Open Source vs. Closed Source Software
In this video, you’ll learn more about the differences between open-source software and closed-source software. Visit https://edu.gcfglobal.org/en/basic-computer-skills/ for more technology, software, and computer tips. We hope you enjoy!
From playlist Technology Trends

Security is always a concern as our products ship, especially in today's world of cracking attempts. But, what enables the crackers to be able to break into systems? Oftentimes, the answer is that they reverse engineer your product. In this tutorial, we will examine the techniques used by
From playlist Software Development

LINUX: Command Line IP - Comparing openSUSE 11.3 with Windows 7
More videos like this at http://www.theurbanpenguin.com : In IT Windows is not all about the GUI and Linux not all about command line tools. So in this demo we look at using command line tools to set the IP address and default gateway on both openSUSE11.3 and Windows 7.
From playlist Windows

Computer Basics: Buttons and Ports on a Computer
Every computer has it's own set of buttons and ports. We'll show you some of the most common ones so you can identify the ones that your device has. We hope you enjoy! To learn more, check out our written lesson: https://edu.gcfglobal.org/en/computerbasics/buttons-and-ports-on-a-computer/
From playlist Starting out with Technology

What Is Quantum Computing | Quantum Computing Explained | Quantum Computer | #Shorts | Simplilearn
🔥Explore Our Free Courses With Completion Certificate by SkillUp: https://www.simplilearn.com/skillup-free-online-courses?utm_campaign=QuantumComputingShorts&utm_medium=ShortsDescription&utm_source=youtube Quantum computing is a branch of computing that focuses on developing computer tech
From playlist #Shorts | #Simplilearn

Quantum Computers, Explained With Quantum Physics
Quantum computers aren’t the next generation of supercomputers—they’re something else entirely. Before we can even begin to talk about their potential applications, we need to understand the fundamental physics that drives the theory of quantum computing. (Featuring Scott Aaronson, John Pr
From playlist Explainers

Speaker: Ralf-Philipp Weinmann Backdooring Embedded Controllers Want to persistently backdoor a laptop? Backdooring the BIOS is out of the question since your target can dump and diff it? Planting hardware is out of the question as well? Shhhhhhh.. I have something for you: Embedded con
From playlist 27C3: We come in peace

DEFCON 13: The Next Generation of Cryptanalytic Hardware
Speaker: The Next Generation of Cryptanalytic Hardware David Hulton, Dachb0den Labs Encryption is simply the act of obfuscating something to the point that it would take too much time or money for an attacker to recover it. Many algorithms have time after time failed due to Moore's law
From playlist DEFCON 13

DEFCON 20: Hardware Backdooring is Practical
Speaker: JONATHAN BROSSARD TOUCAN SYSTEM This presentation will demonstrate that permanent backdooring of hardware is practical. We have built a generic proof of concept malware for the intel architecture, Rakshasa, capable of infecting more than a hundred of different motherboards. The f
From playlist DEFCON 20

ShmooCon 2014: Genuinely "Trusted Computing:" Free and Open Hardware Security Modules
For more information visit: http://bit.ly/shmooc14 To download the video visit: http://bit.ly/shmooc14_down Playlist Shmoocon 2014: http://bit.ly/shmooc14_pl Speaker: Ryan Lackey "Trusted Computing" unfortunately often means trusting a black box provided by a third party who may not be p
From playlist ShmooCon 2014

Security Vulnerability Mitigations
Security vulnerabilities allow software to be manipulated in such a way that it misbehaves to the benefit of an attacker - security vulnerability mitigations work to thwart attempts to successfully exploit such a vulnerability. This landscape is continually changing in both the types of at
From playlist Security

How Intel wants to backdoor every computer in the world | Intel Management Engine explained
Intel embeds Management Engine into all of its computers since 2008. Intel Management Engine has been criticized for its security risks and has been called a backdoor with rootkit possibilities by many security experts and researchers. This is Intel Management Engine. A subsystem micropr
From playlist Decrypted Lies
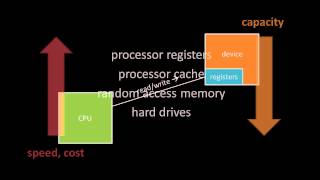
Essential concepts of computer hardware. Part of a larger series teaching programming. Visit http://codeschool.org
From playlist Hardware Basics

Attack of the Tails: Yes, you Really can Backdoor Federated Learning
A Google TechTalk, 2020/7/30, presented by Dimitris Papailiopoulos, University of Wisconsin-Madison ABSTRACT: Due to its decentralized nature, Federated Learning (FL) lends itself to adversarial attacks in the form of backdoors during training. A range of FL backdoor attacks have been in
From playlist 2020 Google Workshop on Federated Learning and Analytics

SOURCE Boston 2008: Information Operations
Speaker: Sinan Eren This presentation will discuss techniques to attack secure networks and successfully conduct long term penetrations into them. New Immunity technologies for large scale client-side attacks, application based backdoors will be demonstrated as will a methodology for high
From playlist SOURCE Boston 2008

For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speakers: Nadia Heninger | djb | Tanja Lange This was a busy year for crypto. TLS was broken. And then broken again. Discrete logs were computed. And then computed again.
From playlist 30C3

30C3: The Year in Crypto (DE - translated)
For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speakers: Nadia Heninger | djb | Tanja Lange This was a busy year for crypto. TLS was broken. And then broken again. Discrete logs were computed. And then computed again.
From playlist 30C3

The True Story of the Windows _NSAKEY
Microsoft _NSAKEY is a signing key found in Microsoft's CryptoAPI since Windows 95. Many claimed this was the ultimate backdoor for the National Security Agency. But is this a hoax, or is the _NSAKEY a real backdoor in Microsoft Windows? A British researcher discovered that Microsoft was
From playlist Decrypted Lies
