
Introduction to the C programming language. Part of a larger series teaching programming. See http://codeschool.org
From playlist The C language

DEFCON 19: Chip & PIN is Definitely Broken
Speakers: Andrea Barisani Inverse Path S.r.l. | Adam Laurie Aperture Labs Ltd | Zac Franken Aperture Labs Ltd | Daniele Bianco Inverse Path S.r.l. The EMV global standard for electronic payments is widely used for inter-operation between chip equipped credit/debit cards, Point of Sales d
From playlist DEFCON 19
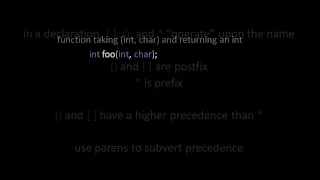
Introduction to the C programming language. Part of a larger series teaching programming. See http://codeschool.org
From playlist The C language

DEFCON 19: Chip & PIN is Definitely Broken ( w speaker)
Speakers: Andrea Barisani Inverse Path S.r.l. | Adam Laurie Aperture Labs Ltd | Zac Franken Aperture Labs Ltd | Daniele Bianco Inverse Path S.r.l. The EMV global standard for electronic payments is widely used for inter-operation between chip equipped credit/debit cards, Point of Sale
From playlist Payments

A review of the notes common to all formations of a G chord.
From playlist Music Lessons

Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

Fast, Furious and Insecure: Hacking Tesla S
Our research revealed several weaknesses in the Tesla Model S passive keyless entry and start system. The talk will be a comprehensive overview of how we reverse engineered the key fob, the issues we found and an efficient proof of concept attack. The proof of concept attack exploits the u
From playlist Security

In this video, you’ll learn more about how hashtags are used on Twitter. Visit https://www.gcflearnfree.org/twitter/what-is-a-hashtag/1/ for our text-based lesson. This video includes information on: • Using hashtags • Browsing popular hashtags We hope you enjoy!
From playlist Twitter

Subscribe to our YouTube Channel for all the latest from World Science U. Visit our Website: http://www.worldscienceu.com/ Like us on Facebook: https://www.facebook.com/worldscienceu Follow us on Twitter: https://twitter.com/worldscienceu
From playlist Science Unplugged: General Relativity

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

Block Ciphers and Data Encryption Standard (DES) - Part 1
Fundamental concepts of Block Cipher Design Principles are discussed. DES is presented. Differential and linear cryptanalysis are explained . Block Cipher Principles Data Encryption Standard (DES) Differential and Linear Cryptanalysis Block Cipher Design Principles
From playlist Network Security

Bogoliubov theory for trapped Bose-Einstein condensates - Benjamin Schlein
Analysis Seminar Topic: Bogoliubov theory for trapped Bose-Einstein condensates Speaker: Benjamin Schlein Affiliation: University of Zurich Date: January 25, 2021 For more video please visit http://video.ias.edu
From playlist Mathematics

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

GRCon20 - Security Analysis of Zigbee Networks with Zigator and GNU Radio
Presented by Dimitrios-Georgios Akestoridis, Madhumitha Harishankar, Michael Weber and Patrick Tague at GNU Radio Conference 2020 https://gnuradio.org/grcon20 Zigbee is a wireless communication protocol that is based on the IEEE 802.15.4 standard and is commonly used in smart homes. Numer
From playlist GRCon 2020

24C3: Relay attacks on card payment: vulnerabilities and defences
Speaker: Steven J. Murdoch Keeping your enemies close Relay attacks allow criminals to use credit or debit cards for fraudulent transactions, completely bypassing protections in today's electronic payment systems. This talk will show how using easily available electronics, it is possibl
From playlist 24C3: Full steam ahead

What Size Magnet Can ERASE a Credit Card?
Check out Samy's channel: https://youtu.be/UHSFf0Lz1qc Don’t try this at home! The experiments and products shown in this episode were used in the name of science. If you liked this video check out these: The HIDDEN Magnets in Your Phone! https://www.youtube.com/watch?v=HodWkE0G28M How t
From playlist Electricity and Magnetism

IBM Mag Card Selectric Typewriter 1969 : MC/ST Electronic Word Processing, Magnetic Storage
The 1969 IBM Magnetic Card Selectric Typewriter (“Mag Card”). A look back at a vintage 1969 office environment with dictation machines and the Mag Card system. The Mag Card and its successor machines facilitated the link between electronic typing and computer storage of data, and increase
From playlist Word Processing, Office Automation, Electronic Office Tools

Adam Savage's One Day Builds: New Workbench Lights!
When Adam received his new shop workbench, builder Andrew Klein incorporated his take on Adam's LED lamp lighting solution into the bench, attached using a strong Magswitch for durability and ease of adjustment. Adam still has the lamps from his previous workbench, and modifies them in thi
From playlist Adam Savage's One Day Builds

Irma from the ASU MA in Global Security (MAGS)
The ASU Online MA in Global Security (MAGS) student body is diverse and comes to the program from a variety of educational and professional backgrounds, including members of the US military, members of other national militaries, government officials, humanitarian assistance workers, law en
From playlist Master's in global security

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography