
An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Cryptographic Hash Functions: Part 1
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

https://en.wikipedia.org/wiki/SHA-1#Examples_and_pseudocode If you have any questions of want to contribute to code or videos, feel free to write me a message on youtube or get my contact in the About section or googling my contacts.
From playlist Programming

Cryptographic Hash Functions: Part 2
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

In this video, you’ll learn more about how hashtags are used on Twitter. Visit https://www.gcflearnfree.org/twitter/what-is-a-hashtag/1/ for our text-based lesson. This video includes information on: • Using hashtags • Browsing popular hashtags We hope you enjoy!
From playlist Twitter

Get the Code Here: http://goo.gl/srwIf Welcome to my Java Hash Table tutorial. A Hash Table is a data structure offers fast insertion and searching capabilities. The negative is that they are limited in size because they are based on arrays. They are also hard to order. People get confus
From playlist Java Algorithms
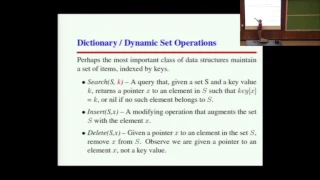
This is Lecture 6 of the CSE373 (Analysis of Algorithms) course taught by Professor Steven Skiena [http://www3.cs.stonybrook.edu/~skiena/] at Stony Brook University in 2016. The lecture slides are available at: https://www.cs.stonybrook.edu/~skiena/373/newlectures/lecture6.pdf More infor
From playlist CSE373 - Analysis of Algorithms 2016 SBU

Lecture 6 - Applications of Sorting
This is Lecture 6 of the CSE373 (Analysis of Algorithms) course taught by Professor Steven Skiena [http://www.cs.sunysb.edu/~skiena/] at Stony Brook University in 2007. The lecture slides are available at: http://www.cs.sunysb.edu/~algorith/video-lectures/2007/lecture6.pdf More informati
From playlist CSE373 - Analysis of Algorithms - 2007 SBU

Cryptographic Hash Functions (Contd...2)
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Hash Tables and Hash Functions
This computer science video describes the fundamental principles of the hash table data structure which allows for very fast insertion and retrieval of data. It covers commonly used hash algorithms for numeric and alphanumeric keys and summarises the objectives of a good hash function. Co
From playlist Data Structures

Solving Private Set Intersection via Cuckoo Hashing: Benny Pinkas, Bar-Ilan University, Israel
Private set intersection (PSI) allows two parties to compute the intersection of their sets without revealing any information about items that are not in the intersection. There has been considerable research on designing custom secure protocols for computing PSI, due to the fact that PSI
From playlist Turing Seminars

CSE 373 --- Lecture 6: Hashing (Fall 2021)
9/9/21
From playlist CSE373 --- Analysis of Algorithms (Fall 2021)

Lecture 9: Table Doubling, Karp-Rabin
MIT 6.006 Introduction to Algorithms, Fall 2011 View the complete course: http://ocw.mit.edu/6-006F11 Instructor: Erik Demaine License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.006 Introduction to Algorithms, Fall 2011

Lec 8 | MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503), Fall 2005
Lecture 08: Universal Hashing, Perfect Hashing View the complete course at: http://ocw.mit.edu/6-046JF05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503),

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Lec 7 | MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503), Fall 2005
Lecture 07: Hashing, Hash Functions View the complete course at: http://ocw.mit.edu/6-046JF05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503),



