
CERIAS Security: Privacy and anonymity in Trust Negotiations 4/5
Clip 4/5 Speaker: Anna Squicciarini · University of Milano Trust negotiation is an emerging approach for establishing trust in open systems, where sensitive interactions may often occur between entities with no prior knowledge of each other. Although several proposals today exist of s
From playlist The CERIAS Security Seminars 2005 (1)

CERIAS Security: Privacy and anonymity in Trust Negotiations 3/5
Clip 3/5 Speaker: Anna Squicciarini · University of Milano Trust negotiation is an emerging approach for establishing trust in open systems, where sensitive interactions may often occur between entities with no prior knowledge of each other. Although several proposals today exist of s
From playlist The CERIAS Security Seminars 2005 (1)

CERIAS Security: Privacy and anonymity in Trust Negotiations 5/5
Clip 5/5 Speaker: Anna Squicciarini · University of Milano Trust negotiation is an emerging approach for establishing trust in open systems, where sensitive interactions may often occur between entities with no prior knowledge of each other. Although several proposals today exist of s
From playlist The CERIAS Security Seminars 2005 (1)

CERIAS Security: Privacy and anonymity in Trust Negotiations 1/5
Clip 1/5 Speaker: Anna Squicciarini · University of Milano Trust negotiation is an emerging approach for establishing trust in open systems, where sensitive interactions may often occur between entities with no prior knowledge of each other. Although several proposals today exist of s
From playlist The CERIAS Security Seminars 2005 (1)

CERIAS Security: Privacy and anonymity in Trust Negotiations 2/5
Clip 2/5 Speaker: Anna Squicciarini · University of Milano Trust negotiation is an emerging approach for establishing trust in open systems, where sensitive interactions may often occur between entities with no prior knowledge of each other. Although several proposals today exist of s
From playlist The CERIAS Security Seminars 2005 (1)
CITRIX: Provisioning Services - Assigning vDisks to users
More videos like this on http://www.theurbanpenguin.com : In this short presentation we look at Citrix Provisioning Services and assigning vDisks to user groups.
From playlist Citrix

Citrix : Web Interface enabling HTTPS
More videos like this online at http://www.theurbanpenguin.com In this video we take a look at enabling HTTPS access with SSL to the WebInterface Server. With the later Citrix Receivers HTTPS is becoming the Protocol of choice and certainly when used with the Citrix Access Gateway we shoul
From playlist Citrix

RSA Conference USA 2010: Will the Internet Ever Be Secure? Not Without Trust 1/3
Clip 1/3 Speaker: James Bidzos, Executive Chairman, VeriSign, Inc. Technologies and policies are important, but the future of Internet security rests upon trust. Without trust, people and organizations wont freely share information or purchase online. VeriSign has been building trust
From playlist RSA Conference USA 2010

DeepSec 2011: Do They Deliver? - Practical Security and Load Testing of Cloud Service Providers
Speaker: Matthias Luft | Enno Rey Matthias Luft talks at the DeepSec 2011 conference about cloud service providers and cloud security: The rapid evolution of cloud based computing is often used to illustrate a possible paradigm shift in computing. The centralized processing and storing
From playlist DeepSec 2011

RSA Conference USA 2010: Will the Internet Ever Be Secure? Not Without Trust 2/3
Clip 2/3 Speaker: James Bidzos, Executive Chairman, VeriSign, Inc. Technologies and policies are important, but the future of Internet security rests upon trust. Without trust, people and organizations wont freely share information or purchase online. VeriSign has been building trust
From playlist RSA Conference USA 2010

CERIAS Security: Thoughts on the Pervasive Trust Foundation for the Future Internet Architecture 3/5
Clip 3/5 Speaker: Leszek Lilien · Western Michigan University We start with presenting motivation and goals for the Future Internet, and reviewing basics of trust in computing. The Pervasive Trust Foundation (PTF) for the Future Internet is proposed next. This includes presenting motiva
From playlist The CERIAS Security Seminars 2009
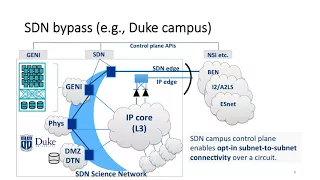
Trusted CI webinar: Toward Security-Managed Virtual Science Networks
Originally recorded April 23rd 2018 Data-intensive science collaborations increasingly provision dedicated network circuits to share and exchange datasets securely at high speed, leveraging national-footprint research fabrics such as ESnet or I2/AL2S. This talk first gives an overview o
From playlist Center for Applied Cybersecurity Research (CACR)

CERIAS Security: PlugNPlay Trust for Embedded Communication Systems 5/6
Clip 5/6 Speaker: Raquel Hill · Indiana University Given the proliferation of malware, the integrity of embedded communication systems is becoming a growing concern. Recent compromises to systems such as ATMs and network switches and routers provide evidence of the potential security pro
From playlist The CERIAS Security Seminars 2009

Blockchain Technology Explained (2 Hour Course)
Blockchain Technology Course will cover: - Technology overview - Blockchain evolution - Decentralized web - Distributed organizations - Distributed ledger - Smart contracts - Distributed applications - Internet of value - Token economies **** INTERESTED IN THE STOCK MARKET? I developed a
From playlist Blockchain

Trusted CI Webinar: SCI Trust Framework with David Kelsey
Originally recorded September 24, 2018 Slides: http://hdl.handle.net/2142/101446 E-Infrastructures recognise that controlling information security is crucial for providing continuous and trustworthy services for their user communities. Such infrastructures, including grids and clouds, ar
From playlist Center for Applied Cybersecurity Research (CACR)

Defining digital identities for humanitarian action in migration
Nadia Khoury, Humanitarian cash and migration consultant, IFRC Joseph Oliveros, Senior Officer, Cash Innovations, IFRC There is growing interest in the use of digital identities in providing services to migrants, and this research aims to help humanitarian organisations better understand
From playlist Turing trustworthy digital identity conference

[Title] Enterprise Blockchain Solutions for Financial Services: Techniques and Challenges [Presenter] Ziyuan Wang ,Swinburne University of Technology, Australia Donghai Liu ,Swinburne University of Technology, Australia Yang Xiang ,Swinburne University of Technology, Australia [Abstract]
From playlist IEEE ICBC Tutorial


