What in the world is a linear program?
What is a linear program and why do we care? Today I’m going to introduce you to the exciting world of optimization, which is the mathematical field of maximizing or minimizing an objective function subject to constraints. The most fundamental topic in optimization is linear programming,
From playlist Summer of Math Exposition 2 videos

Network Analysis. Course introduction.
Introduction to the Social Network Analysis course.
From playlist Structural Analysis and Visualization of Networks.

What Software Architecture Should Look Like
What is Software Architecture? It’s a surprisingly difficult question to answer. We can describe software architecture patterns and argue about what is the best software architecture, but in reality, most definitions are vague enough to be unhelpful or so over the top to be more like a lis
From playlist Software Engineering

How To Estimate Software Development Time
"How to estimate software development time” is a perennial question that faces us all at some point in our career. How to manage software projects is a complex problem, there is a lot to understand, and there is a lot of misunderstanding about what is sensible and possible in software esti
From playlist Teamwork and Leadership

GTAC 2015: Test Suites and Program Analysis
http://g.co/gtac Slides: https://docs.google.com/presentation/d/1yoOf_fyeN-AtQQQsTemxrranKVBUc9i-VzF_o4OqsJQ/pub Patrick Lam (University of Waterloo) Specializing static analysis techniques for test suites has yielded interesting results. We've previously learned that most tests are simp
From playlist GTAC 2015

DEFCON 15: How I Learned to Stop Fuzzing and Find More Bugs
Speaker: Jacob West Manager, Security Research Group, Fortify Software Fuzzing and other runtime testing techniques are great at finding certain kinds of bugs. The trick is, effective fuzzing requires a lot of customization. The fuzzer needs to understand the protocol being spoken, antici
From playlist DEFCON 15

🔥Program Overview: The Reasons to Get Certified in Business Analysis in 2023 | Simplilearn
🔥Enoll to our Professional Certificate Program In Business Analysis: https://www.simplilearn.com/pgp-business-analysis-certification-training-course?utm_campaign=BusinessAnalyticsWebinar6April2023&utm_medium=DescriptionFF&utm_source=youtube About the Webinar As more of the world has shif
From playlist Simplilearn Live

Black Hat USA 2010: Crash Analysis Using BitBlaze 2/5
Speakers: Charlie Miller, Noah Johnson You've fuzzed your favorite application and found a mountain of crashes, now what? BitBlaze is an open source binary analysis platform which can perform whole system taint tracing, dynamic symbolic execution, as well as static analysis. Using BitBlaz
From playlist BH USA 2010 - REVERSE ENGI
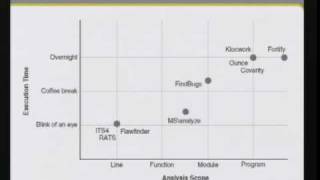
CERIAS Security: Static source code analysis 3/6
Clip 3/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008
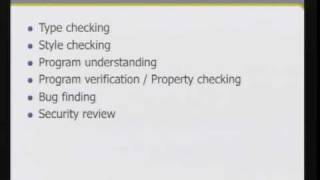
CERIAS Security: Static source code analysis 2/6
Clip 2/6 Speaker: Jacob West · Fortify Software Creating secure code requires more than just good intentions. Programmers need to know how to make their code safe in an almost infinite number of scenarios and configurations. Static source code analysis gives users the ability to review t
From playlist The CERIAS Security Seminars 2008

PMI-PgMP® Tutorial | Lesson 4: Program Strategy Alignment | Simplilearn
🔥Certified ScrumMaster® (CSM) Certification Training Course: https://www.simplilearn.com/agile-and-scrum/csm-certification-training?utm_campaign=PMIPGMP-F_xf5rwTMF0&utm_medium=DescriptionFF&utm_source=youtube 🔥Certified Scrum Product Owner (CSPO) Certification Training: https://www.simplil
From playlist PMI-PgMP® Certification Training Videos

Garrett Grolemund, author of the forthcoming "Data Analysis with R" discusses the benefits of using a programming language like R, instead of traditional data analysis software, for data analysis.
From playlist Programming Podcast
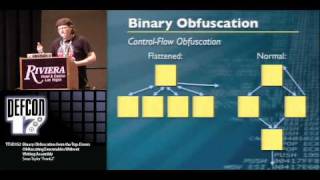
DEFCON 17: Binary Obfuscation from the Top-Down: Obfuscating Executables Without Writing Assembly
Speaker: Sean "Frank^2" Taylor Security Engineer, Rapid7 Binary obfuscation is commonly applied in malware and by software vendors in order to frustrate the efforts of reverse engineers to understand the underlying code. A common misconception is one must be a master of assembly in order
From playlist DEFCON 17