
What is Parity Check? | Parity Check Error Detection | Parity Check Matrix | Simplilearn
In this video on 'What Is Parity Check?', we will look into the working of the network method parity bit check, which uses redundant bits to perform the error check at the receiver side and uses even and the odd parity bit to perform the method. Topics covered in this video on 'What Is Pa
From playlist Networking

Background Checks and Criminal Records
In this video, you’ll learn more about how to respond to background checks when you have a criminal record. https://www.gcflearnfree.org/jobsearchandnetworking/getting-a-job-with-a-criminal-record/1/ for our text-based lesson. This video includes information on: • Elements of a background
From playlist The Search

Verifying Particular Solutions to Differential Equations Calculus 1 AB
I reintroduce Differential Equations including the definition of a differential equations, the order of differential equations, the difference between particular solutions and general solutions, and the number of arbitrary constants you can expect when solving these equations. I then work
From playlist Calculus

Can You Validate These Emails?
Email Validation is a procedure that verifies if an email address is deliverable and valid. Can you validate these emails?
From playlist Fun

From playlist Week 5 2013

Randomness - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

What Is Checksum Error Detection? | What Is Checksum And How It Works? | Simplilearn
"In this video on 'What Is Checksum?', we will look at one of the most applied error-detection methods of the network domain, the checksum method, along with details and the working steps of the checksum method. Topics covered in this video on 'What Is Checksum?' are as follows: 00:00:00
From playlist Networking
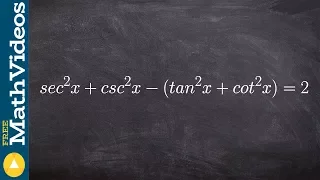
Distributing a negative to verify the identity
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

Checking Solutions in Differential Equations (Differential Equations 3)
https://www.patreon.com/ProfessorLeonard Determining whether or not an equation is a solution to a Differential Equation.
From playlist Differential Equations

Black Hat USA 2010: Crash Analysis Using BitBlaze 2/5
Speakers: Charlie Miller, Noah Johnson You've fuzzed your favorite application and found a mountain of crashes, now what? BitBlaze is an open source binary analysis platform which can perform whole system taint tracing, dynamic symbolic execution, as well as static analysis. Using BitBlaz
From playlist BH USA 2010 - REVERSE ENGI

CERIAS Security: OS-Level Taint Analysis for Malware Investigation and Defense 6/6
Clip 6/6 Speaker: Dongyan Xu · Purdue University The Internet is facing threats from increasingly stealthy and sophisticated malware. Recent reports have suggested that new computer worms and malware deliberately avoid fast massive propagation. Instead, they lurk in infected machines
From playlist The CERIAS Security Seminars 2006

Black Hat USA 2010: Crash Analysis Using BitBlaze 4/5
Speakers: Charlie Miller, Noah Johnson You've fuzzed your favorite application and found a mountain of crashes, now what? BitBlaze is an open source binary analysis platform which can perform whole system taint tracing, dynamic symbolic execution, as well as static analysis. Using BitBlaz
From playlist BH USA 2010 - REVERSE ENGI

22C3: Finding and Preventing Buffer Overflows
Speaker: Martin Johns An overview of static and dynamic approaches A talk that will present academic tools, which are designed to find or disarm security problems in C code For more information visit: http://bit.ly/22c3_information To download the video visit: http://bit.ly/22c3_videos
From playlist 22C3: Private Investigations

Shmoocon 2010: BaSO4: A Dynamic Dataflow Analysis Tool for Auditing and Reversing 1/5
Clip 1/5 Speaker: Dion Blazakis The complexity of modern applications makes binary auditing a long slow march without a significant investment in tools and techniques. BaSO4 is a new IDA plug-in that highlights the instructions responsible for processing and propogating the information
From playlist ShmooCon 2010

Black Hat USA 2010: Crash Analysis Using BitBlaze 5/5
Speakers: Charlie Miller, Noah Johnson You've fuzzed your favorite application and found a mountain of crashes, now what? BitBlaze is an open source binary analysis platform which can perform whole system taint tracing, dynamic symbolic execution, as well as static analysis. Using BitBlaz
From playlist BH USA 2010 - REVERSE ENGI

Black Hat USA 2010: Deconstructing ColdFusion 2/5
Speakers: Chris Eng, Brandon Creighton ColdFusion is a somewhat forgotten but still very prevalent web application development platform. This presentation is a technical survey of ColdFusion security that will be of interest mostly to code auditors, penetration testers, and developers. I
From playlist BH USA 2010 - WEB APPS

Bitcoin Q&A: Blacklists, Taint, and Wallet Fingerprinting
Would companies try to blacklist coins that have been mixed with CoinJoin? What is taint? What is wallet fingerprinting? Chapters 0:00 Do you think there is potential for companies and exchanges to blacklist all CoinJoined bitcoin? 3:14 What does tainted mean? 6:22 What is wallet fingerpr
From playlist Privacy and Surveillance

DEFCON 14: Automatic Exploit Detection in Binaries
Speakers: Matt Hargett Luis Miras, Lead Vulnerability Researcher, Intrusion Inc. Abstract: Binary disassembling and manual analysis to find exploitable vulnerabilities is a cool topic. What's cooler? Saving yourself hours of time and brain rot by letting a program do the hard parts for yo
From playlist DEFCON 14

Tutorial for verifying trigonometric identities
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

NOTACON 6: Injection Rejection, or How I Learned To Stop Worrying and Love Bobby Tables
Speaker: catfood Security pros are familiar with the well-known SQL Injection and Shell Injection attacks. But more obscure attacks such as DNS Injection and even Clipper Macro Injection proliferate because many programmers don't know any better. Learn how to write injection-proof code in
From playlist Notacon 6