
An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet
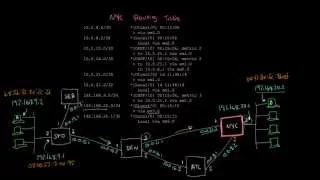
Hop-by-hop routing | Networking tutorial (11 of 13)
A closer look at the IP header and how IP packets are routed hop by hop. Support me on Patreon: https://www.patreon.com/beneater This video is part 11 of an intro to networking tutorial: https://www.youtube.com/playlist?list=PLowKtXNTBypH19whXTVoG3oKSuOcw_XeW
From playlist Networking tutorial

In this video, you’ll learn about how links function in HTML. We hope you enjoy! To learn more, check out our Basic HTML tutorial here: https://edu.gcfglobal.org/en/basic-html/ #html #links #coding
From playlist HTML

Introduction to TCP/IP and Sockets, part 1: Introducing the protocols and API
This is a basic introduction to the Internet protocols and how to use them in programs using sockets. This is the first of two introduction videos on the Internet Protocol and its family of associated protocols (UDP, TCP, etc.) as well as Sockets, a pseudo-standard interface made for prog
From playlist Introduction to TCP/IP and Sockets

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet
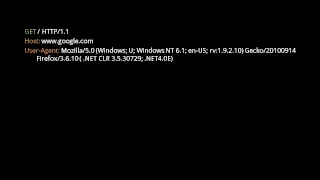
An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

Internet Tips: Understanding URLs
In this video, you’ll learn more about how URLs work. Visit https://www.gcflearnfree.org/internetbasics/understanding-urls/1/ for our text-based lesson. This video includes information on: • The basic parts of a URL, including the scheme, domain name, file path, parameters, and anchor We
From playlist Internet Tips

Bitcoin Q&A: What is Rendezvous Routing?
What is rendezvous routing? Has the Lightning Network "figured out" routing yet? How far along is it in development? More about rendezvous routing: https://www.mail-archive.com/lightning-dev@lists.linuxfoundation.org/msg00761.html Chapters 0:00 What is rendezvous routing in Lightning? Ho
From playlist English Subtitles - aantonop Videos with subtitles in English
Distance Vector Routing Algorithm In Computer Networks | DV Routing Algorithm | Simplilearn
In this video on 'Distance Vector Routing', we will understand how the network chooses the best and the smallest path for transmitting data packets over the channel. This task is performed by using the Bellman-Ford Algorithm and designing a proper protocol to follow for smooth transmission
From playlist Networking

Bitcoin Q&A: Misconceptions about Lightning Network
What are some misconceptions about the Lightning Network? How does the onion-routing work? How does channel funding work? Are there any security or legal risks to running a Lightning node? How far is the user experience development? Chapters 0:00 Have you seen the video how banks bought b
From playlist English Subtitles - aantonop Videos with subtitles in English

Bitcoin Q&A: Lightning Network Scaling
What is the capacity difference between utilizing second layers, like the Lightning Network, and block size increases? Are hard forks harder to execute with the existence of second layers? BCH supporters say that the Lightning Network will not be able to scale, remain decentralised, or be
From playlist English Subtitles - aantonop Videos with subtitles in English

CERIAS Security: Clouseau: A IP spoofing defense through route-based filtering 1/6
Clip 1/6 Speaker: Jelena Mirkovic · University of Delaware IP spoofing accompanies many malicious activities and is even means for performing reflector DDoS attacks. Route-based filtering (RBF) enables a router to filter spoofed packets based on their incoming interface - this informa
From playlist The CERIAS Security Seminars 2005 (2)

Build an Event Calendar App Using NodeJS, VueJS, and SQL Server (Step by Step Tutorial)
In this tutorial, you will learn the basics of creating a secure Node.js web application and API using Microsoft SQL Server by creating a simple calendar events application. These same architecture and approach in this tutorial could be applied to any basic "Create, Read, Update, and Delet
From playlist NodeJS

CERIAS Security: Spoofing-resistant Packet Routing for the Internet 3/6
Clip 3/6 Speaker: Minaxi Gupta · Indiana University The forgery of source IP addresses, called IP spoofing, is commonly exploited to launch damaging denial-of-service (DoS) attacks in the Internet. Currently proposed spoofing prevention approaches either focus on protecting only the t
From playlist The CERIAS Security Seminars 2006

Understanding Routing! | ICT#8
The amazing journey of data packets from a data center to your device forms the backbone of the Internet. This data flow is governed to make the most efficient transfer of the data. It is apparent from this animation that this governing of the data, from the source to the destination, thro
From playlist Internet & Telecommunication Technology

CERIAS Security: Spoofing-resistant Packet Routing for the Internet 5/6
Clip 5/6 Speaker: Minaxi Gupta · Indiana University The forgery of source IP addresses, called IP spoofing, is commonly exploited to launch damaging denial-of-service (DoS) attacks in the Internet. Currently proposed spoofing prevention approaches either focus on protecting only the t
From playlist The CERIAS Security Seminars 2006

Introduction to TCP/IP and Sockets, part 2: Example code Walk-Through
This is a walk-through of example C++ code for using Sockets to send and receive messages between programs using the Internet protocols. This is part 2 of the series. Part 1 is here: https://youtu.be/C7CpfL1p6y0 Here is a link to all the code: https://github.com/rhymu8354/SocketTutori
From playlist Introduction to TCP/IP and Sockets

OSB 2015 - Build a Web Map with Open Source Tools - Lyzi Diamond
Come learn to make a map on the web! In this tutorial, we will build an interactive, data-filled web map using a number of open source tools including Mapbox.js (a JavaScript library based on Leaflet.js). We will cover several options for interactivity and data sources, and show how to int
From playlist Open Source Bridge 2015

