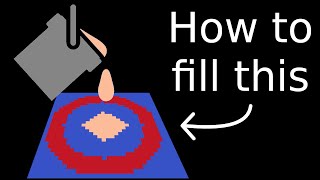
Algorithm Archive: https://www.algorithm-archive.org/contents/flood_fill/flood_fill.html Source code: In chapter Github sponsors (Patreon for code): https://github.com/sponsors/leios Twitch: https://www.twitch.tv/leioslabs Discord: https://discord.gg/QctJhUA Github: https://github.com
From playlist Algorithm Archive

SYN Flood Denial of Service attack using perl script and hping3 tool.
From playlist Denial of Service attacks

Heap Sort - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

Tutorial: GeoHTTP Remote Buffer Overflow and DoS
A real example of a Buffer Overflow/Denial of Service attack! My favorite video: http://www.youtube.com/watch?v=z00kuZIVXlU Visit http://binslashshell.wordpress.com and join our forum community!!! This is a video showing what a Buffer Overflow Aattck can do to a Web Server. For th
From playlist Denial of Service attacks

My attempt at writing an epidemic algorithm to describe the propagation of viral videos... -- Watch live at https://www.twitch.tv/simuleios
From playlist Viral videos

Almost Linear Time Algorithms for Max-flow and More - Sushant Sachdeva
Computer Science/Discrete Mathematics Seminar II Topic: Almost Linear Time Algorithms for Max-flow and More Speaker: Sushant Sachdeva Affiliation: University of Toronto Date: October 18, 2022 We give the first almost-linear time algorithm for computing exact maximum flows and minimum-cos
From playlist Mathematics

Modeling of Compound Flooding in Coastal Environments
SIAM Geosciences Webinar Series Title: Modeling of Compound Flooding in Coastal Environments Date and Time: Thursday, April 7, 2022, 12:00pm Eastern time zone Speaker: Clint Dawson, University of Texas Austin Abstract: Compound flooding is flooding due to two or more events occurring simu
From playlist SIAM Geosciences Webinar Series

Understanding Routing! | ICT#8
The amazing journey of data packets from a data center to your device forms the backbone of the Internet. This data flow is governed to make the most efficient transfer of the data. It is apparent from this animation that this governing of the data, from the source to the destination, thro
From playlist Internet & Telecommunication Technology

Broadcasted live on Twitch -- Watch live at https://www.twitch.tv/simuleios
From playlist Misc

Discrete Math - 3.1.3 Sorting Algorithms
Bubble sort and insertion sort algorithms. Textbook: Rosen, Discrete Mathematics and Its Applications, 7e Playlist: https://www.youtube.com/playlist?list=PLl-gb0E4MII28GykmtuBXNUNoej-vY5Rz
From playlist Discrete Math I (Entire Course)

Christian Claudel: "Data assimilation & optimal control in the context of UAV-based flash flood..."
Mathematical Challenges and Opportunities for Autonomous Vehicles 2020 Workshop III: Large Scale Autonomy: Connectivity and Mobility Networks "Data assimilation and optimal control in the context of UAV-based flash flood monitoring" Christian Claudel - University of Texas at Austin Abstr
From playlist Mathematical Challenges and Opportunities for Autonomous Vehicles 2020

CERIAS Security: Provable security in mobile ad hoc networks 5/6
Clip 5/6 Speaker: Mike Burmester · Florida State Mobile ad hoc networks (MANETs) are collections of wireless mobile nodes with links that are made or broken in an arbitrary way. Communication is achieved via routes whose node relay packets. Several routing algorithms have been propose
From playlist The CERIAS Security Seminars 2006

Build a Heap - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms
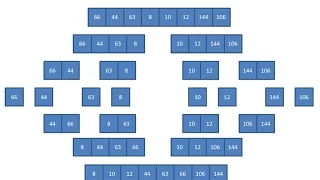
This is the first in a series of videos about the merge sort. It describes the principle of the merge sort algorithm, which takes a ‘divide and conquer’ approach to the problem of sorting and unordered list. The videos that follow build on these principles, leading towards a recursive im
From playlist Sorting Algorithms

Breadth First Search (BFS): Visualized and Explained
In this video we break down the BFS algorithm in a visual manner with examples and key intuition. We then show the implementation of the algorithm with code and then finish off the video by demonstrating how you can use the BFS algorithm to solve the Flood Fill problem. 0:00 Introduction
From playlist Graph Theory

Fellow Short Talks: Professor Rob Procter, University of Warwick
Bio Rob Procter is Professor of Social Informatics and deputy head (research) in the department of Computer Science, Warwick University. Previously he has held positions at Manchester and Edinburgh universities. His research interests are strongly inter-disciplinary, and include social me
From playlist Short Talks

From playlist Algorithms 1

Stanford Seminar - Strategies to Fight Disaster
Nicole Hu One Concern April 24, 2019 Nicole Hu and her two co-founders created One Concern to help communities prepare for and mitigate natural disasters by harnessing the power of AI. She explains how they use machine intelligence as a predictive tool, and shares strategies for identifyi
From playlist MS&E472 - Entrepreneurial Thought Leaders - Stanford Seminars
