
Can You Validate These Emails?
Email Validation is a procedure that verifies if an email address is deliverable and valid. Can you validate these emails?
From playlist Fun

Second Order Recurrence Formula (1 of 3: Prologue - considering the old course)
More resources available at www.misterwootube.com
From playlist Further Proof by Mathematical Induction

Verifying Particular Solutions to Differential Equations Calculus 1 AB
I reintroduce Differential Equations including the definition of a differential equations, the order of differential equations, the difference between particular solutions and general solutions, and the number of arbitrary constants you can expect when solving these equations. I then work
From playlist Calculus

Verifying an identify by expanding an expression
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

Randomness - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

9. Verification and Validation
MIT 16.842 Fundamentals of Systems Engineering, Fall 2015 View the complete course: http://ocw.mit.edu/16-842F15 Instructor: Olivier de Weck The focus of this lecture is design verification and validation. Other concepts including design tesing and technical risk management and flight rea
From playlist MIT 16.842 Fundamentals of Systems Engineering, Fall 2015

Kernel Recipes 2019 - Formal modeling made easy
Modeling parts of Linux has become a recurring topic. For instance, the memory model, the model for PREEMPT_RT synchronization, and so on. But the term “formal model” causes panic for most of the developers. Mainly because of the complex notations and reasoning that involves formal languag
From playlist Kernel Recipes 2019

Rolando Somma - The Quantum Linear Systems Problem - IPAM at UCLA
Recorded 24 January 2022. Rolando Somma of Los Alamos National Laboratory presents "The Quantum Linear Systems Problem" at IPAM's Quantum Numerical Linear Algebra Workshop. Abstract: The goal of the quantum linear systems problem (QLSP) is to prepare a quantum state proportional to the sol
From playlist Quantum Numerical Linear Algebra - Jan. 24 - 27, 2022

Determining the negation of a hypothesis and conclusion from a statement
👉 Learn how to find the negation of a statement. The negation of a statement is the opposite of the statement. It is the 'not' of a statement. If a statement is represented by p, then the negation is represented by ~p. For example, The statement "It is raining" has a negation of "It is not
From playlist Negation of a Statement

Luciano Campi, seminar - 15 February 2018
QUANTITATIVE FINANCE SEMINARS @ SNS Prof. Luciano Campi, London School of Economics Nonzero-sum stochastic differential games with impulse controls: a verification theorem with applications Abstract: We consider a general nonzero-sum impulse game with two players. The main mathematical
From playlist Quantitative Finance Seminar @ SNS
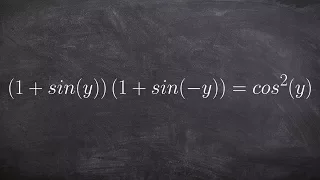
Verifying a trigonometric Identities
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities
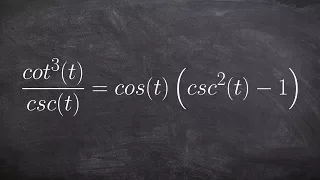
Verifying a trigonometric Identities
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

From playlist Cryptography Lectures

Nexus Trimester - Boaz Patt-Shamir (Tel Aviv University)
Randomized proof-labeling schemes Boaz Patt-Shamir (Tel Aviv University) February 12, 2016
From playlist Nexus Trimester - 2016 - Distributed Computation and Communication Theme

Randomness Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Ruby Conf 12 - Could a Machine ever write tests for our code by Loren Segal
TDD is a great way to test code, but have you ever wondered if there are ways to leverage the awesome power of computers and help us write better tests? Research in the field of formal verification has shown promising results with tools that analyze programs for logic errors and can even f
From playlist Ruby Conference 2012

Mod-01 Lec-36 The social construction of knowledge: Adaptation and Revolution
History of Economic Theory by Dr. Shivakumar, Department of Humanities and Social Sciences IIT Madras, For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist IIT Madras: History of Economic Theory | CosmoLearning.org Economics

Safety and robustness for deep learning with provable guarantees - Marta Kwiatkowska - Oxford
Computing systems are becoming ever more complex, with automated decisions increasingly often based on deep learning components. A wide variety of applications are being developed, many of them safety-critical, such as self-driving cars and medical diagnosis. Since deep learning is unstabl
From playlist Interpretability, safety, and security in AI

LambdaConf 2015 - Type Theory and its Meaning Explanations Jon Sterling
At the heart of intuitionistic type theory lies an intuitive semantics called the “meaning explanations." Crucially, when meaning explanations are taken as definitive for type theory, the core notion is no longer “proof” but “verification”. We’ll explore how type theories of this sort aris
From playlist LambdaConf 2015

Introduction to Proof by Induction: Prove 1+3+5+…+(2n-1)=n^2
This video introduces proof by induction and proves 1+3+5+…+(2n-1) equals n^2. mathispower4u.com
From playlist Sequences (Discrete Math)