
Computer Basics: Protecting Your Computer
There are many different online threats that you need to be aware of. In this video, we're going to show you some of these threats and talk about how to protect the files and personal data that you have stored on your computer. We hope you enjoy! For more info, check out our written less
From playlist Starting out with Technology

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

How to protect your computer from malware and hackers 2017 | Malware protection tutorial
Please watch: "How Facebook targeted advertisements track you online, offline and where they sell your private data" https://www.youtube.com/watch?v=9sFl2qGedFQ -~-~~-~~~-~~-~- How to protect your computer from malware and hackers in 2017? Protection against malware and viruses is often
From playlist TUTORIALS & HOW TO's

Application Security Tutorial | Application Security Basics | Cyber Security Tutorial | Simplilearn
In this application tutorial, we will cover application security basics in this cyber security tutorial. We will cover the basic definitions of application security, along with the different types and categories of application security. Next we cover the common application security vulnera
From playlist Cyber Security Playlist [2023 Updated]🔥

Firmware Security: Why It Matters and How You Can Have It
A system is only as secure as the least secure component it depends on. Hardening the kernel is a vital part of developing a secure operating system, but if the firmware underneath the kernel is insecure then attackers have an opportunity to sidestep your security and compromise you anyway
From playlist Security

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Staysafe.org: Protect your computer
The Internet is a global network that connects us to limitless information and opportunities. But there are risks involved with connecting to the Internet, such as downloading viruses and spyware onto computers and devices. Watch this video for four easy steps to help protect your computer
From playlist awareness

Kernel Recipes 2019 - Kernel hacking behind closed doors
The recent hardware security vulnerabilites exposed the kernel community to unprecedented restrictions and bureaucrazy. Pure software bugs which only affect the Linux kernel are a completely different category and the kernel community has established and well working ways to handle them.
From playlist Kernel Recipes 2019

Bitcoin Q&A: Protocol Development Security
What are the odds of "rogue developers" who introduce vulnerabilities? What happens if the digital signature algorithm is compromised? Is trust in hardware wallet developers and the firmware update process a problem? Note: I was mostly talking about Bitcoin and other popular open blockcha
From playlist English Subtitles - aantonop Videos with subtitles in English

What Is Malware? | Malware Explained | What Is Malware And It's Types? | Malware Attack |Simplilearn
In this video on what is malware?, we will get to understand malware explained, what is malware and it's types? We will also know specifically about viruses and trojans, their operation process, types of malicious programs, and how to prevent a malware attack. Through this, we can protect
From playlist Cyber Security Playlist [2023 Updated]🔥

DevOpsDays Chicago 2019 - Jessie Frazelle - Why Open Source Firmware is Important
Jessie Frazelle - Why Open Source Firmware is Important This talk will dive into some of the problems of running servers at scale, with data from surveys and why open source firmware will solve some of the problems. Why is it important for security and root of trust? It will also cover th
From playlist DevOpsDays Chicago 2019

HITB SecConf 2009 Malaysia: Hardware is the New Software 3/6
Clip 3/6 Speaker: Joe Grand aka Kingpin (President, Grand Idea Studio) Society thrives on an ever increasing use of technology. Electronics are embedded into nearly everything we touch. Hardware products are being relied on for security-related applications and are inherently trusted,
From playlist Hack In The Box Malaysia 2009

Kernel Recipes 2015 - Hardened kernels for everyone - By Yves-Alexis Perez
Grsecurity is a Linux kernel hardening patch. The PaX patchset it includes pioneered some security features like ASLR which where later included in basically every operating system. But the patch itself is still standalone (not included mainline), so most Linux users don’t benefit its secu
From playlist Kernel Recipes 2015

DEFCON 19: Virtualization under attack: Breaking out of KVM
Speaker: Nelson Elhage KVM, the Linux Kernel Virtual Machine, seems destined to become the dominant open-source virtualization solution on Linux. Virtually every major Linux distribution has adopted it as their standard virtualization technology for the future. And yet, to date, remarkabl
From playlist DEFCON 19

Kernel Recipes 2017 - The State of Kernel Self-Protection - Kees Cook
The Kernel Self-Protection Project focuses on addressing gaps in Linux’s defensive technologies. With Linux reaching into every corner of modern life, and userspace frequently being very locked-down, the kernel has become an ever-increasing target for attackers and much more needs to be do
From playlist Kernel Recipes 2017

DEFCON 19: Familiarity Breeds Contempt
Speakers: Sandy "Mouse" Clark University of Pennsylvania | Brad "RenderMan" Haines Chief research monkey, Renderlab.net "Good programmers write code, great programmers reuse" is one of the most well known truisms of software development. But what does that mean for security? For over 30 y
From playlist DEFCON 19
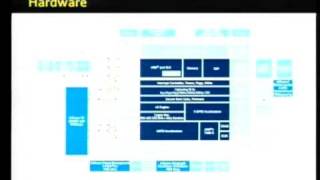
Speakers: MuscleNerd, pytey, planetbeing Apple's iPhone has made a tremendous impact on the smartphone market and the public consciousness, but it has also highlighted their desire to carefully control the device with draconian restrictions. These restrictions prevent users from choosing
From playlist 25C3: Nothing to hide

http://www.365computersecuritytraining.com This video is an excerpt from our online training in computer security. It Covers some of the basic terminology used in the information technology security profession. Some of the terms covered are: Vulnerability, Threats, Assets, Risk...and
From playlist awareness

5 Devastating Security Flaws You've Never Heard Of
Devastating vulnerabilities are hiding in the technology in programs, protocols, and hardware all around us. Most of the time, you can find ways to protect yourself. Hosted by: Michael Aranda SciShow has a spinoff podcast! It's called SciShow Tangents. Check it out at http://www.scishowt
From playlist Uploads