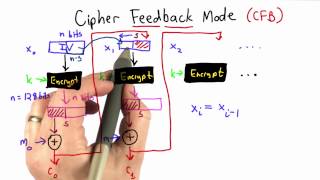
Key feedback mode
In cryptography key feedback mode (KFB) is a mode of operation for cryptographic block ciphers. It uses the block cipher output block to form the block cipher key of the next round, thereby creating a keystream generator that can be used as a synchronous stream cipher. (Wikipedia).