
Gentle Intro to Generative Adversarial Networks - Part 1 (GANs)
Join my Foundations of GNNs online course (https://www.graphneuralnets.com)! This video gives a high-level overview of Generative Adversarial Networks (GANs). A simple coin-flip example demonstrates the key aspects of adversarial learning. 3-part blog series: Part 1: https://blog.zakj
From playlist Generative Adversarial Networks

The reliability of machine learning systems in the presence of adversarial noise has become a major field of study in recent years. As ML is being used for increasingly security sensitive applications and is trained in increasingly unreliable data, the ability for learning algorithms to to
From playlist Top 10 Tutorials and Talks: Adversarial Machine Learning

This video explains the paper presenting Deep Convolutional Generative Adversarial Networks! Thanks for watching, Please Subscribe!
From playlist Generative Adversarial Networks
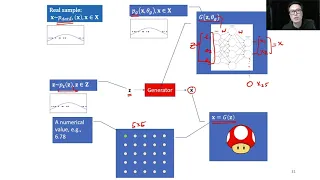
Generative Adversarial Networks (GANs) - Part 1
This video is about Generative Adversarial Networks (GANs) - Part 1
From playlist Generative Adversarial Networks (GANs)

Adversarial Machine Learning Ian Goodfellow
Google's Ian Goodfellow joined us to share his research. Full slides: http://www.iangoodfellow.com/slides/2018-05-24.pdf
From playlist Top 10 Tutorials and Talks: Adversarial Machine Learning

Lecture 16 | Adversarial Examples and Adversarial Training
In Lecture 16, guest lecturer Ian Goodfellow discusses adversarial examples in deep learning. We discuss why deep networks and other machine learning models are susceptible to adversarial examples, and how adversarial examples can be used to attack machine learning systems. We discuss pote
From playlist Top 10 Tutorials and Talks: Adversarial Machine Learning

Kaggle Reading Group: Probing Neural Network Comprehension of Natural Language Arguments (Part 2)
BERT (which we read the paper for earlier) has had really impressive success on a number of NLP tasks... but how well is it really capturing the structures of natural language? This week we're continuing with "Probing Neural Network Comprehension of Natural Language Arguments" (Niven & K
From playlist Kaggle Reading Group | Kaggle

TUNIT: Rethinking the Truly Unsupervised Image-to-Image Translation (Paper Explained)
Image-to-Image translation usually requires corresponding samples or at least domain labels of the dataset. This paper removes that restriction and allows for fully unsupervised image translation of a source image to the style of one or many reference images. This is achieved by jointly tr
From playlist Papers Explained

Example Memorization in Learning: Batch and Streaming
A Google TechTalk, presented by Gavin Brown, 2022/08 /17 Differential Privacy for ML seminar series.
From playlist Differential Privacy for ML

DEFCON 15: Securing the Tor Network
Mike Perry Mad Computer Scientist, fscked.org evil labs Imagine your only connection to the Internet was through a potentially hostile environment such as the Defcon wireless network. Worse, imagine all someone had to do to own you was to inject some html that runs a plugin or some clever
From playlist DEFCON 15

MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012 View the complete course: http://ocw.mit.edu/6-02F12 Instructor: Hari Balakrishnan This lecture introduces communication networks, with MIT's network serving as an example. Packet-switched networks are discussed wi
From playlist MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012

Foundational Aspects of Blockchain Protocols (Lecture 1) by Juan Garay
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

Network design games in presence of strategic adversaries by Prithwish Basu
Games, Epidemics and Behavior URL: http://www.icts.res.in/discussion_meeting/geb2016/ DATES: Monday 27 Jun, 2016 - Friday 01 Jul, 2016 VENUE : Madhava lecture hall, ICTS Bangalore DESCRIPTION: The two main goals of this Discussion Meeting are: 1. To explore the foundations of policy d
From playlist Games, Epidemics and Behavior

Image generative modeling for future prediction or (...) - Couprie - Workshop 1 - CEB T1 2019
Couprie (Facebook) / 05.02.2019 Image generative modeling for future prediction or inspirational purposes Generative models, and in particular adversarial ones, are becoming prevalent in computer vision as they enable enhancing artistic creation, inspire designers, prove usefulness in s
From playlist 2019 - T1 - The Mathematics of Imaging

A Blueprint of Standardized and Composable Machine Learning - Eric Xing
Seminar on Theoretical Machine Learning Topic: A Blueprint of Standardized and Composable Machine Learning Speaker: Eric Xing Affiliation: Carnegie Mellon University Date: August 6, 2020 For more video please visit http://video.ias.edu
From playlist Mathematics

Onion Routing - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography



