
PreCalculus | Radical Equations with Complex Solutions
We solve a two step radical equation with complex solutions. http://www.michael-penn.net http://www.randolphcollege.edu/mathematics/
From playlist PreCalculus

A graphic and algebraic approach to finding inverse functions. Definition of the Inverse of a Function Let f and g be two functions such that f(g(x)) = x for every x in the domain of g and g(f(x)) = x for all x in the domain of f. Check out http://www.ProfRobBob.com, there you will find
From playlist PreCalculus

An introduction to inverse functions. I talk about what an inverse function is, the relationship between domain and range, and the composition of two inverse functions. Stay tuned for part two! Facebook: https://www.facebook.com/braingainzofficial Instagram: https://www.instagram.com/b
From playlist Precalculus

How to Solve Trigonometric Equations (Precalculus - Trigonometry 22)
A very In-Depth look into solving equations that involve trig functions. We will focus on solving equations without having to use inverse trigonometric functions and relating solutions to the unit circle. Support: https://www.patreon.com/ProfessorLeonard
From playlist Precalculus - College Algebra/Trigonometry

👉 Learn about graphing linear equations. A linear equation is an equation whose highest exponent on its variable(s) is 1. i.e. linear equations has no exponents on their variables. The graph of a linear equation is a straight line. To graph a linear equation, we identify two values (x-valu
From playlist ⚡️Graph Linear Equations | Learn About
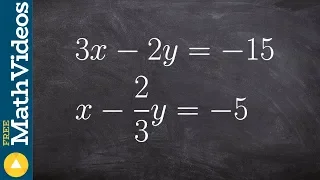
Solve a system of equation when they are the same line
👉Learn how to solve a system (of equations) by elimination. A system of equations is a set of equations which are collectively satisfied by one solution of the variables. The elimination method of solving a system of equations involves making the coefficient of one of the variables to be e
From playlist Solve a System of Equations Using Elimination | Medium

Solving a system of equations with infinite many solutions
👉Learn how to solve a system (of equations) by elimination. A system of equations is a set of equations which are collectively satisfied by one solution of the variables. The elimination method of solving a system of equations involves making the coefficient of one of the variables to be e
From playlist Solve a System of Equations Using Elimination | Medium

Follow-up: Barbie electronic typewriter
Here is a copy of the description from the Barbie video: ---- I first found this story on the crypto museum website, which has great information about the Barbie typewriter (and other cipher machines) https://www.cryptomuseum.com/crypto/mehano/barbie/ ------- Thanks to Sarah Everett fr
From playlist My Maths Videos

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Live CEOing Ep 544: Language Design in Wolfram Language [Ciphers & WFR Submissions] [Part 01]
In this episode of Live CEOing, Stephen Wolfram discusses upcoming improvements and features to the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through the official Twitch channel of Stephen Wolfram
From playlist Behind the Scenes in Real-Life Software Design
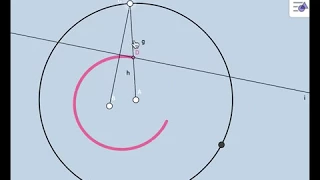
Ellipse: Construction and Locus Definition - A Conceptual Approach
Link to Lesson Investigation Activity: https://www.geogebra.org/m/TZu6tRwE BGM: Andy Hunter
From playlist PreCalculus: Dynamic Interactives!

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography
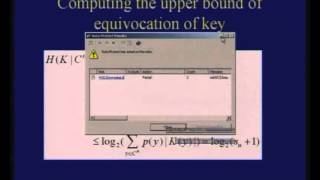
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

What is Bill Cipher? (Scientific Analysis)
What is Bill Cipher? Today we discover the very very confusing science of what Gravity Fall's Bill Cipher is. =======WARNING VERY VERY CONFUSING======= This video talks about dimensions and alternate universes. Your mind might explode! Sources: -http://en.wikipedia.org/wiki/Four-dim...
From playlist Scientific Videos

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

The Barbie electronic typewriter - with Just My Typewriter
I first found this story on the crypto museum website, which has great information about the Barbie typewriter (and other cipher machines) https://www.cryptomuseum.com/crypto/mehano/barbie/ ------- Thanks to Sarah Everett from Just My Typewriter, check out her channel here: https://www.y
From playlist My Maths Videos

25c3: An introduction to new stream cipher designs
Speaker: Tor E. Bjørstad Turning data into line noise and back Even with "nothing to hide", we want to protect the privacy of our bits and bytes. Encryption is an important tool for this, and stream ciphers are a major class of symmetric-key encryption schemes. Algorithms such as RC4 (us
From playlist 25C3: Nothing to hide

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

How do you graph an equation using the intercept method
👉 Learn about graphing linear equations. A linear equation is an equation whose highest exponent on its variable(s) is 1. i.e. linear equations has no exponents on their variables. The graph of a linear equation is a straight line. To graph a linear equation, we identify two values (x-valu
From playlist ⚡️Graph Linear Equations | Learn About
