
If you are interested in learning more about this topic, please visit http://www.gcflearnfree.org/ to view the entire tutorial on our website. It includes instructional text, informational graphics, examples, and even interactives for you to practice and apply what you've learned.
From playlist The Internet

How can I keep all my smart devices secure?
Keep those programmable “smart” devices like toasters and light bulbs around your home from being coopted for nefarious activities by choosing and maintaining devices with security in mind.
From playlist Internet Safety

Lots of gun safety advocates focus on regulating the sale and transfer of firearms. Another area that could yield gains is gun storage. How safely weapons are stored is a big factor, especially when it comes to keeping kids safe. Secure storage and locks can do a lot. Related HCT episodes
From playlist Healthcare Triage

Staysafe.org: Protect your computer
The Internet is a global network that connects us to limitless information and opportunities. But there are risks involved with connecting to the Internet, such as downloading viruses and spyware onto computers and devices. Watch this video for four easy steps to help protect your computer
From playlist awareness

Fundamental concepts of IPSec are discussed. Authentication Header is explained. ESP & IKE are analyzed.
From playlist Network Security

Is renewable energy really sustainable?
Renewable energy is described as replenishable, safe for the environment, and available in the long term. But do all renewable energy sources meet these criteria? Watch to find out. Find out more information at https://bit.ly/3p0Thsz To get the latest science and technology news, su
From playlist Theory to Reality
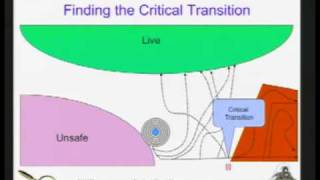
CERIAS Security: Mace: Systems and Language for Building Networked Services 4/5
Clip 4/5 Speaker: Charles Killian · Purdue University Building distributed systems is particularly difficult because of the asynchronous, heterogeneous, and failure-prone environment where these systems must run. This asynchrony makes verifying the correctness of systems implementations
From playlist The CERIAS Security Seminars 2009

OWASP AppSec USA 2010: Keynote: Chenxi Wang 2/2
Speaker: Chenxi Wang More information can be found on the OWASP website: http://bit.ly/hY4bqh Source: http://bit.ly/owasp_appsec_us_2010
From playlist OWASP AppSec USA 2010

Stanford Seminar - Safety (and Liveness!) of Robot Behaviors
Hadas Kress- Gazit, Professor Sibley School of Mechanical and Aerospace Engineering, College of Engineering - Princeton April 27, 2022 In this talk I will describe how formal methods such as synthesis – automatically creating a system from a formal specification – can be leveraged to desi
From playlist Stanford CS521 - AI Safety Seminar

Missouri Government and Politics: Lecture 16 - Local Government
This course is designed to familiarize students with the constitutional framework and institutions of the state of Missouri, including the legislative, executive, and judiciary branches, and its political parties. Missouri's inherent conservatism and individualism is explored in the fram
From playlist Missouri State: PLS 103: Missouri Government | CosmoLearning Political Science

Transport Layer Security: Part 1
Fundamental concepts of TLS are discussed. SSL is analyzed. HTTPS & SSH are presented.
From playlist Network Security

CERIAS Security: Mace: Systems and Language for Building Networked Services 3/5
Clip 3/5 Speaker: Charles Killian · Purdue University Building distributed systems is particularly difficult because of the asynchronous, heterogeneous, and failure-prone environment where these systems must run. This asynchrony makes verifying the correctness of systems implementations
From playlist The CERIAS Security Seminars 2009

CERIAS Security: Mace: Systems and Language for Building Networked Services 5/5
Clip 5/5 Speaker: Charles Killian · Purdue University Building distributed systems is particularly difficult because of the asynchronous, heterogeneous, and failure-prone environment where these systems must run. This asynchrony makes verifying the correctness of systems implementations
From playlist The CERIAS Security Seminars 2009

Vibrational properties in the continuum limit of amorphous solids by Hideyuki Mizuno
PROGRAM ENTROPY, INFORMATION AND ORDER IN SOFT MATTER ORGANIZERS: Bulbul Chakraborty, Pinaki Chaudhuri, Chandan Dasgupta, Marjolein Dijkstra, Smarajit Karmakar, Vijaykumar Krishnamurthy, Jorge Kurchan, Madan Rao, Srikanth Sastry and Francesco Sciortino DATE: 27 August 2018 to 02 Novemb
From playlist Entropy, Information and Order in Soft Matter

OWASP AppSec 2010: (New) Object Capabilities and Isolation of Untrusted Web Applications 2/3
Clip 2/3 Speaker: Sergio Maffeis, Imperial College, London The object-capability model provides an appealing approach for isolating untrusted content in mashups: if untrusted applications are provided disjoint capabilities they still can interact with the user or the hosting page, but
From playlist OWASP AppSec 2010

Ruby|Web Conference 2010 - The 7 Habits of Highly Successful Samurai, and How That Helps Rubyists
By Alistair Cockburn The Crystal 3-step model consists of practices, principles, and personalization. The practices are what you know or learn how to do. The principles are the laws of design that inform you as to what works better, when. Personalization is adapting yourself to your situat
From playlist Ruby|Web Conference 2010

Network Security, Part 1 : Basic Encryption Techniques
Fundamental concepts of network security are discussed. It provides a good overview of secret Key and public key Encryption. Important data encryption standards are presented.
From playlist Network Security

Best Smart Home Tech 2020 for Safety, Security, and Health
Best Smart Home Tech 2020 for Safety, Security, and Health Review. Go to https://brilliant.org/Undecided you can sign up for free. And also, the first 200 people will get 20% off their annual premium membership. If you're into sustainability, EVs, and renewable energy, there are some re
From playlist Smart Home Reviews

Is Alec Baldwin Going to Jail for the Death of Halyna Hutchins?
⭐️ Get my videos early & ad free (plus my exclusives!) only on Nebula. Save $10 per year! https://legaleagle.link/getnebula ⭐️ Shootings on set shouldn't happen. What happened here and who is going to pay for it? 🚀For a LIMITED TIME get CuriosityStream AND Nebula for 26% OFF! https://lega
From playlist Law Review News!
