
Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Transport Layer Security: Part 1
Fundamental concepts of TLS are discussed. SSL is analyzed. HTTPS & SSH are presented.
From playlist Network Security

If you are interested in learning more about this topic, please visit http://www.gcflearnfree.org/ to view the entire tutorial on our website. It includes instructional text, informational graphics, examples, and even interactives for you to practice and apply what you've learned.
From playlist The Internet

Transport Layer Security: Part 2 - TLS & HTTPS
Fundamental concepts of TLS are discussed. SSL is analyzed. HTTPS & SSH are presented.
From playlist Network Security

Network Security, Part 1 : Basic Encryption Techniques
Fundamental concepts of network security are discussed. It provides a good overview of secret Key and public key Encryption. Important data encryption standards are presented.
From playlist Network Security

Does it really matter what browser I choose?
You have a choice of browsers to select from. What makes a browser more - or less - secure? Learn some ways to assess a browser's security.
From playlist Internet Safety

Facebook: Understanding Privacy
In this video, you’ll learn more about how Facebook privacy works. Visit https://www.gcflearnfree.org/facebook101/understanding-facebook-privacy/1/ for our text-based lesson. This video includes information on: • Understanding basic privacy settings • Sharing and privacy • Facebook privac
From playlist Internet Safety

Network Security: Classical Encryption Techniques
Fundamental concepts of encryption techniques are discussed. Symmetric Cipher Model Substitution Techniques Transposition Techniques Product Ciphers Steganography
From playlist Network Security

EEVblog #1082 - What Do Compliance Logos Mean?
What does the UL type approval compliance logo on consumer products mean? What about TUV, ETL, GS, CCC and other marks? Dave breaks down safety standards and compliance marks. Previous video on the CE & FCC mark: https://www.youtube.com/watch?v=f0uvS80YIGU Forum: http://www.eevblog.com/f
From playlist General Tech Information

RubyHACK 2018: Interfaces Not Required by James Thompson
RubyHACK 2018: Interfaces Not Required by James Thompson Interfaces give classes a way to guarantee they behave in compatible ways. How can such a guarantee be afforded in Ruby without a language construct to provide it? Explore getting the same assurances through testing and behavior-ori
From playlist RubyHACK 2018

Type systems are becoming increasingly popular in the javascript community with leading projects increasingly adopting flow and typescript. Another awesome development in the javascript space has been the rise of css-in-js frameworks. This talk is a deep dive into the challenges and oppo
From playlist Talks

Lec 1 | MIT 22.091 Nuclear Reactor Safety, Spring 2008
Lecture 1: Introduction and overview Instructor: Andrew Kadak View the complete course: http://ocw.mit.edu/22-091S08 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 22.091 Nuclear Reactor Safety, Spring 2008

The Rust Memory Safety Model Explained
Check out Prabhu Eshwarla's book 📖 Rust Servers, Services, and Apps | http://http://mng.bz/KBl0 📖 To save 40% off this book ⭐ DISCOUNT CODE: watcheshwarla40 ⭐ Prabhu explains why and how should you use Rust for web development. In this video, Prabhu dives deeper into the Rust Memory Safety
From playlist Rust

A Case for Oxidation: The Rust Programming Language
For almost five decades, we've built core systems software in unsafe languages like C or C++. Four of these decades can be excused as no alternative existed that matched these languages in performance and control. In the last decade, however, Rust, a programming language sponsored by Mozil
From playlist Rust
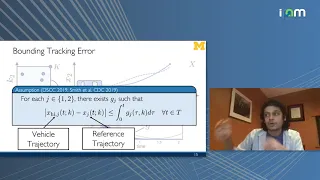
Ram Vasudevan: "Bridging the Gap Between Safety & Real-Time Performance for AV Control"
Mathematical Challenges and Opportunities for Autonomous Vehicles 2020 Workshop II: Safe Operation of Connected and Autonomous Vehicle Fleets "Bridging the Gap Between Safety and Real-Time Performance for Autonomous Vehicle Control" Ram Vasudevan - University of Michigan Abstract: Autono
From playlist Mathematical Challenges and Opportunities for Autonomous Vehicles 2020

RustConf 2017 - Closing Keynote: Safe Systems Software and the Future of Computing by Joe Duffy
Closing Keynote: Safe Systems Software and the Future of Computing by Joe Duffy Someday in the future, all important systems software on the planet will be written in a safe programming language. The questions are, when, and how do we get there? In this talk, I will describe my experienc
From playlist RustConf 2017
RustConf 2017 - Closing Keynote: Safe Systems Software and the Future of Computing by Joe Duffy
Closing Keynote: Safe Systems Software and the Future of Computing by Joe Duffy Someday in the future, all important systems software on the planet will be written in a safe programming language. The questions are, when, and how do we get there? In this talk, I will describe my experienc
From playlist RustConf 2017

Stanford Seminar - Building Safe Digital Products, Lisa Welchman
Lisa Welchman Digital Governance October 23, 2020 In its zest for innovation, the digital maker community, like new technology communities of the past, often does not consider its products and services' full impact. Makers have adopted agile methodologies that measure product readiness by
From playlist Stanford Seminars
