An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

Transport Layer Security: Part 1
Fundamental concepts of TLS are discussed. SSL is analyzed. HTTPS & SSH are presented.
From playlist Network Security

Protocols - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Transport Layer Security: Part 2 - TLS & HTTPS
Fundamental concepts of TLS are discussed. SSL is analyzed. HTTPS & SSH are presented.
From playlist Network Security

Cryptocurrencies and Beyond - Aggelos Kiayias, Chief scientist IOHK.
Secure Decentralized Blockchains without Proofs of Work By Aggelos Kiayias, Chief scientist IOHK. A Provably Secure Proof-of-Stake Blockchain Protocol https://eprint.iacr.org/2016/889.pdf Contribute to pos-haskell-prototype development by creating an account on GitHub. https://github.co
From playlist Cryptocurrencies and Beyond Workshop

The nightmare future humanity avoided
The Montreal Protocol was designed to save the ozone layer, but it may have ended up saving the planet. Learn more about how the atmosphere absorbs radiation with Brilliant! https://www.brilliant.org/simonclark A new paper this year examined the "world avoided" via the Montreal Protocol,
From playlist Science videos

The BEST Way To Use Creatine For Muscle Growth (4 STEPS)
Creatine is an effective and safe supplement to help you build stronger and bigger muscles. But science also reveals that, when it comes to how to take creatine, there’s a specific way to use it (e.g., creatine before or after workout?) to maximize its benefits and save money while you’re
From playlist SUPPLEMENTS FOR MUSCLE GROWTH

PubHlth 194: Clinc Trans Rsrch-A. Lec 8: Biostatistics, Epidemiology and Research Design (BERD)
UCI PubHlth 194: Clinical and Translational Research Preparatory I (Fall 2012) Lec 08. Clinical and Translational Research Preparatory I -- Biostatistics, Epidemiology and Research Design (BERD) -- View the complete course: http://ocw.uci.edu/courses/pubhlth_194a_clinical_and_translational
From playlist PubHlth 194: Clinical & Translational Research Preparatory-A

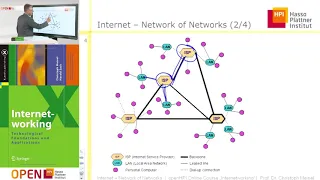
IP addresses and DNS | Internet 101 | Computer Science | Khan Academy
The co-founder of the Internet Vint Cerf and software engineer Paola Mejia take us through the ins and outs of how networks talk to each other. Watch the next lesson: https://www.khanacademy.org/computing/computer-science/internet-intro/internet-works-intro/v/the-internet-packet-routers-a
From playlist Internet 101 | Computer Science | Khan Academy

Stanford Seminar: The Time-Less Datacenter
EE3280: Colloquium on Computer Systems Seminar Series The Time-Less Datacenter Speakers: Paul Borrill and Alan Karp, EARTH Computing We describe, and demonstrate, a novel foundation for datacenter communication: a new "event based" protocol that can dispense with the need for conventi
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series

CS105: Introduction to Computers | 2021 | Lecture 6.1 Network Protocols: What is a Protocol
Patrick Young Computer Science, PhD This course is a survey of Internet technology and the basics of computer hardware. You will learn what computers are and how they work and gain practical experience in the development of websites and an introduction to programming. To follow along wi
From playlist Stanford CS105 - Introduction to Computers Full Course

Nexus trimester - Omri Weinstein (Courant Institute (NYU)) 3/6
Interactive Information Complexity and Applications : Interactive Compression - Part I/1 Omri Weinstein (Courant Institute (NYU)) February 08, 2016 Abstract: Communication complexity had a profound impact on nearly every field of theoretical computer science, and is one of the rare method
From playlist Nexus Trimester - 2016 - Distributed Computation and Communication Theme

Internet Technologies - CS50's Computer Science for Business Professionals 2017
00:00:00 - Introduction 00:00:49 - Protocols 00:02:04 - How the Internet Works 00:04:25 - DHCP 00:06:45 - DNS 00:10:51 - TCP 00:14:00 - UDP 00:15:37 - traceroute 00:18:53 - Undersea Cabling 00:21:36 - TCP/IP 00:25:01 - HTTP 00:33:52 - HTML This course is a variant of Harvard College's int
From playlist CS50's Computer Science for Business Professionals 2017

A Tutorial on Network Protocols
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Source Boston 2010: Cracking the Foundation: Attacking WCF Web Services 1/5
Clip 1/5 Speaker: Brian Holyfield, Gotham Digital Science Hacking a web service generally isn't rocket science. But what if the web service requires messages to be sent using a binary protocol? What if it requires message level encryption but you don't have a key? These are just a few com
From playlist SOURCE Boston 2010