
EEVblog #1194 - 1985 Electronics
Dave uncovered the first edition of Australian Electronics Monthly magazine from July 1985, by Roger Harrison, and featuring a classic David Tilbrook MOSFET amplifier design, vintage computer, vintage analog scopes and more. Forum: http://www.eevblog.com/forum/blog/eevblog-1194-1985-elec
From playlist Vintage Computers

MIT 6.858 Computer Systems Security, Fall 2014 View the complete course: http://ocw.mit.edu/6-858F14 Instructor: Nickolai Zeldovich In this lecture, Professor Zeldovich discusses how to cryptographically protect network communications, as well as how to integrate cryptographic protection
From playlist MIT 6.858 Computer Systems Security, Fall 2014

From playlist everything

MIT 6.858 Computer Systems Security, Fall 2014 View the complete course: http://ocw.mit.edu/6-858F14 Instructor: Nickolai Zeldovich In this lecture, Professor Zeldovich discusses network security, and how TCP/IP has evolved. License: Creative Commons BY-NC-SA More information at http://o
From playlist MIT 6.858 Computer Systems Security, Fall 2014

MIT 6.858 Computer Systems Security, Fall 2014 View the complete course: http://ocw.mit.edu/6-858F14 Instructor: Nickolai Zeldovich In this lecture, Professor Zeldovich discusses the Kerberos authentication service. License: Creative Commons BY-NC-SA More information at http://ocw.mit.ed
From playlist MIT 6.858 Computer Systems Security, Fall 2014

MIT 6.858 Computer Systems Security, Fall 2014 View the complete course: http://ocw.mit.edu/6-858F14 Instructor: James Mickens In this lecture, Professor Mickens discusses authentication schemes and their implementations. License: Creative Commons BY-NC-SA More information at http://ocw.
From playlist MIT 6.858 Computer Systems Security, Fall 2014

From playlist Linear Algebra Ch 8 (updated Jan2021)

RI Seminar: Yann LeCun : The Next Frontier in AI: Unsupervised Learning
Yann LeCun Director of AI Research at Facebook, Professor of Computer Science, New York University November 18, 2016 Abstract The rapid progress of AI in the last few years are largely the result of advances in deep learning and neural nets, combined with the availability of large datase
From playlist AI talks

Why There Is No Alternative to Publicly Funded Science Research | Avideh Zakhor | Big Think
Why There Is No Alternative to Publicly Funded Science Research Watch the newest video from Big Think: https://bigth.ink/NewVideo Join Big Think Edge for exclusive videos: https://bigth.ink/Edge ---------------------------------------------------------------------------------- For our f
From playlist Best Videos | Big Think

CSDM - Noga Alon - October 13, 2015
http://www.math.ias.edu/calendar/event/83634/1444746600/1444753800
From playlist Computer Science/Discrete Mathematics

[Rust Programming] Advent of Code Episode 27 - 2015 Day 22 [4/4] - Both Solutions
Day 22 took a bit longer than the average, so this is split up into 4 sections. This is the final one! Once I was able to model (and debug) the input properly, the solutions to both parts was straightforward #aoc #adventofcode #rust #rustlang #aoc2015
From playlist Advent of Code

MrExcel's Learn Excel #854 - VLOOKUP Below
Can the VLOOKUP return a value one row below the matched value? Episode 854 shows you how to achieve this result using two other functions. This blog is the video podcast companion to the book, Learn Excel 97-2007 from MrExcel. Download a new two minute video every workday to learn one of
From playlist VLOOKUP

MySQL Database with Python Tutorial Part 3 - UPDATE, DELETE, AND SELECT
Python + MySQL in playlist: http://www.youtube.com/watch?v=lhU2OZCKXhQ&feature=share&list=PLQVvvaa0QuDfhTF3Zfyzc_yD-Mq9iTp4G&index=26 Here, you are shown how to update, delete, and select data from a database. The UPDATE command allows you to modify pre-existing data. This can be useful i
From playlist MySQL with Python and MySQLdb
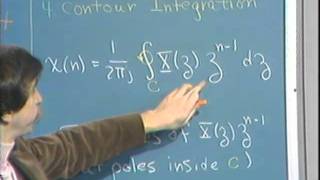
Lec 6 | MIT RES.6-008 Digital Signal Processing, 1975
Lecture 6: The inverse z-transform Instructor: Alan V. Oppenheim View the complete course: http://ocw.mit.edu/RES.6-008 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT RES.6-008 Digital Signal Processing, 1975

GRCon20 - Security Analysis of Zigbee Networks with Zigator and GNU Radio
Presented by Dimitrios-Georgios Akestoridis, Madhumitha Harishankar, Michael Weber and Patrick Tague at GNU Radio Conference 2020 https://gnuradio.org/grcon20 Zigbee is a wireless communication protocol that is based on the IEEE 802.15.4 standard and is commonly used in smart homes. Numer
From playlist GRCon 2020

25c3: FAIFA: A first open source PLC tool
Speakers: Florian, Xavier Carcelle PowerLineCommunications has now their open source tool PLC (PowerLineCommunications) had been widely used currently for the in-home LANs and for Internet access over PowerLineCommunications based on the market standard called HomePlug. Electricity is a
From playlist 25C3: Nothing to hide
From playlist Communications & Network Systems

Wireless Network Security: Part 2
Fundamental concepts of IEEE 802.11 WLAN are discussed. IEEE 802.11i WLAN security is Reviewed. WAP is presented. Wireless transport layer security is analyzed. IEEE 802.11 Wireless LAN Overview Legacy 802.11 Security: WEP IEEE 802.11i Wireless LAN Security: WPA, WPA2 Wireless Application
From playlist Network Security

Lec 7 | MIT RES.6-008 Digital Signal Processing, 1975
Lecture 7: z-Transform properties Instructor: Alan V. Oppenheim View the complete course: http://ocw.mit.edu/RES6-008S11 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT RES.6-008 Digital Signal Processing, 1975
