
Directory Links and Subdir Count
More videos like this online at http://www.theurbanpenguin.com We can use the link count in a long listing of a directory to easily understand how many sub-directories exist for a given directory. Each directory has two links, the directory name itself and the name . meaning this directory
From playlist Linux
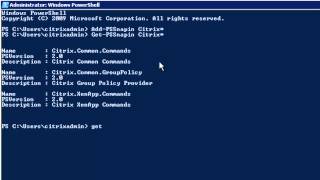
More videos like this online at http://www.theurbanpenguin.com if you are looking to make a start with PowerShell this may help you on your way using PowerShell with Citrix XenApp. We look at how you can list command by the module and the associated verb or noun
From playlist Citrix

Data structures: Introduction to Doubly Linked List
See complete series on data structures here: http://www.youtube.com/playlist?list=PL2_aWCzGMAwI3W_JlcBbtYTwiQSsOTa6P In this lesson, we have described doubly linked list data structure. For practice problems and more, visit: http://www.mycodeschool.com Like us on Facebook: https://www
From playlist Data structures

Sign up for our Excel webinar, times added weekly: https://www.excelcampus.com/blueprint-registration/ In this post, I explain the XOR function is used in the context of tracking attendance. This is Part 1 of 6 in a series that shows you how to build a dashboard for an attendance report.
From playlist Excel Formulas

See complete series on data structures here: http://www.youtube.com/playlist?list=PL2_aWCzGMAwI3W_JlcBbtYTwiQSsOTa6P In this lesson, we have described linked list data structure. We have analyzed our limitations with array data structure and tried to understand the need for linked list. F
From playlist Data structures

SORT & SORTBY Functions Dashboard Part 4 of 6
Sign up for our Excel webinar, times added weekly: https://www.excelcampus.com/blueprint-registration/ Learn to use the Dynamic Array Functions SORT and SORTBY to sort and rank a list based on criteria from a corresponding range. This is especially useful for displaying a list that's ranke
From playlist Excel Formulas

Linked List Data Structure 1. Representation and Traversal (algorithms and pseudocode).
This is the first in a series of videos about the linked list data structure. It mentions the applications of linked lists, and describes how a linked list can be represented programmatically using a Data array and an array of Next pointers. It also includes pseudocode for traversing, an
From playlist Data Structures

[c] Introduction to Linked Lists
From playlist Data Structures

Python Programming Practice: LeetCode #136 -- Single Number
In this episode of Python Programming Practice: LeetCode #136 -- Single Number ** Note: at 4:48 I misspoke. I should have said if it is NOT already in counts, store it.** Link to the problem here: https://leetcode.com/problems/single-number/ If you don't know Python, you can learn the
From playlist Python Programming Practice

Live Coding A Squirrelwaffle Malware Config Extractor
Join us as we reverse engineer Squirrelwaffle and write a config extractor for it in python. Expand for more ... ----- OALABS DISCORD https://discord.gg/6h5Bh5AMDU OALABS PATREON https://www.patreon.com/oalabs OALABS TIP JAR https://ko-fi.com/oalabs OALABS GITHUB https://github.com/OAL
From playlist Open Analysis Live!

Live Stream #119 - Solving Merge Conflicts and XOR Problem
In this live stream, I go through pull requests on the JavaScript neural network library repo and take another crack at the XOR coding challenge. 26:40 - Resolving merge conflicts 52:51 - XOR Problem Schedule and topics: https://github.com/CodingTrain/Rainbow-Code/blob/master/README.md
From playlist Live Stream Archive

Yes, You Too Can Break Crypto: Exploiting Common Crypto Mistakes
Cryptography is tricky. Sure, everybody knows not to roll out their own crypto, but is it enough? Are the standard algorithms, libraries, and utilities always used the right way? This is of course a rhetorical question! Humans keep making mistakes that other humans can exploit, and Murphy’
From playlist Security

Lec 21 | MIT 6.172 Performance Engineering of Software Systems, Fall 2010
Lecture 21: Quiz 2 Review Instructor: John Dong View the complete course: http://ocw.mit.edu/6-172F10 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.172 Performance Engineering of Software Systems

Live: Creating Cracking Videogame Passwords Episode 13
See the process of discovering how a NES game encodes / decodes its passwords, live. Disassembling and reverse-engineering a game I have not researched before. In the advent of 1990 I played NES games a lot. Knowing nothing about programming but being geekish by nature, I obsessed over cr
From playlist Cracking Videogame Passwords Season 1

Cleaning images and creating description files - OpenCV with Python for Image and Video Analysis 19
Simple enough, this script will visit the links, grab the URLs, and proceed to visit them. From here, we grab the image, convert to grayscale, resize it, then save it. We use a simple counter for naming the images. Go ahead and run it. As you can probably see, there are a lot of missing pi
From playlist OpenCV with Python for Image and Video Analysis

Linked Lists Python | Data Structures in Python | Python Tutorial | Edureka
🔥Edureka Python Certification Training: https://www.edureka.co/python-programming-certification-training This Edureka video on Linked Lists Python is a part of Python Tutorial series which discusses the concept of the linked lists in Python Programming. A linked list is a linear data struc
From playlist Python Programming Tutorials | Edureka

Speaker: Thorsten Holz Storm Worm Not only the Web has reached level 2.0, also attacks against computer systems have advanced in the last few months: Storm Worm, a peer-to-peer based botnet, is presumably one of the best examples of this development. Instead of a central command & cont
From playlist 24C3: Full steam ahead

Citrix : Branding Your Web Interface Site
More videos like this online at http://www.theurbanpenguin.com Sharing a Web Interface site for both Citrix XenApp and XenDesktop is probably what you would like to do. However the XenApp site is branded for XenApp and vice versa for XenDesktop. You may want to replace these central logo w
From playlist Citrix

J and Bex vs Primorial 15 | MegaFavNumbers
Solving boolean expressions, and how 614,889,782,588,491,410 became my #megafavnumber ! table of contents: 00:00 intro: primorial 15 01:23 the problem to solve (factoring in bex) 03:31 solving the problem in J 06:03 the problem in bex 07:38 scaling the problem 08:39 visualizing x*y=6 in
From playlist MegaFavNumbers