
History of computers - A Timeline
A timeline from the first computer, The Turing Machine, to the 1970's. Hope you guys enjoy,and make sure to subscribe and like! Adding subtitles for our video is welcomed! Your translation can help people around the world see our awesome videos! http://www.youtube.com/timedtext_cs_panel?c
From playlist Computers

What Is Infrastructure As Code?
Infrastructure as code is a central idea in Continuous Delivery. The environment in which our software exists is a dependency of our software, so we need to control that environment as far as we can. If our aim is to release software reliably and repeatedly we need to control the variables
From playlist Software Engineering

What Software Architecture Should Look Like
What is Software Architecture? It’s a surprisingly difficult question to answer. We can describe software architecture patterns and argue about what is the best software architecture, but in reality, most definitions are vague enough to be unhelpful or so over the top to be more like a lis
From playlist Software Engineering

Introduction to Computer Programming for beginners || Coding for beginners
Computer programming is the process of performing a particular computation (or more generally, accomplishing a specific computing result), usually by designing and building an executable computer program. Programming involves tasks such as analysis, generating algorithms, profiling algorit
From playlist Programming

Zigurd Mednieks, How software architectures adapt to the Internet of Things
Many of the considerations that software architects have to monitor in traditional projects are of even higher importance in the Internet of Things, such as distributed resources and handling local failures.
From playlist O'Reilly Software Architecture Conference 2015

An introduction to microservices from Software Engineering Daily. Find out about microservices and microservice architecture in this quick animation. Music by The Prion. http://softwareengineeringdaily.com -- Learn to code for free and get a developer job: https://www.freecodecamp.com
From playlist Computer Science Concepts

[LISA] Linguistically-Informed Self-Attention for Semantic Role Labeling | AISC
For more details including paper and slides, visit https://aisc.a-i.science/events/2019-04-25/
From playlist Natural Language Processing

Stanford Seminar - ML Explainability Part 2 I Inherently Interpretable Models
Professor Hima Lakkaraju presents some of the latest advancements in machine learning models that are inherently interpretable such as rule-based models, risk scores, generalized additive models and prototype based models. View the full playlist: https://www.youtube.com/playlist?list=PLoR
From playlist Stanford Seminars

Is Designing Different To Coding?
In software development, what is the relationship between “Code” and “Design”? Is code the responsibility of one set of people, and design another, or are these part of a continuum in software design where code, design and architecture are essential just different aspects of the same activ
From playlist Software Engineering

Kaggle Reading Group: Dissecting contextual word embeddings (Part 2) | Kaggle
Join Kaggle Data Scientist Rachael as she reads through an NLP paper! Today's paper is "Dissecting contextual word embeddings: Architecture and representation" (Peters et al, 2018). You can find a copy here: https://aclweb.org/anthology/D18-1179 SUBSCRIBE: https://www.youtube.com/c/kaggle?
From playlist Kaggle Reading Group | Kaggle

Software Architecture Conference 2015
For more information, visit: http://oreil.ly/1Cyt9nt Software architecture is a massive multidisciplinary subject, covering many roles and responsibilities, which makes it challenging to teach because so much context is required for every subject. It's also a fast-moving discipline, where
From playlist O'Reilly Software Architecture Conference 2015

Stanford Seminar - Instruction execution on the Mill CPU
"Instruction execution on the Mill CPU" -Ivan Godard, Out-of-the-Box Computing Colloquium on Computer Systems Seminar Series (EE380) presents the current research in design, implementation, analysis, and use of computer systems. Topics range from integrated circuits to operating systems
From playlist Engineering

Learning Explanatory Rules from Noisy Data - Richard Evans, DeepMind
Artificial Neural Networks are powerful function approximators capable of modelling solutions to a wide variety of problems, both supervised and unsupervised. As their size and expressivity increases, so too does the variance of the model, yielding a nearly ubiquitous overfitting problem.
From playlist Logic and learning workshop
Ross King: "Automating Science using Robot Scientists"
Machine Learning for Physics and the Physics of Learning 2019 Workshop I: From Passive to Active: Generative and Reinforcement Learning with Physics "Automating Science using Robot Scientists" Ross King, University of Manchester Institute of Science and Technology (UMIST) Abstract: A Rob
From playlist Machine Learning for Physics and the Physics of Learning 2019

End-to-End Differentiable Proving: Tim Rocktäschel, University of Oxford
We introduce neural networks for end-to-end differentiable proving of queries to knowledge bases by operating on dense vector representations of symbols. These neural networks are constructed recursively by taking inspiration from the backward chaining algorithm as used in Prolog. Specific
From playlist Logic and learning workshop
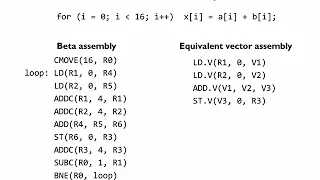
MIT 6.004 Computation Structures, Spring 2017 Instructor: Chris Terman View the complete course: https://ocw.mit.edu/6-004S17 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP62WVs95MNq3dQBqY2vGOtQ2 21.2.2 Data-level Parallelism License: Creative Commons BY-NC-SA More i
From playlist MIT 6.004 Computation Structures, Spring 2017

Stanford Seminar: Building Systems Using Malicious Components
EE380: Colloquium on Computer Systems Building Systems Using Malicious Components: How I learned to Stop Worrying and Trust SNARK Proofs Speaker: Eran Tromer, Tel Aviv University and Columbia University "Computers are unreliable and vulnerable to attacks. Therefore, we shouldn't belie
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

Computational Semantics: How Computers Know what Words Mean [Lecture]
This is a single lecture from a course. If you you like the material and want more context (e.g., the lectures that came before), check out the whole course: https://boydgraber.org/teaching/CMSC_723/ (Including homeworks and reading.) Music: https://soundcloud.com/alvin-grissom-ii/review
From playlist Computational Linguistics I
