
YouTube Has Blacklisted My Channel
YouTube is refusing to suggest my content to my subscribers and wider audiences. This can't go on. If you value my videos, please support my independent work on: https://www.patreon.com/thehatedone I have never trusted YouTube. I have always considered it a necessary evil for this channe
From playlist All of my videos

From playlist Multimedia Systems

Content Marketing Tutorial - Getting setup to create video content
Learn about the essential tools and skills you'll need to produce engaging video content. Explore more Content Marketing courses and advance your skills on LinkedIn Learning: https://www.linkedin.com/learning/topics/content-marketing?trk=sme-youtube_M140599-07-08_learning&src=yt-other Thi
From playlist Content Marketing

Security for Modern Webapps: New Web Platform Security Features to Protect your Application
Web applications have historically been plagued by vulnerabilities which allow attackers to compromise the session of a logged-in user: XSS, CSRF, clickjacking and related issues. Luckily, new security mechanisms available in web browsers in 2019 offer exciting features which allow develop
From playlist Security

How to Create Content that's “Better” than Your Competitor’s
In this video, you’ll learn how to create content that's better than your competitor's by focusing on the four attributes that make content great. Subscribe ► https://www.youtube.com/AhrefsCom?sub_confirmation=1 *************************************** Additional Content Marketing Resourc
From playlist Content Marketing and Blogging Tutorials

IP Problems, YouTube, and the Future: Crash Course Intellectual Property #7
In which Stan Muller talks about some of the problems in Intellectual Property law as it exists today. He'll also teach you a little about how IP law applies to everyone's favorite media platform, YouTube. Lastly, he'll do a little prognosticating, and try to predict how IP law might chang
From playlist Intellectual Property

Dungeons & Dragons Rolls a 1 on New License (OGL 1.1) ft. Matt Colville
Listen up you nerds, it would be great if you could help support Richard Hoeg's recovery here: https://www.gofundme.com/f/reasonable-minds-can-rebuild Extra thanks to @mcolville for the assist! 🚀 Watch my next video early & ad-free on Nebula! https://legaleagle.link/watchnebula 👔 Suits by
From playlist Law Review News!

Does it really matter what browser I choose?
You have a choice of browsers to select from. What makes a browser more - or less - secure? Learn some ways to assess a browser's security.
From playlist Internet Safety

Net Neutrality: The Battle to Keep the Internet Open and Free with Barbara van Schewick
It's easy to take for granted that we get to use the websites and apps of our choice. That's thanks to net neutrality, the principle that we get to make those decisions, not the companies we pay to get online. But in 2017, the FCC decided to eliminate net neutrality. Come explore what net
From playlist Reunion Homecoming Classes Without Quizzes and Micro Lectures

Thanks to the DeepSec organisation for making these videos available and let me share the videos on YouTube. Speakers: Zane Lackey | Luis Mira Zane Lackey & Luis Miras of iSEC Partners talk about Short Message Service (SMS) communication and how it can be attacked. This is another exampl
From playlist DeepSec 2009

CERIAS Security: Hiding the Message Behind the Words: Advances in Natural Language Watermarking 1/4
Clip 1/4 Speaker: Mercan Topkara · Purdue University The Internet has become one of the main sources of knowledge acquisition, harboring resources such as online newspapers, web portals for scientific documents, personal blogs, encyclopedias, and advertisements. It has become a par
From playlist The CERIAS Security Seminars 2007

SOURCE Boston 2008: Content Awareness: A Cornerstone to Data Prote
Speaker: John Amaral - CTO of Vericept The perimeters of a corporate network are expanding. Mobile devices and ubiquitous network access have blurred the network edge. Uninhibited information flow is critical to business continuity; however, as information flows freely across these bounda
From playlist SOURCE Boston 2008

29C3: INDECT, Verhaltenserkennung & Co (DE)
Speaker: Ben automatisierte staatliche Verdächtigung INFECT: "Bei der Forschung an unserem neuen Killervirus hat unsere Ethikkommission penibelst darauf geachtet, dass niemand der Forscher sich ansteckt." Obwohl sowohl Erfahrungen als auch Studien gezeigt haben, dass Videoüberwachung im
From playlist 29C3: Not my department

From the Interactive Media & Games Seminar Series; Todd Smithline, Principal of Smithline PC addresses how the rules and mechanics of a game have historically not been protected by copyright. A recent spate of cases involving clones of mobile video games, however, is challenging that under
From playlist Interactive Media & Games Seminars FALL 2015

Speaker: Nicholas Bentley A new approach to copyright in the digital world A discussion of the Intellectual Contributions model and the Rights Office system as an alternative for regulating copyright in a digital environment. For more information visit: http://bit.ly/22c3_information To
From playlist 22C3: Private Investigations
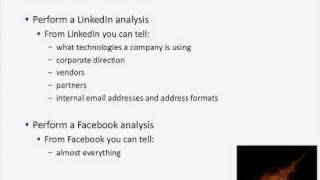
O'Reilly Webcast: Information Security and Social Networks
Social networks are an information security game changer, and enterprises and their management are struggling to understand and deal with the security risks of social networks. Traditional information security protected your corporate IT perimeter. But that won't help in the web 2.0 era
From playlist O'Reilly Webcasts

DEFCON 16: Anti-RE Techniques in DRM Code
Speaker: Jan Newger, Security Researcher In order to prevent music from being copied among consumers, content providers often use DRM systems to protect their music files. This talk describes the approach taken while analysing a DRM system (whose identity needs to be kept secret due to le
From playlist DEFCON 16


