
An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography
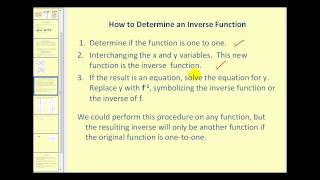
(New Version Available) Inverse Functions
New Version: https://youtu.be/q6y0ToEhT1E Define an inverse function. Determine if a function as an inverse function. Determine inverse functions. http://mathispower4u.wordpress.com/
From playlist Exponential and Logarithmic Expressions and Equations

From playlist Cryptography Lectures

Cryptographic Hash Functions: Part 1
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

A graphic and algebraic approach to finding inverse functions. Definition of the Inverse of a Function Let f and g be two functions such that f(g(x)) = x for every x in the domain of g and g(f(x)) = x for all x in the domain of f. Check out http://www.ProfRobBob.com, there you will find
From playlist PreCalculus

An introduction to inverse functions. I talk about what an inverse function is, the relationship between domain and range, and the composition of two inverse functions. Stay tuned for part two! Facebook: https://www.facebook.com/braingainzofficial Instagram: https://www.instagram.com/b
From playlist Precalculus

Quantum Computing - Spooky Action at a Distance - Extra History - #4
What happens when we can't link physical cause and effect between two actions? Well, quantum bits (or qubits) do this all the time. Let's look into how quantum entanglement can be used in computing. Credit to Alisa Bishop for her art on this series: http://www.alisabishop.com/ A tremendou
From playlist Extra History : Quantum Computing

Lecture 13. Fugue: Bach, Bizet and Bernstein
Listening to Music (MUSI 112) In this lecture, Professor Wright briefly explores the manifestations of the fugue form in poetry, painting, and other disciplines, and then gives a detailed explanation of how fugues are put together in music. Though he uses excerpts by composers as disparat
From playlist Listening to Music with Craig Wright

Lecture 14. Ostinato Form in the Music of Purcell, Pachelbel, Elton John and Vitamin C
Listening to Music (MUSI 112) This lecture begins with a review of all the musical forms previously discussed in class: sonata-allegro, rondo, theme and variations, and fugue. Professor Wright then moves on to discuss the final form that will be taught before the students' next exam: osti
From playlist Listening to Music with Craig Wright

Cryptographic Hash Functions: Part 2
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

Eating Poison Fish | National Geographic
The puffer fish is a very expensive dish to eat...but watch out, it can kill you. ➡ Subscribe: http://bit.ly/NatGeoSubscribe #NationalGeographic #PufferFish #Fugu About National Geographic: National Geographic is the world's premium destination for science, exploration, and adventure. Th
From playlist Oceans | National Geographic

Live CEOing Ep 107: Language Design in Wolfram Language
Watch Stephen Wolfram and teams of developers in a live, working, language design meeting. This episode is about Language Design in the Wolfram Language.
From playlist Behind the Scenes in Real-Life Software Design

Lec 27 | MIT 7.012 Introduction to Biology, Fall 2004
Nervous System 2 (Prof. Eric Lander) View the complete course: http://ocw.mit.edu/7-012F04 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 7.012 Introduction to Biology, Fall 2004

Bach: Toccata and Fugue in D minor, BWV 565
Posibly my favourite Bach composition. The Toccata and Fugue in D minor, BWV 565, is a piece of organ music composed by Johann Sebastian Bach sometime between 1703 and 1707. It is one of the most famous works in the organ repertoire, and has been used in a variety of popular media ranging
From playlist Brilliant Music

Lecture 23: Hash Tables - Richard Buckland UNSW Computing2
Lecture 23 of comp1927 data structures and algorithms aka computing2. Searching searching searching... Searching leads us to hash tables and maybe even more. What dark horrors lurk ahead...??? Richard Buckland UNSW Computing recorded in 2009.
From playlist CS2: Data Structures and Algorithms - Richard Buckland

Lecture 16. Baroque Music: The Vocal Music of Johann Sebastian Bach
Listening to Music (MUSI 112) In this lecture, Professor Wright discusses the Baroque period through a detailed look at the life and music of Johann Sebastian Bach. He first takes the students through the basics of Bach's life, showing slides of the towns and buildings in which Bach and h
From playlist Listening to Music with Craig Wright

Unlocking New Capabilities for the Web
To close the capability gap between the web and native to provide a solid foundation for modern applications delivered on the web, the web needs open. Learn how some of these new capabilities work, what's on our road map, and how we're designing them to work in a way that respect user. EV
From playlist Web Development

Define an inverse function. Determine if a function as an inverse function. Determine inverse functions.
From playlist Determining Inverse Functions

