
Obfuscated C programs: Introduction
If you program long enough, eventually you will run into a programming art category called "obfuscated code" or “code golf”. You can find these especially at IOCCC. In this video I introduce the concept and the basic ideas behind such design. More information below (click "Show more"). I
From playlist Programming

What is an Injective Function? Definition and Explanation
An explanation to help understand what it means for a function to be injective, also known as one-to-one. The definition of an injection leads us to some important properties of injective functions! Subscribe to see more new math videos! Music: OcularNebula - The Lopez
From playlist Functions

Definition of an Injective Function and Sample Proof
We define what it means for a function to be injective and do a simple proof where we show a specific function is injective. Injective functions are also called one-to-one functions. Useful Math Supplies https://amzn.to/3Y5TGcv My Recording Gear https://amzn.to/3BFvcxp (these are my affil
From playlist Injective, Surjective, and Bijective Functions

Injective, Surjective and Bijective Functions (continued)
This video is the second part of an introduction to the basic concepts of functions. It looks at the different ways of representing injective, surjective and bijective functions. Along the way I describe a neat way to arrive at the graphical representation of a function.
From playlist Foundational Math
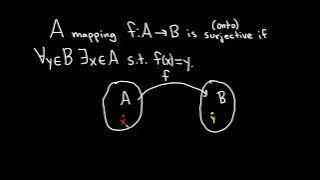
Definition of a Surjective Function and a Function that is NOT Surjective
We define what it means for a function to be surjective and explain the intuition behind the definition. We then do an example where we show a function is not surjective. Surjective functions are also called onto functions. Useful Math Supplies https://amzn.to/3Y5TGcv My Recording Gear ht
From playlist Injective, Surjective, and Bijective Functions
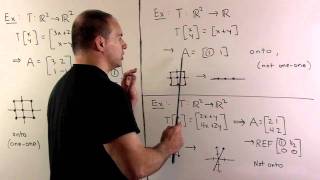
Linear Algebra: Continuing with function properties of linear transformations, we recall the definition of an onto function and give a rule for onto linear transformations.
From playlist MathDoctorBob: Linear Algebra I: From Linear Equations to Eigenspaces | CosmoLearning.org Mathematics
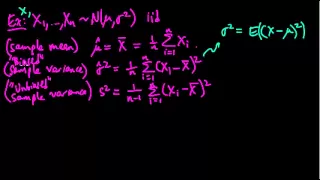
Definition of an estimator. Examples of estimators. Definition of an unbiased estimator.
From playlist Machine Learning

Abstract Algebra | Injective Functions
We give the definition of an injective function, an outline of proving that a given function is injective, and a few examples. http://www.michael-penn.net http://www.randolphcollege.edu/mathematics/
From playlist Abstract Algebra

This video explains what a mathematical function is and how it defines a relationship between two sets, the domain and the range. It also introduces three important categories of function: injective, surjective and bijective.
From playlist Foundational Math

Windows Red Team - Dynamic Shellcode Injection & PowerShell Obfuscation
In this video, I will be exploring the process of dynamically injecting Shellcode into portable executables and PowerShell obfuscation for the purpose of defense evasion on Windows. Defense Evasion consists of techniques that adversaries use to avoid detection throughout their compromise.
From playlist Red Team Fundamentals

Malware Software Armoring Circumvention 1/5
Speaker: Danny Quist clip 1°5
From playlist ShmooCon 2008

DEFCON 15: CaffeineMonkey: Automated Collection, Detection and Analysis of Malicious JavaScript
Speakers: Daniel Peck Security Researcher, Secureworks Ben Feinstein Security Researcher, Secureworks The web browser is ever increasing in its importance to many organizations. Far from its origin as an application for fetching and rendering HTML, today's web browser offers an expansive
From playlist DEFCON 15

DEFCON 18: Gaming in the Glass Safe Games DRM and Privacy 1/4
Speaker: Ferdinand Schober "DRM is the new form of slavery - but it also spies on you." - conversation with a gamer After years of perceived-rampant piracy on the PC, game publishers are beginning to shackle gamers with increasingly intrusive DRM systems. However, recent game news he
From playlist DEFCON 18-3

DEFCON 15: Covert Debugging: Circumventing Software Armoring Techniques
Speakers: Danny Quist Cofounder, Offensive Computing, LLC Valsmith Cofounder, Offensive Computing, LLC Software armoring techniques have increasingly created problems for reverse engineers and software analysts. As protections such as packers, run-time obfuscators, virtual machine and deb
From playlist DEFCON 15

Botleggers Exposed - Analysis of The Conti Leaks Malware
Join us for analysis of the leaked Conti malware, what is BazarLoader, how is Conti operated, and what does all this mean for your security team. These are our first thoughts as the situation unfolds... Twitter account for the leaker: https://twitter.com/ContiLeaks ----- OALABS DISCORD h
From playlist Open Analysis Live!

CERIAS Security: Obfuscated Databases: Definitions and Constructions 2/6
Clip 2/6 Speaker: Vitaly Shmatikov · University of Texas at Austin I will present some new definitions and constructions for privacy in large databases. In contrast to conventional privacy mechanisms that aim to prevent any access to individual records, our techniques are designed to
From playlist The CERIAS Security Seminars 2005 (1)

Getting around obfuscated code: Sara Chipps interviewed at Fluent 2012
Sara Chipps Developer, Girl Develop It Sara Chipps is a JavaScript developer and she blogs at http://sarajchipps.com. She consults with early stage startups as an interim CTO, serving to walk teams through the difficult task of building their first web application. In 2010, along with
From playlist Fluent 2012
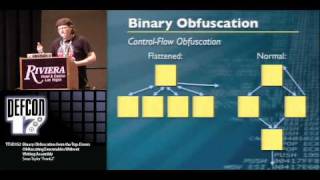
DEFCON 17: Binary Obfuscation from the Top-Down: Obfuscating Executables Without Writing Assembly
Speaker: Sean "Frank^2" Taylor Security Engineer, Rapid7 Binary obfuscation is commonly applied in malware and by software vendors in order to frustrate the efforts of reverse engineers to understand the underlying code. A common misconception is one must be a master of assembly in order
From playlist DEFCON 17

Black Hat USA 2010: NEPTUNE: Dissecting Web-Based Malware via Browser and OS Instrumentation 1/5
Speaker: Rami Kawach Increased built-in security and robust standard configurations have made the classical operating system vulnerabilities a rare occurrence. Malware authors have been forced to switch to alternative channels to get their malicious software installed. One of the main del
From playlist REVERSE ENGINEERING REDUX