka POW (1969) | British Pathé
A very young Prince Charles does a brief introduction before the remarkable archive footage of his investiture ceremony at Carnarvon Castle, Wales in 1969. For Archive Licensing Enquiries Visit: https://goo.gl/W4hZBv Explore Our Online Channel For FULL Documentaries, Fascinating Intervie
From playlist The Woman under the Crown: Key Films from Her Life

Royal Decade - Technicolor (1963)
This item is filmed in Technicolor. Various. Title reads "Royal Decade - Ten years after the Coronation we review the truly royal progress of our young Queen". Several shots of the Trooping the Colour ceremony 1963 - Queen Elizabeth II is seen riding onto parade ground. Variou
From playlist The Woman under the Crown: Key Films from Her Life

Recipes at http://www.ciaprochef.com/WCA/ On the next stop of our tour of Indonesian sate, we visit Chef Heinz van Holzen at his Restaurant Bumbu Bali Benoa, in Tanjung, Bali. Originally born in Switzerland, Chef van Holzen has lived in Bali since 1990, and is a Balinese cuisine cookbook
From playlist Culinary Institute of America: Cooking Demonstrations | CosmoLearning.org Culinary

Abel Award ceremony 2017 - Yves Meyer
The Abel Prize Award Ceremony, May 23, 2017. Place: The University Aula, Oslo, Norway 0:00 Procession accompanied by the “Abel Fanfare” (Klaus Sandvik) Performed by musicians from The Staff Band of the Norwegian Armed Forces 0:39 His Majesty King Harald enters the University Aula 1:37 Ri
From playlist Abel Prize Ceremonies

To Westminster - The Queen - Technicolor (1966)
This item is filmed in Technicolor. London. Long shot of the Houses of Parliament. Close up shot of the crown on a pillow. Top shot, inside Parliament, of ceremony of the Opening of the Parliament. Lord Bernard Montgomery carrying the Sword of State. Lord Chamberlain takes crown with
From playlist The Woman under the Crown: Key Films from Her Life

ICM 2018 - Rio de Janeiro | http://www.icm2018.org © 2018 Rio ICM2018 & International Mathematical Union Os direitos sobre todo o material deste canal pertencem ao Instituto de Matemática Pura e Aplicada, sendo vedada a utilização total ou parcial do conteúdo sem autorização prévia e
From playlist Ceremonies ICM 2018

How to Build a KeyLogger in C++ | Session 18 | #C | #programming
Don’t forget to subscribe! This project series is about creating a Keylogger in C++. A KeyLogger is a program that can capture every key or click that is pressed on the computer asynchronously. In order to get useful information, we will learn how to erase the cache, build the keylogger
From playlist Build A KeyLogger In C++

