If you are interested in learning more about this topic, please visit http://www.gcflearnfree.org/ to view the entire tutorial on our website. It includes instructional text, informational graphics, examples, and even interactives for you to practice and apply what you've learned.
From playlist The Internet

How can I keep all my smart devices secure?
Keep those programmable “smart” devices like toasters and light bulbs around your home from being coopted for nefarious activities by choosing and maintaining devices with security in mind.
From playlist Internet Safety

What is a Protective Put? Options Trading Strategies
These classes are all based on the book Trading and Pricing Financial Derivatives, available on Amazon at this link. https://amzn.to/2WIoAL0 Check out our website http://www.onfinance.org/ Follow Patrick on twitter here: https://twitter.com/PatrickEBoyle What is a Protective Put? A pr
From playlist Class 2: An Introduction to Options

This video explains what a hazard, risk and near miss are and what you should do if an incident occurs at UNSW.
From playlist UNSW Safety

Fundamental concepts of IPSec are discussed. Authentication Header is explained. ESP & IKE are analyzed.
From playlist Network Security

What is Neural Network Verification?
Neural networks can do some pretty amazing things, but if we want to use them in safety-critical applications, we need to verify their performance.
From playlist Summer of Math Exposition Youtube Videos

OWASP AppSec USA 2010: Keynote: Chenxi Wang 2/2
Speaker: Chenxi Wang More information can be found on the OWASP website: http://bit.ly/hY4bqh Source: http://bit.ly/owasp_appsec_us_2010
From playlist OWASP AppSec USA 2010
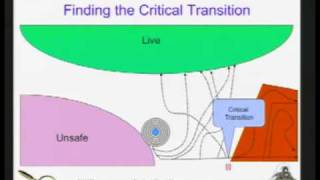
CERIAS Security: Mace: Systems and Language for Building Networked Services 4/5
Clip 4/5 Speaker: Charles Killian · Purdue University Building distributed systems is particularly difficult because of the asynchronous, heterogeneous, and failure-prone environment where these systems must run. This asynchrony makes verifying the correctness of systems implementations
From playlist The CERIAS Security Seminars 2009

Type systems are becoming increasingly popular in the javascript community with leading projects increasingly adopting flow and typescript. Another awesome development in the javascript space has been the rise of css-in-js frameworks. This talk is a deep dive into the challenges and oppo
From playlist Talks

Stanford Seminar - Safety (and Liveness!) of Robot Behaviors
Hadas Kress- Gazit, Professor Sibley School of Mechanical and Aerospace Engineering, College of Engineering - Princeton April 27, 2022 In this talk I will describe how formal methods such as synthesis – automatically creating a system from a formal specification – can be leveraged to desi
From playlist Stanford CS521 - AI Safety Seminar

AI Safety - Elliot Catt on Mathematical approaches to AGI Safety
The AI Safety seminar hosts weekly discussions of readings on technical and philosophical topics in AI safety. This week Elliot Catt joins us from DeepMind, to give an introduction to the role of mathematics in AGI Safety. He covers the following approaches to safety: - Universal AI and A
From playlist AI Safety seminar

OWASP AppSec 2010: (New) Object Capabilities and Isolation of Untrusted Web Applications 2/3
Clip 2/3 Speaker: Sergio Maffeis, Imperial College, London The object-capability model provides an appealing approach for isolating untrusted content in mashups: if untrusted applications are provided disjoint capabilities they still can interact with the user or the hosting page, but
From playlist OWASP AppSec 2010

http://www.365computersecuritytraining.com This video is an excerpt from our online training in computer security. It Covers some of the basic terminology used in the information technology security profession. Some of the terms covered are: Vulnerability, Threats, Assets, Risk...and
From playlist awareness

How to Debug a Property Proving Counterexample
Property proving with Simulink Design Verifier™ is a static analysis technique that uses formal methods to prove whether a given property will always be valid. This technique can help you formally verify that specific requirements implemented in your design will always be met. If a propert
From playlist Embedded Systems | Developer Tech Showcase

A Case for Oxidation: The Rust Programming Language
For almost five decades, we've built core systems software in unsafe languages like C or C++. Four of these decades can be excused as no alternative existed that matched these languages in performance and control. In the last decade, however, Rust, a programming language sponsored by Mozil
From playlist Rust

Network Security, Part 1 : Basic Encryption Techniques
Fundamental concepts of network security are discussed. It provides a good overview of secret Key and public key Encryption. Important data encryption standards are presented.
From playlist Network Security

CERIAS Security: Mace: Systems and Language for Building Networked Services 3/5
Clip 3/5 Speaker: Charles Killian · Purdue University Building distributed systems is particularly difficult because of the asynchronous, heterogeneous, and failure-prone environment where these systems must run. This asynchrony makes verifying the correctness of systems implementations
From playlist The CERIAS Security Seminars 2009