
An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Cryptographic Hash Functions: Part 1
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

Cryptographic Hash Functions: Part 2
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

From playlist Cryptography Lectures

Day 2 Talks: JAX, Flax & Transformers 🤗
Day 2 Talks: JAX, Flax & Transformers 🤗 0:00:00 Suraj Patil & Patrick von Platen (Hugging Face): How to use JAX/Flax with Transformers 0:26:16 Sabrina J. Mielke (Johns Hopkins University & Hugging Face): From stateful code to purified JAX: how to build your neural net framework 1:01:35 Mos
From playlist Partnerships and Guest Talks

From playlist Cryptography Lectures

Aprender li lingue international Occidental (Interlingue) con Salute, Jonathan! - un cursu scrit completmen in Occidental. Learn the international language Occidental (Interlingue) with Salute, Jonathan! - a course written completely in Occidental. https://en.wikibooks.org/wiki/Salute,_J
From playlist Salute, Jonathan! Learn the Occidental language using the natural method

Lecture 8.1 — A brief overview of Hessian-free optimization [Neural Networks for Machine Learning]
Lecture from the course Neural Networks for Machine Learning, as taught by Geoffrey Hinton (University of Toronto) on Coursera in 2012. Link to the course (login required): https://class.coursera.org/neuralnets-2012-001
From playlist [Coursera] Neural Networks for Machine Learning — Geoffrey Hinton

Stanford Seminar - The Future of Wireless Communications Hint: It's not a linear amplifier
Speaker: Douglas Kirkpatrick, Eridan Communications Wireless communications are ubiquitous in the 21 st century--we use them to read the newspaper, talk to our colleagues or children, watch sporting events or other forms of entertainment, and to monitor and control the environment we live
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series

Uri Onn: Base change and representation growth of arithmetic groups
SMRI Seminar: Uri Onn (Australian National University) Abstract: A group is said to have polynomial representation growth if the sequence enumerating the isomorphism classes of finite dimensional irreducible representations according to their dimension is polynomially bounded. The repres
From playlist SMRI Seminars

Hash Tables and Hash Functions
This computer science video describes the fundamental principles of the hash table data structure which allows for very fast insertion and retrieval of data. It covers commonly used hash algorithms for numeric and alphanumeric keys and summarises the objectives of a good hash function. Co
From playlist Data Structures

Oscillating Boundary problems (Lecture 3) by Antonio Gaudiello
PROGRAM: MULTI-SCALE ANALYSIS AND THEORY OF HOMOGENIZATION ORGANIZERS: Patrizia Donato, Editha Jose, Akambadath Nandakumaran and Daniel Onofrei DATE: 26 August 2019 to 06 September 2019 VENUE: Madhava Lecture Hall, ICTS, Bangalore Homogenization is a mathematical procedure to understa
From playlist Multi-scale Analysis And Theory Of Homogenization 2019

How to Create a WordPress Mega Menu from Scratch - Part 4
How to Create a WordPress Mega Menu from Scratch - Part 4 Download APWS: https://github.com/Alecaddd/awps Download Walker Nav Class: https://github.com/Alecaddd/WordPress-MegaMenu :: Become a Patreon :: https://www.patreon.com/alecaddd :: Join the Forum :: https://forum.alecaddd.com/ ::
From playlist Create a WordPress Mega Menu from Scratch

0:00-4:15 - A conceptual overview of hash functions and their requirements. 4:15-end - Hash functions in digital signatures use. For review on how RSA signatures work, see: https://www.youtube.com/watch?v=DIfOvWymmP0 Questions? Feel free to post them in the comments and I'll do my best t
From playlist Cryptography and Coding Theory

Conversational Question-Answering System for Aircraft Pilots' Documentation | L3-AI 2021
The aerospace industry relies on massive collections of complex and technical documents covering system descriptions, manuals, or procedures. This talk focuses on a question answering (QA) system that was built to help aircraft pilots access information in this documentation by naturally i
From playlist Level 3 AI Assistant Conference 2021

https://en.wikipedia.org/wiki/SHA-1#Examples_and_pseudocode If you have any questions of want to contribute to code or videos, feel free to write me a message on youtube or get my contact in the About section or googling my contacts.
From playlist Programming
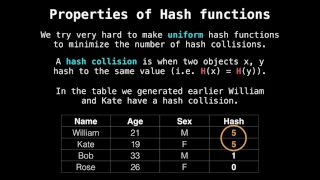
Related Videos: Hash table intro/hash function: https://www.youtube.com/watch?v=2E54GqF0H4s Hash table separate chaining: https://www.youtube.com/watch?v=T9gct6Dx-jo Hash table separate chaining code: https://www.youtube.com/watch?v=Av9kwXkuQFw Hash table open addressing: https://www.youtu
From playlist Data structures playlist

