
Discrete Math: 05. Binary Reflected Gray Codes
The Binary Reflected Gray Codes are defined in this video and several small examples are provided. We also prove that they are indeed Gray Codes. -- Bits of Discrete Math by Dr. Sarada Herke. Related videos: http://youtu.be/RURnaoPTEMI - Discrete Math: 04. Gray Codes http://youtu.be/X8
From playlist Discrete Math part-1

Ex: Reflect a Point about the x-axis, y-axis, and the Origin
This video provides an example of how to determine the coordinates of a point reflected about the x-axis, y-axis, and the origin. Site: http://mathispower4u.com
From playlist Determining Transformations of Functions
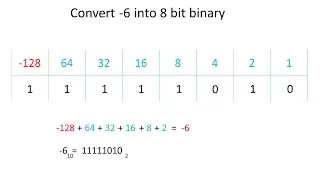
Binary 2 - Two's Complement Representation of Negative Numbers
This is the second in a series of computer science videos about the binary number system which is fundamental to the operation of a digital electronic computer. It covers the two's complement system of representing positive and negative integers in binary. It demonstrates how two's comple
From playlist Binary
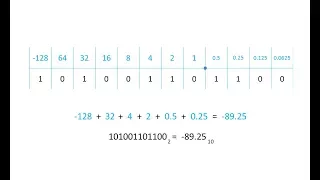
Binary 3 – Fixed Point Binary Fractions
This is the third in a series of videos about the binary number system which is fundamental to the operation of a digital electronic computer. It covers the representation of real numbers in binary using a fixed size, fixed point, register. It explains with examples how to convert both po
From playlist Binary

Binary 4 – Floating Point Binary Fractions 1
This is the fourth in a series of videos about the binary number system which is fundamental to the operation of a digital electronic computer. In particular, this video covers the representation of real numbers using floating point binary notation. It begins with a description of standard
From playlist Binary
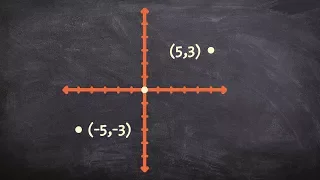
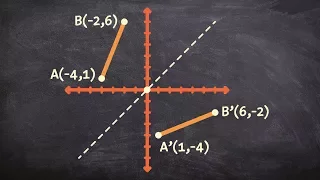
How to reflect a point over the origin
👉 Learn how to reflect points and a figure over a line of symmetry. Sometimes the line of symmetry will be a random line or it can be represented by the x or y-axis. Either way when reflecting a point and or figure over the line of symmetry it is important to think of flipping the figure
From playlist Transformations

How to reflect a line over the origin
👉 Learn how to reflect points and a figure over a line of symmetry. Sometimes the line of symmetry will be a random line or it can be represented by the x or y-axis. Either way when reflecting a point and or figure over the line of symmetry it is important to think of flipping the figure
From playlist Transformations

Hamiltonicity of Cayley graphs and Gray codes: open problems by Elena Konastantinova
DATE & TIME 05 November 2016 to 14 November 2016 VENUE Ramanujan Lecture Hall, ICTS Bangalore Computational techniques are of great help in dealing with substantial, otherwise intractable examples, possibly leading to further structural insights and the detection of patterns in many abstra
From playlist Group Theory and Computational Methods
How to reflect a line segment over the y=x line
👉 Learn how to reflect points and a figure over a line of symmetry. Sometimes the line of symmetry will be a random line or it can be represented by the x or y-axis. Either way when reflecting a point and or figure over the line of symmetry it is important to think of flipping the figure
From playlist Transformations

Offensive Golang Bonanza: Writing Golang Malware
The past two years have seen the rise of Golang-based malware from its beginnings as a way to win at CCDC and red team engagements to its current use by actual threat actors. This talk will break down why Golang is so useful for malware with a detailed tour through the available components
From playlist Golang

In this video I describe the motivation behind Gray codes, which are a specific way of listing the binary sequences of length n. We also discuss a Graph-Theoretic way of viewing Gray codes. -- Bits of Discrete Math by Dr. Sarada Herke. Related videos: http://youtu.be/X8mnQJ5AlTM - Graph
From playlist Discrete Math part-1

DEFCON 20: Detecting Reflective Injection
Speaker: ANDREW KING CONTRACT RESEARCHER, GRAYHAT RESEARCH, LLC This talk will focus on detecting reflective injection with some mildly humorous notes and bypassing said protections until vendors start actually working on this problem. It seems amazing that reflective injection still work
From playlist DEFCON 20

OWASP AppSecUSA 2012: Interactive Application Security Testing(IAST), Beyond SAST/DAST
Speaker: Ofer Maor Until recently, SAST/DAST dominated the application security testing market, each with its own pros and cons. We present IAST, a completely new approach - analyzing code execution, memory and data in runtime, allowing for accurate inspection of the application. We will
From playlist OWASP AppSecUSA 2012

!!Con West 2019 - Jeroen (Jerry) Van Leeuwen: Fast code! By removing all branches!
Presented at !!Con West 2019: http://bangbangcon.com/west Performance optimization should never be your first concern when creating a solution, and run-time code generation is always a measure of last resort. But when I was faced with the seemingly insurmountable task of making .NET 2.0
From playlist !!Con West 2019

Black Hat USA 2010: Constricting the Web: Offensive Python for Web Hackers 4/4
Clip 4/4 Speakers: Nathan Hamiel, Marcin Wielgoszewski It seems that everything is a web application nowadays. Whether the application is cloud-based, mobile, or even fat client they all seem to be using web protocols to communicate. Adding to the traditional landscape there is rise in
From playlist Black Hat USA 2010

Black Hat USA 2010: pyREtic: Reversing Obfuscated Python Bytecode Live Python Objects 1/5
Speaker: Rich Smith Increasing numbers of commercial and closed source applications are being developed in Python. The Developers of these applications are investing increasing amounts to stop people being able to see their source code through by a variety of bytecode obfuscation efforts.
From playlist REVERSE ENGINEERING REDUX

!!Con West 2019 - Jeroen (Jerry) Van Leeuwen: Fast code! By removing all branches!
Presented at !!Con West 2019: http://bangbangcon.com/west Performance optimization should never be your first concern when creating a solution, and run-time code generation is always a measure of last resort. But when I was faced with the seemingly insurmountable task of making .NET 2.0
From playlist !!Con West 2019

C# Reflection Explained | Reflection In C# | C# Tutorial Reflection Example |C# Tutorial|Simplilearn
"This video on C# Reflection Explained will clearly explain Reflections in C#. In this C# tutorial on Reflection in C#, you will get a proper Introduction To C# Reflection Explained. We will begin our session with a discussion on What is Metadata, followed by a brief discussion on C# Refle
From playlist C# Training 🔥[2022 Updated]

an introduction to the concept of reflection transformations
From playlist Common Core Standards - 8th Grade