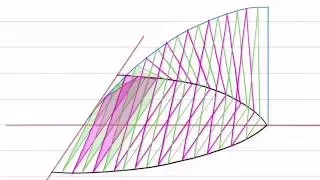
I'll be back shortly with a new video series on forward and inverse kinematics. In the meantime, here's a bit of a preview of what can be done with what will be covered in the next video.
From playlist Kinematics

Why does time go forward? How does Entropy relate to the direction of time? What really is time, and what gives it a direction? The Arrow of Time. Hi! I'm Jade. I draw pictures that move and become animated physics videos. ***SUBSCRIBE*** https://www.youtube.com/c/upandatom ***Let's b
From playlist Physics

Distance and Displacement? | #Shorts #YouTubeShorts | Don't Memorise
What’s the difference between distance and displacement? Watch this video to find out more! Don’t Memorise brings learning to life through its captivating educational videos. To Know More, visit https://infinitylearn.com/ New videos every week. To stay updated, subscribe to our YouTube c
From playlist Shorts

Why I got a Google One membership
As I was close to exceeding my storage limit for Gmail, I decided to get a Google One membership. I have ways to get around it, but I chose not to. You might decide to do the same.
From playlist Technology

In this video, I define what it means to rearrange (or reshuffle) a series and show that if a series converges absolutely, then any rearrangement of the series converges to the same limit. Interesting Consequence: https://youtu.be/Mw7ocynGVmw Series Playlist: https://www.youtube.com/play
From playlist Series

Speaker: Jens Kubieziel An introduction into anonymous communication with I2P I2P is a message-based anonymizing network. It builds a virtual network between the communication endpoints. This talk will introduce the technical details of I2P and show some exemplary applications. My talk
From playlist 24C3: Full steam ahead

CERIAS Security: Sphinx: A Compact and Provably Secure Mix Format 2/6
Clip 2/6 Speaker: Ian Goldberg · University of Waterloo Mix networks, originally proposed in 1981, provide a way for Internet users to send messages--such as email, blog posts, or tweets--without automatically revealing their identities or their locations. In this talk, we will describe
From playlist The CERIAS Security Seminars 2009

DEFCON 16: Could Googling Take Down a President, a Prime Minister, or an Average Citizen?
Speaker: Greg Conti, United States Military Academy Every time we use the web, we disclosure tremendous amounts of information to ISPs, Internet backbone providers, and online companies; information that will be shared and data mined, but rarely discarded. Email addresses, phone numbers,
From playlist DEFCON 16

IMT4306: Anonymous communication protocols
IMT4306: Research in Mobile/Decentralised technologies Anonymity, privacy, anonymous communication protocols.
From playlist Archive - Research in Mobile/Wearable Tech

What goes on TOR stays on TOR, or so we hope. Dr Mike Pound takes us through how Onion Routing works. This video was formerly called "Onion Routing" EXTRA BITS: https://youtu.be/6eWkdyRNfqY End to End Encryption: https://youtu.be/jkV1KEJGKRA Deep Web / Dark Web: https://youtu.be/joxQ_X
From playlist The Deep, Dark Web

Speaker: Len Sassaman Why not just use Tor? In recent years, an increasing amount of academic research has been focused on secure anonymous communication systems. In this talk, we briefly review the state of the art in theoretical anonymity systems as well as the several deployed and ac
From playlist 24C3: Full steam ahead

DEFCON 20: Anonymous and the Online Fight for Justice
Speakers: AMBER LYON INDEPENDENT INVESTIGATIVE JOURNALIST GABRIELLA COLEMAN CHAIR IN SCIENTIFIC AND TECHNOLOGICAL LITERACY, MCGILL UNIVERSITY, DEPARTMENT OF ART HISTORY & COMMUNICATION STUDIES MARCIA HOFFMAN SENIOR STAFF ATTORNEY, ELECTRONIC FRONTIER FOUNDATION MERCEDES HAEFER STUDENT, UN
From playlist DEFCON 20
DEFCON 19: Anonymous Cyber War
Speakers: Hubris Strategic Operations, Backtrace Security | a5h3r4h Director of Psychological Operations This talk will educate listeners on best practices for safety and privacy on the Internet.It aims to demonstrate the improbability of staying anonymous while engaging in group or socia
From playlist DEFCON 19

Ethics and Computational Social Science (Part 2)
In the second of two videos, Professor Matt Salganik of Princeton University discusses ethical issues in the field of Computational Social Science. Link to slides used in this video: https://github.com/compsocialscience/summer-institute/blob/master/2020/materials/day1-intro-ethics/ethics_p
From playlist SICSS 2020

AlterConf Portland 2017: Privacy & Anonymity may be ruining your Diversity and...by Miki Demeter
Privacy & Anonymity may be ruining your Diversity and Inclusion by Miki Demeter Diversity and inclusion are the latest buzzwords in corporate HR. Studies show teams perform better when developed with these considerations. However, how HR actually handles these issues can be very problemat
From playlist AlterConf Portland 2017
Link Building for a New Website: 5 Actionable Ways to Get More Backlinks
Having a heard time getting links? Learn 5 actionable link building strategies to get powerful backlinks even if no one knows who you are. *************************************** Additional Link Building Resources How to Build Unique Backlinks With Resource Page Link Building ► https://w
From playlist Link Building Tutorials (Step-By-Step)