
Pseudorandom Generators for Regular Branching Programs - Amir Yehudayoff
Amir Yehudayoff Institute for Advanced Study March 16, 2010 We shall discuss new pseudorandom generators for regular read-once branching programs of small width. A branching program is regular if the in-degree of every vertex in it is (either 0 or) 2. For every width d and length n, the p
From playlist Mathematics

Pseudorandom Generators for Read-Once ACC^0 - Srikanth Srinivasan
Srikanth Srinivasan DIMACS April 24, 2012 We consider the problem of constructing pseudorandom generators for read-once circuits. We give an explicit construction of a pseudorandom generator for the class of read-once constant depth circuits with unbounded fan-in AND, OR, NOT and generaliz
From playlist Mathematics

Pseudorandom Generators for CCO[p]CCO[p] and the Fourier Spectrum... - Shachar Lovett
Shachar Lovett Institute for Advanced Study October 5, 2010 We give a pseudorandom generator, with seed length O(logn)O(logn), for CC0[p]CC0[p], the class of constant-depth circuits with unbounded fan-in MODpMODp gates, for prime pp. More accurately, the seed length of our generator is O(
From playlist Mathematics

Pseudorandom Number Generation and Stream Ciphers
Fundamental concepts of Pseudorandom Number Generation are discussed. Pseudorandom Number Generation using a Block Cipher is explained. Stream Cipher & RC4 are presented.
From playlist Network Security

Better Pseudorandom Generators from Milder Pseudorandom Restrictions - Parikshit Gopalan
Parikshit Gopalan Microsoft Research Silicon Valley, Mountain View, CA April 3, 2012 We present an iterative approach to constructing pseudorandom generators, based on the repeated application of mild pseudorandom restrictions. We use this template to construct pseudorandom generators for
From playlist Mathematics

Avi Wigderson: Randomness and pseudorandomness
Abstract: The talk is aimed at a general audience, and no particular background will be assumed. Is the universe inherently deterministic or probabilistic? Perhaps more importantly - can we tell the difference between the two? Humanity has pondered the meaning and utility of randomness fo
From playlist Abel Lectures

Jonathan Katz - Introduction to Cryptography Part 1 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography I" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will serve as a "crash course" in modern cryptography for those with no prior exposure
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Pseudorandom number generators | Computer Science | Khan Academy
Random vs. Pseudorandom Number Generators Watch the next lesson: https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/the-fundamental-theorem-of-arithmetic-1?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Missed the previous lesson? https://www.k
From playlist Journey into cryptography | Computer Science | Khan Academy
Giray Ökten: Number sequences for simulation - lecture 1
After an overview of some approaches to define random sequences, we will discuss pseudorandom sequences and low-discrepancy sequences. Applications to numerical integration, Koksma-Hlawka inequality, and Niederreiter’s uniform point sets will be discussed. We will then present randomized q
From playlist Probability and Statistics
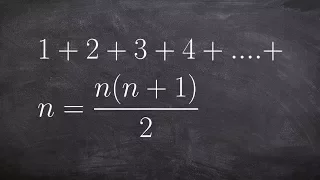
Learn how to use mathematical induction to prove a formula
👉 Learn how to apply induction to prove the sum formula for every term. Proof by induction is a mathematical proof technique. It is usually used to prove that a formula written in terms of n holds true for all natural numbers: 1, 2, 3, . . . To prove by induction, we first show that the f
From playlist Sequences

Using mathematical induction to prove a formula
👉 Learn how to apply induction to prove the sum formula for every term. Proof by induction is a mathematical proof technique. It is usually used to prove that a formula written in terms of n holds true for all natural numbers: 1, 2, 3, . . . To prove by induction, we first show that the f
From playlist Sequences

Interview Igor Shparlinski : Jean Morlet Chair (First Semester 2014)
Jean-Morlet Chair on 'Number Theory and its Applications to Cryptography' Beneficiaries : Jean-Morlet Chair : Igor SHPARLINSKI School of Mathematics and Statistics University of New South Wales Sydney, Australia igor.shparlinski@unsw.edu.au Local project leader : David KOHEL I2M - Insti
From playlist Jean-Morlet Chair's holders - Interviews

The Green-Tao theorem and a relative Szemeredi theorem - Yufei Zhao
Slides for this talk: https://drive.google.com/file/d/1RdgY6N869MN5lJwl2jv1HwIgWky6aW5C/view?usp=sharing The Green-Tao theorem and a relative Szemeredi theorem - Yufei Zhao Abstract: The celebrated Green-Tao theorem states that there are arbitrarily long arithmetic progressions in the p
From playlist Mathematics

Peter Sarnak - Substitution Sequences at Primes [2008]
Pseudorandomness in Mathematics & Computer Science Mini Workshop In math, one often studies random aspects of deterministic systems and structures. In CS, one often tries to efficiently create structures and systems with specific random-like properties. Recent work has shown many connecti
From playlist Number Theory

Giray Ökten: Derivative pricing, simulation from non-uniform distributions - lecture 3
The models of Bachelier and Samuelson will be introduced. Methods for generating number sequences from non-uniform distributions, such as inverse transformation and acceptance rejection, as well as generation of stochastic processes will be discussed. Applications to pricing options via re
From playlist Probability and Statistics

Jean Bourgain - Exponential sums, equidistribution and pseudo randomness [2008]
Pseudorandomness in Mathematics & Computer Science Mini Workshop In math, one often studies random aspects of deterministic systems and structures. In CS, one often tries to efficiently create structures and systems with specific random-like properties. Recent work has shown many connecti
From playlist Number Theory

Learn to use induction to prove the sum formula of a series
👉 Learn how to apply induction to prove the sum formula for every term. Proof by induction is a mathematical proof technique. It is usually used to prove that a formula written in terms of n holds true for all natural numbers: 1, 2, 3, . . . To prove by induction, we first show that the f
From playlist Sequences
24. Probabilistic Computation (cont.)
MIT 18.404J Theory of Computation, Fall 2020 Instructor: Michael Sipser View the complete course: https://ocw.mit.edu/18-404JF20 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP60_JNv2MmK3wkOt9syvfQWY Quickly reviewed last lecture. Simulated read-once branching programs
From playlist MIT 18.404J Theory of Computation, Fall 2020