
Verifying Trigonometric Identities: The Fundamental Identities
Visit http://mathispower4u.wordpress.com/ for a categorized and searchable list of all videos.
From playlist Reciprocal, Quotient, Negative, and Pythagorean Trigonometric Identities
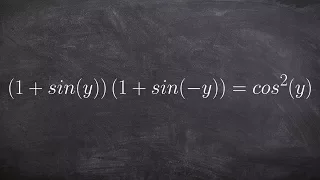
Verifying a trigonometric Identities
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities
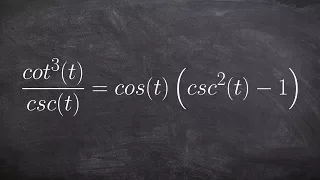
Verifying a trigonometric Identities
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

What are the different ways to perform data validation in machine learning?
#machinelearning #shorts #datascience
From playlist Quick Machine Learning Concepts

Verifying an identify by expanding an expression
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

Kernel Recipes 2019 - Formal modeling made easy
Modeling parts of Linux has become a recurring topic. For instance, the memory model, the model for PREEMPT_RT synchronization, and so on. But the term “formal model” causes panic for most of the developers. Mainly because of the complex notations and reasoning that involves formal languag
From playlist Kernel Recipes 2019

Verifying an identity by multiplying
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities
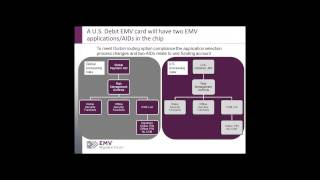
EMV 101: Fundamentals of EMV Chip Payment
Commonly used globally in place of magnetic stripe, EMV chip technology helps to reduce card fraud in a face-to-face card-present environment; provides global interoperability; and enables safer and smarter transactions across contact and contactless channels. EMV implementation was initia
From playlist Payments

Project Quality Management PMBOK® 6 | Project Quality Control | PMP® Training Videos | Edureka
( PMP® Training: https://www.edureka.co/pmp-certification-exam-training ) This Edureka tutorial on Project Quality Management will give you an insight into the various process and activities covered during Project development in order to maintain and manage the quality of a project. 1:47 -
From playlist PMP Certification Training Videos

OWASP AppSec EU 2013: New OWASP ASVS 2013
For more information and to download the video visit: http://bit.ly/appseceu13 Playlist OWASP AppSec EU 2013: http://bit.ly/plappseceu13 Speaker: Sahba Kazerooni We are excited to announce and share the next version of the OWASP Application Security Verification Standard (ASVS) project.
From playlist OWASP AppSec EU 2013

At-scale Formal Verification for Industrial Semiconductor Designs - Professor Tom Melham
https://www.turing-gateway.cam.ac.uk/sites/default/files/asset/doc/1707/Big%20Proof%20Day%20Melham%2019-07-2017.pdf #TuringSeminars
From playlist Turing Seminars

CGSR | Everything Counts: Building a Control Regime for Nonstrategic Nuclear Warheads in Europe
Featuring: Rose Gottemoeller, William M. Moon, Miles A. Pomper Abstract: This paper focuses on the negotiating, policy, legal, and technical issues that the U.S and allies will likely have to address to reach and implement an agreement with Russia on non-strategic nuclear warheads at the
From playlist Center for Global Security Research

Top 50 Software Testing Interview Questions & Answers | Software Testing Training | Edureka
** Test Automation Engineer Masters Program : https://www.edureka.co/masters-program/automation-testing-engineer-training ** This Edureka video on Top 50 Software Testing Interview Question and Answers will help you to prepare yourself for Software Testing Interviews. It covers questions f
From playlist Software Testing Training Videos | Edureka

How to verify a trigonometric identity
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

DEFCON 15: Comparing Application Security Tools
Speaker: Edward Lee Security Researcher, Fortify Software If you're going to buy an application security tool, which one will it be? Every vendor likes to talk about how their tools are the best. "We are the market leader!" they all say. But not everyone can lead all the time. I will show
From playlist DEFCON 15

Multiply and verify the trigonometric identity
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

Trigonometry: Verifying Identities
This is the fourth video of a series from the Worldwide Center of Mathematics explaining the basics of trigonometry. This video shows some of the trigonometric identities (NOTE: they are not proved here), and shows how to do verification problems. For more math videos, visit our channel or
From playlist Basics: Trigonometry

Safety and robustness for deep learning with provable guarantees - Marta Kwiatkowska - Oxford
Computing systems are becoming ever more complex, with automated decisions increasingly often based on deep learning components. A wide variety of applications are being developed, many of them safety-critical, such as self-driving cars and medical diagnosis. Since deep learning is unstabl
From playlist Interpretability, safety, and security in AI

Keynote Presentation: Framework for Developing Complex Systems
Get a Free Trial: https://goo.gl/C2Y9A5 Get Pricing Info: https://goo.gl/kDvGHt Ready to Buy: https://goo.gl/vsIeA5 Framework for Developing Complex Systems using Model-based design and Simulink.
From playlist MathWorks Automotive Conference 2013

Tutorial for verifying trigonometric identities
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities