
OWASP AppSecUSA 2012: Interactive Application Security Testing(IAST), Beyond SAST/DAST
Speaker: Ofer Maor Until recently, SAST/DAST dominated the application security testing market, each with its own pros and cons. We present IAST, a completely new approach - analyzing code execution, memory and data in runtime, allowing for accurate inspection of the application. We will
From playlist OWASP AppSecUSA 2012

CERIAS Security: Static source code analysis 4/6
Clip 4/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008
CERIAS Security: Static source code analysis 2/6
Clip 2/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008

CERIAS Security: Static source code analysis 1/6
Clip 1/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008
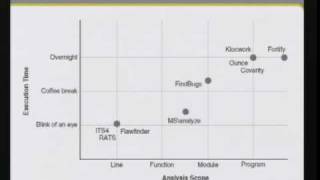
CERIAS Security: Static source code analysis 3/6
Clip 3/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008

CERIAS Security: Static source code analysis 5/6
Clip 5/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008

CERIAS Security: Static source code analysis 6/6
Clip 6/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008

CERIAS Security: Robustness testing - black-box testing for software security 6/6
Clip 6/6 Speaker: Ari Takanen · Codenomicon Ltd. The robustness testing method is based on systematic creation of a very large number of communication protocol messages containing exceptional data elements and structures simulating malicious attacks or corrupted traffic. The method pr
From playlist The CERIAS Security Seminars 2004

DEFCON 15: How I Learned to Stop Fuzzing and Find More Bugs
Speaker: Jacob West Manager, Security Research Group, Fortify Software Fuzzing and other runtime testing techniques are great at finding certain kinds of bugs. The trick is, effective fuzzing requires a lot of customization. The fuzzer needs to understand the protocol being spoken, antici
From playlist DEFCON 15

Application Security Tutorial | Application Security Basics | Cyber Security Tutorial | Simplilearn
In this application tutorial, we will cover application security basics in this cyber security tutorial. We will cover the basic definitions of application security, along with the different types and categories of application security. Next we cover the common application security vulnera
From playlist Cyber Security Playlist [2023 Updated]🔥

AppSec at DevOps Speed and Portfolio Scale - Jeff Williams
AppSec at DevOps Speed and Portfolio Scale - Jeff Williams Software development is moving much faster than application security with new platforms, languages, frameworks, paradigms, and methodologies like Agile and Devops. Unfortunately, software assurance hasn't kept up with the times.
From playlist AppSecUSA 2013

RailsConf 2019 - No Such Thing as a Secure Application by Lyle Mullican
RailsConf 2019 - No Such Thing as a Secure Application by Lyle Mullican _______________________________________________________________________________________________ Cloud 66 - Pain Free Rails Deployments Cloud 66 for Rails acts like your in-house DevOps team to build, deploy and maint
From playlist RailsConf 2019

Application Security at DevOps Speed and portfolio scale - Jeff Williams
Software development is moving much faster than application security with new platforms, languages, frameworks, paradigms, and methodologies like Agile and Devops. Unfortunately, software assurance hasn't kept up with the times. For the most part, our security techniques were built to wor
From playlist AppSec California 2014

OWASP AppSecUSA 2012: Secure Code Reviews Magic or Art? A Simplified Approach to Secure Code Reviews
Speaker: Sherif Koussa Secure code review is one of the best ways to uncover vulnerabilities and reduce risk of online web applications being breached. However, secure code review has always been challenged as being skill and tools intensive. But what if this could be simplified so develo
From playlist OWASP AppSecUSA 2012

Cyber Security Interview Questions Part - 2 | Software Programming Interview Questions | Simplilearn
This video on cybersecurity interview questions part 2 will focus on software and programming questions. Here, we will look at questions related to use-case testing, C, C++, Java, static and dynamic testing, and many more. 🔥Enroll for Free Cyber Security Course & Get Your Completion Certif
From playlist Cyber Security Playlist [2023 Updated]🔥

OWASP AppSecUSA 2012: Using Interactive Static Analysis for Detection of Software Vulnerabilities
Speaker: Bill Chu We present our work of using interactive static analysis to improve upon static analysis techniques by introducing a new mixed-initiative paradigm for interacting with developers to aid in the detection and prevention of security vulnerabilities. The key difference betwe
From playlist OWASP AppSecUSA 2012

DevOpsDays Boston 2019 - DevSecOps - Automating Security in DevOps by Anand Tiwari
DevSecOps - Automating Security in DevOps by Anand Tiwari As part of this workshop attendees will receive a state-of-the-art DevSecOps tool-chest comprising of various open-source tools and scripts to help the DevOps engineers in automating security within the CI/CD pipeline. While the wo
From playlist DevOpsDays Boston 2019

CERIAS Security: Robustness testing - black-box testing for software security 4/6
Clip 4/6 Speaker: Ari Takanen · Codenomicon Ltd. The robustness testing method is based on systematic creation of a very large number of communication protocol messages containing exceptional data elements and structures simulating malicious attacks or corrupted traffic. The method pr
From playlist The CERIAS Security Seminars 2004