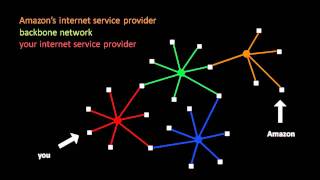
Routing algorithms | Flooding algorithms
Flooding (computer networking)
Flooding is used in computer networks routing algorithm in which every incoming packet is sent through every outgoing link except the one it arrived on. Flooding is used in bridging and in systems such as Usenet and peer-to-peer file sharing and as part of some routing protocols, including OSPF, DVMRP, and those used in ad-hoc wireless networks (WANETs). (Wikipedia).