
WebAssembly: The What, Why and How
WebAssembly is a portable, size, and load-time efficient binary format for the web. It is an emerging standard being developed in the WebAssembly community group, and supported by multiple browser vendors. This talk details what WebAssembly is, the problems it is trying to solve, exciting
From playlist Talks

A beat is an interference pattern between two sounds of slightly different in frequencies You can download this app or a similar app on two devices and TRY it at home Enjoy!!!
From playlist Beats

In this video, you’ll learn about how links function in HTML. We hope you enjoy! To learn more, check out our Basic HTML tutorial here: https://edu.gcfglobal.org/en/basic-html/ #html #links #coding
From playlist HTML

Amazing science experiment-Demonstrating beat frequency
A beat is an interference pattern between two sounds of slightly different in frequencies You can download this app or a similar app on two devices and TRY it at home Enjoy!!!
From playlist Beats

Amazing science experiment-Demonstrating beat frequency
A beat is an interference pattern between two sounds of slightly different in frequencies You can download this app or a similar app on two devices and TRY it at home Enjoy!!!
From playlist Beats

NOTACON 5: Lock Picking into the New Frontier: From Mechanical to Electronic Locks
Speaker: dosman We will start with a brief introduction to demonstrated lock picking fundamentals moving quickly towards how more advanced mechanical locks operate. Several high security cutaway locks will be shown with their additional security features explained in full view. We will th
From playlist Notacon 5

More videos like this online at http://www.theurbanpenguin.com We now look at how we can use and define methods in ruby to help keep the code tidy and concise. This also helps with readability of the code and later maintenance. In the example we use we take the decimal to ip address conver
From playlist RUBY

DEFCON 15: OpenBSD remote Exploit and another IPv6 vulnerabilities
Speaker: Alfredo Ortega Core Security OpenBSD is regarded as a very secure Operating System. This article details one of the few remote exploit against this system. A kernel shellcode is described, that disables the protections of the OS and installs a user-mode process. Several other pos
From playlist DEFCON 15

Greg Shackles interviewed at TOC 2012
Greg Shackles (MobileDevelpment with C#)
From playlist TOC 2012
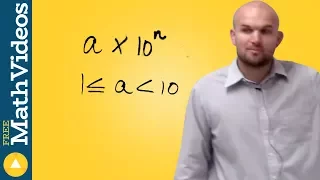
What is the definition of scientific notation
👉 Learn about scientific notations. Scientific notation is a convenient way of writing very large or very small numbers. A number written in scientific notation is of the form a * 10^n where a is the first non-zero number between 1 and 10, (1 included) and n is the number of digits up to t
From playlist Scientific Notation | Learn About

The Search for History’s Lost Slave Ships | Podcast | Overheard at National Geographic
On the bottom of the world’s oceans lie historic treasures—the lost wrecks of ships that carried enslaved people from Africa to the Americas. Only a handful have been identified so far, but National Geographic explorer and Storytelling Fellow Tara Roberts is documenting the efforts of Blac
From playlist Podcast | Overheard at National Geographic

The C programming language (unit 2) - 4 of 5 (old version; watch new version instead)
A continuation of discussing the C programming language. This unit goes more into depths on pointers and arrays. Visit http://codeschool.org
From playlist The C language (unit 2)

Obóz koncentracyjny Majdanek (KL Lublin) w 1979 roku
Obóz koncentracyjny w Majdanku (KL Lublin) oraz jego okolice na materiale filmowym z 1979 roku. Film pokazuje rozległe terenu obozu jenieckiego w Majdanku (oficjalnie nazywał się KL Lublin), krematoria, komory gazowe, zasieki czy wieże strażnicze. Przez obóz w Majdanku przewinęło się okoł
From playlist Claude Lanzmann "Shoah" - materiały filmowe powstałe podczas realizacji zdjęć do filmu

Solving the IMPOSSIBLE REVENGE Lock Puzzle!! Level 10!
Stock X Giveaway:https://www.instagram.com/p/Blqdw98H62l/?taken-by=chrisramsay52 Follow Stock X: https://www.instagram.com/stockx/ Today I'm going to attempt to solve the level 10 Revenge Lock Puzzle, otherwise known as the Wanderer. This puzzle lock is the latest puzzle released by Wil
From playlist Puzzles!

Scripting vs Programming :Major Difference Between Scripting And Programming | #Shorts | Simplilearn
🔥Explore Our Free Courses With Completion Certificate by SkillUp: https://www.simplilearn.com/skillup-free-online-courses?utm_campaign=ScriptingvsProgramming&utm_medium=ShortsDescription&utm_source=youtube A scripting language is a computer language that does not require compilation and i
From playlist #Shorts | #Simplilearn

DEFCON 19: DIY Non-Destructive Entry
Speaker: Schuyler Towne Competitive Lockpicker Ever leave the house without your picks only to find yourself in a situation where you desperately need them? Well, never fear! I'm going to explain how to open everything from cars, to briefcases to safes with objects as common as popsicle s
From playlist DEFCON 19

Grigori Rasputin - The Mad Monk - Extra History - #1
Use code EXTRACREDITS to get 40% off any annual membership for World Anvil and start hammering out the worlds you wanna see in your games! https://www.worldanvil.com/extracredits Oh boy another figure in history steeped in more myth and legend than anything else huh? Who exactly was the M
From playlist Extra History: Chronological Order (1700 CE - Present)

Go to https://NordVPN.com/thehistoryguy to get a 2-year plan at a huge discount plus 4 months free. It’s risk free with Nord’s 30 day money-back guarantee! For every Butch Cassidy or Billy the Kid, there were dozens of other criminals who never gained enough notoriety to become famous, li
From playlist Wild West

History of Mathematics Project: Learning Journeys for Kids and Others
New Learning Journeys created exclusively for the History of Mathematics Project (www.history-of-mathematics.org) connect and explore mathematical ideas across cultures and time. These journeys also help clarify meanings to some key developments in mathematics. The extensive computational
From playlist Wolfram Technology Conference 2021

This video is a brief introduction to linear codes: dimensions, G (generating matrix), H (parity check matrix), their forms. Also gives an example of how to convert between G and H. Here is the formal definition of a Linear Code: A linear code of dimension k and length n over a field
From playlist Cryptography and Coding Theory