
The method of determining eigenvalues as part of calculating the sets of solutions to a linear system of ordinary first-order differential equations.
From playlist A Second Course in Differential Equations

Changing notation with complex eigenvalues.
From playlist A Second Course in Differential Equations

Irrigation Efficiencies - Part 1
From playlist TEMP 1

Evaluating Recurrence Relations (1 of 4: When do you apply Recurrence Relations?)
More resources available at www.misterwootube.com
From playlist Further Integration

With the eigenvalues for the system known, we move on the the eigenvectors that form part of the set of solutions.
From playlist A Second Course in Differential Equations

B22 Introduction to Substitutions
An overview of the three type of substitutions as a new method of solving linear, exact, and "almost" separable differential equations.
From playlist Differential Equations

Calculus Introduction to U-Substitution
In this lesson, I introduce the concept of u-substitution for integrals with a brief review of substitution techniques in Algebra first. This technique is also known as integration by substitution.
From playlist Calculus
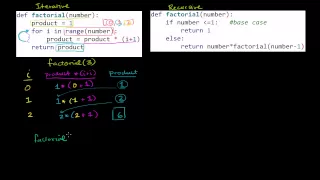
Comparing Iterative and Recursive Factorial Functions
Comparing iterative and recursive factorial functions
From playlist Computer Science

Kernel Recipes 2014 - Performance does matter
Deploying clouds is in everybody’s mind but how to make an efficient deployment ? After setting up the hardware, it’s mandatory to make a deep inspection of server’s performance. In a farm of supposed identical servers, many miss-{installation|configuration} could seriously degrade perfo
From playlist Kernel Recipes 2014

Java OOPs Concepts | Object Oriented Programming | Java Tutorial For Beginners | Edureka
🔥 Java Certification Training: https://www.edureka.co/java-j2ee-training-course This Edureka video on “Java OOPs Concepts” will give you a brief insight about various fundamentals of Object Oriented Programming in Java like Inheritance, Abstraction, Encapsulation, and Polymorphism along w
From playlist Java Tutorial For Beginners | Edureka

Cyberinfrastructure Software Sustainability and Reusability Workshop 3
Clifford Lynch gives his presentation, "Software and the Long Haul" for the NSF-funded workshop, “Cyberinfrastructure software sustainability and reusability,” held March 27-28, 2009, in Indianapolis. This workshop was organized by the IU Pervasive Technology Institute and supported financ
From playlist 2009 Workshop on Software Sustainability and Reusability

Black Hat USA 2010: Advanced AIX Heap Exploitation Methods 2/5
Speaker: Tim Shelton With the ever increasing importance of providing and maintaining reliable services for both infrastructure support as well as business continuity, companies rely upon the IBM AIX operating system. In most cases, these machines hold the most critical data available for
From playlist Black Hat USA 2010

24C3: Crouching Powerpoint, Hidden Trojan
Speaker: Maarten Van Horenbeeck An analysis of targeted attacks from 2005 to 2007 Targeted trojan attacks first attracted attention in early 2005, when the UK NISCC warned of their wide spread use in attacks on UK national infrastructure. Incidents such as "Titan Rain" and the compromis
From playlist 24C3: Full steam ahead

Java OOPs Concepts For Beginners | Object Oriented Programming Concepts | Edureka | Java Rewind- 3
🔥Java Certification Training: https://www.edureka.co/java-j2ee-training-course This Edureka video on “Java OOPs Concepts” will give you a brief insight about various fundamentals of Object Oriented Programming in Java like Inheritance, Abstraction, Encapsulation, and Polymorphism along wi
From playlist Edureka Live Classes 2020

Selenium Automation Framework | Selenium Automation Testing Videos For Beginners | Simplilearn
🔥 Gain extensive hands-on training in software development, testing, and quality assurance technology skills, including phase-end and capstone projects based on real business scenarios: https://www.simplilearn.com/automation-testing-training-course-placement-guarantee?utm_campaign=Selenium
From playlist Selenium Tutorial Videos [2022 Updated]

Difficult to form a recipe here, but through judicious use of substitution you can infinitely simplify a DE. Have a look.
From playlist Differential Equations



