Random Oracle - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Voter Identity Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Password Reuse - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Voter Identity - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Speakers: Radu State, Humberto Abdelnur, and Olivier Festo clip 2/6
From playlist ShmooCon 2008

TraversalConf 2019: Your Data is Showing by Madison Kerndt
TraversalConf 2019: Your Data is Showing by Madison Kerndt
From playlist TraversalConf 2019
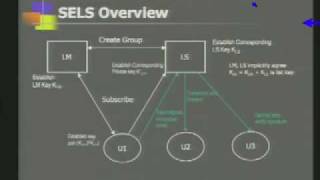
CERIAS Security: Minimizing Trust Liabilities in Secure Group Messaging Infrastructures 2/5
Clip 2/5 Speaker: Himanshu Khurana · University of Illinois at Urbana-Champaign Large-scale collaborative applications are characterized by a large number of users and other processing end entities that are distributed over geographically disparate locations. Therefore, these applicat
From playlist The CERIAS Security Seminars 2005 (1)

Token Authentication for Java Applications
In this presentation, Les will demystify HTTP Authentication and explain how the Next Big Thing - Token Authentication - can be used to secure web applications on the JVM, REST APIs, and 'unsafe' clients while supporting security best practices and even improving your application's perform
From playlist Software Development Lectures

User Authentication Protocols: Part 2
Fundamental concepts of remote user authentication are discussed. Kerberos are Analyzed. Federated identity management are presented.
From playlist Network Security

Practical API Security || Ahmed Elharouny
API security has emerged as a key priority for protecting vital data and services. It's also an area where many companies lack expertise. PUBLICATION PERMISSIONS: API Days Conference Organizer provided Coding Tech with the permission to republish API Days tech talks. CREDITS: API Days Y
From playlist APIs

SSH Authentication - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Speaker: Hendrik Scholz Introduction to SIP Hacking Within the last year VoIP devices and applications flooded the market. SIP (Session Initiation Protocol) became the industry standard although it's still under constant development. VoIP networks converge with the PSTN and thus offer wa
From playlist 22C3: Private Investigations

Cyber Security Full Course 2023 | Cyber Security Course Training For Beginners 2023 | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=CyberSecurityFullCourse2023-hXSFdwIOfnE&utm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.
From playlist Cyber Security Playlist [2023 Updated]🔥

Cyber Security Live - 1 | Cyber Security Tutorial For Beginners | Cyber Security Training | Edureka
🔥Cyber Security Training: https://www.edureka.co/cybersecurity-certification-training This Edureka video on Cyber Security gives an introduction to the Cyber Security world and talks about its basic concepts. You get to know different kinds of attacks in today's IT world and how cybersecur
From playlist Edureka Live Classes 2020

Communications and Network Security | CISSP Training Videos
🔥 Enroll for FREE CISSP Course & Get your Completion Certificate: https://www.simplilearn.com/learn-cloud-security-basics-skillup?utm_campaign=CCSP&utm_medium=DescriptionFirstFold&utm_source=youtube Communication and Network Security : Domain 4 of the CISSP certification course offered by
From playlist Cyber Security Playlist [2023 Updated]🔥

Cyber Security Full course - 11 Hours | Cyber Security Training For Beginners | Edureka
🔥𝐄𝐝𝐮𝐫𝐞𝐤𝐚 𝐂𝐲𝐛𝐞𝐫 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 (𝐔𝐬𝐞 𝐂𝐨𝐝𝐞: 𝐘𝐎𝐔𝐓𝐔𝐁𝐄𝟐𝟎) : https://www.edureka.co/cybersecurity-certification-training This Edureka video on "Cyber Security Full Course" will help you understand and learn the fundamentals of Cyber Security. This Cyber Security Tutorial is ideal for both be
From playlist Cyber Security Training for Beginners | Edureka

Secure Shell Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cybersecurity Tutorial | Demo On Man In The Middle Attack | Cybersecurity Training | Edureka
🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl This "Cybersecurity tutorial" video presented by edureka gives an indepth information about the Cyber Security world and talks about its basic concepts.
From playlist Cyber Security Training for Beginners | Edureka