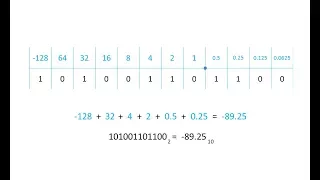
Binary 3 – Fixed Point Binary Fractions
This is the third in a series of videos about the binary number system which is fundamental to the operation of a digital electronic computer. It covers the representation of real numbers in binary using a fixed size, fixed point, register. It explains with examples how to convert both po
From playlist Binary
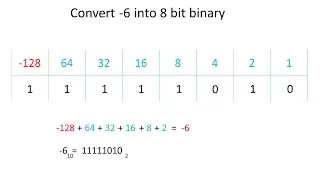
Binary 2 - Two's Complement Representation of Negative Numbers
This is the second in a series of computer science videos about the binary number system which is fundamental to the operation of a digital electronic computer. It covers the two's complement system of representing positive and negative integers in binary. It demonstrates how two's comple
From playlist Binary

Binary 4 – Floating Point Binary Fractions 1
This is the fourth in a series of videos about the binary number system which is fundamental to the operation of a digital electronic computer. In particular, this video covers the representation of real numbers using floating point binary notation. It begins with a description of standard
From playlist Binary

Binary 7 – Floating Point Binary Addition
This is the seventh in a series of videos about the binary number system which is fundamental to the operation of a digital electronic computer. In particular, this video covers adding together floating point binary numbers for a given sized mantissa and exponent, both in two’s complement.
From playlist Binary

How To Add and Subtract Binary Numbers
This video explains how to add and subtract binary numbers. The full version of this video contains extra examples of subtracting, multiplying, and dividing binary numbers. Full 43 Minute Video: https://www.youtube.com/watch?v=eAdWDu3s8xM
From playlist Number Systems
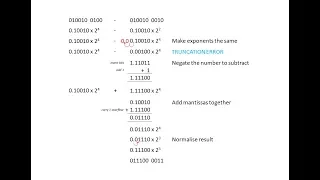
Binary 8 – Floating Point Binary Subtraction
This is the eighth in a series of videos about the binary number system which is fundamental to the operation of a digital electronic computer. In particular, this video covers subtraction of floating point binary numbers for a given sized mantissa and exponent, both in two’s complement.
From playlist Binary
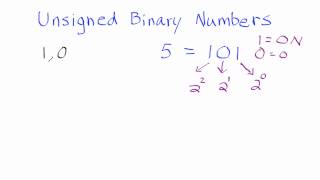
1. Unsigned Binary Numbers - How to Convert From Unsigned Binary Numbers to Whole Numbers
This tutorial shows how to convert from an unsigned binary number to a whole number. Join this channel to get access to perks: https://www.youtube.com/channel/UCn2SbZWi4yTkmPUj5wnbfoA/join :)
From playlist Binary Numbers

Binary 1 - Converting to and from Denary
This is the first in a series of computer science videos about the binary number system which is fundamental to the operation of a digital electronic computer. It covers the need for binary and details of how to convert positive whole numbers in base 10 into 8 bit binary, and vice versa.
From playlist GCSE Computer Science

IEEE 754 Standard for Floating Point Binary Arithmetic
This computer science video describes the IEEE 754 standard for floating point binary. The layouts of single precision, double precision and quadruple precision floating point binary numbers are described, including the sign bit, the biased exponent and the mantissa. Examples of how to con
From playlist Binary

IDA Pro Automated String Decryption For REvil Ransomware
Use IDA Pro and python to automatically decrypt the RC4 strings in REvil (Sodinokibi) ransomware. Expand description for details... ----- OALABS DISCORD https://discord.gg/6h5Bh5AMDU OALABS PATREON https://www.patreon.com/oalabs OALABS TIP JAR https://ko-fi.com/oalabs OALABS GITHUB htt
From playlist REvil (Sodinokibi) Reverse Engineering

What Lies Beneath - A Deep Dive Into Clojure's Data Structures - Mohit Thatte
Immutable, persistent data structures are at the heart of Clojure's philosophy. It is instructive to see how these are implemented, to appreciate the trade-offs between persistence and performance. Lets explore the key ideas that led to effective, practical implementations of these data st
From playlist Clojure, Lisp

WinDbg Basics for Malware Analysis
In this tutorial we cover the basics of debugging malware with WinDbg. Expand for more... ----- OALABS DISCORD https://discord.gg/6h5Bh5AMDU OALABS PATREON https://www.patreon.com/oalabs OALABS TIP JAR https://ko-fi.com/oalabs OALABS GITHUB https://github.com/OALabs UNPACME - AUTOMATE
From playlist Open Analysis Live!

30C3: An introduction to Firmware Analysis (EN)
For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speaker: Stefan Widmann This talk gives an introduction to firmware analysis: It starts with how to retrieve the binary, e.g. get a plain file from manufacturer, extract it
From playlist 30C3

Analyzing Hancitor DLL Live - Let's Build A Config Extractor!
Join us as we reverse engineer the Hancitor DLL and write a config extractor for it in python. Expand for more ... ----- OALABS DISCORD https://discord.gg/6h5Bh5AMDU OALABS PATREON https://www.patreon.com/oalabs OALABS TIP JAR https://ko-fi.com/oalabs OALABS GITHUB https://github.com/O
From playlist Open Analysis Live!

DEFCON 14: Ripples in the Gene Pool - Creating Genetic: Mutations to Survive the Vulerability Window
Speaker: Chris Eagle, Senior Lecturer of Computer Science Abstract: Reverse engineers often like to argue that a prime motivator for their activities is the desire to discover and patch vulnerabilities in closed-source binary software. Given the veritable plethora.. nay, Katrina-like floo
From playlist DEFCON 14

Black Hat USA 2010: Payload Already Inside: Data Re Use for ROP Exploits 3/4
Speaker: Long Le Return-oriented programming (ROP) is one of the buzzing advanced exploitation techniques these days to bypass NX. There are several practical works using ROP techniques for exploitations on Windows, iPhoneOS to bypass DEP and code signing but no any practical ROP work for
From playlist BH USA 2010 - PROGRAMMATIC

DEFCON 13: Reverse Engineering Network Protocols using Bioinformatics
Speaker: Marshall Beddoe Network protocol analysis is currently performed by hand using only intuition and a protocol analyzer tool such as tcpdump or Ethereal. This talk presents Protocol Informatics, a method for automating network protocol reverse engineering by utilizing algorithms f
From playlist DEFCON 13

DEFCON 18: Function Hooking for Mac OSX and Linux 1/3
Speaker: Joe Damato This talk will cover three different methods of function hooking for Mac OSX and Linux. The talk will begin by describing useful bits of Intel64 assembly followed up with 3 different binary rewriting techniques to hook a range of different functions, including some i
From playlist DEFCON 18-3
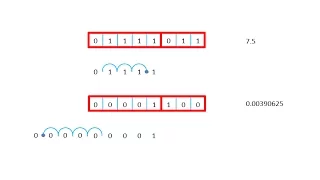
Binary 5 – Floating Point Range versus Precision
This is the fifth in a series of videos about the binary number system which is fundamental to the operation of a digital electronic computer. In particular, this video elaborates on the representation of real numbers using floating point binary notation. It explains how the relative allo
From playlist Binary
