
Few other Cryptanalytic Techniques
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

This video gives a general introduction to cryptography WITHOUT actually doing any math. Terms covered include cryptology vs cryptography vs cryptanalysis, symmetric vs public key systems, and "coding theory." NOTE: Yes, I said and wrote "cryptOanalysis" when it's actually "cryptanalysis
From playlist Cryptography and Coding Theory

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Steganography Tutorial - Hide Messages In Images
Steganography is the hiding of a secret message within an ordinary message and the extraction of it at its destination. Steganography takes cryptography a step further by hiding an encrypted message so that no one suspects it exists. Ideally, anyone scanning your data will fail to know it
From playlist Ethical Hacking & Penetration Testing - Complete Course

Daniele Agostini - Curves and theta functions: algebra, geometry & physics
Riemann’s theta function is a central object throughout mathematics, from algebraic geometry to number theory, and from mathematical physics to statistics and cryptography. One of my long term projects is to develop a program to study and connect the various aspects - geometric, computatio
From playlist Research Spotlight

24C3: Quantum Cryptography and Possible Attacks
Speakers: Alexander Ling, Antia Lamas, Ilja Gerhardt, Christian Kurtsiefer Quantum cryptography is the oldest and best developed application of the field of quantum information science. Although it is frequently perceived as an encryption method, it is really a scheme to securely distri
From playlist 24C3: Full steam ahead

Nexus Trimester - Iftach Haitner (Tel Aviv University) - Leo Reyzin (Boston University) 2/3
Computational Analogues of Entropy 2/3 Iftach Haitner (Tel Aviv University) Leo Reyzin (Boston University) MArch 21, 2016 Abstract: If you see a cryptographic hash of my password, how can I quantify your uncertainty about the password? Entropy – a traditional measure of uncertainty – is
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme

Introduction - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Bitcoin Q&A: Protocol Development Security
What are the odds of "rogue developers" who introduce vulnerabilities? What happens if the digital signature algorithm is compromised? Is trust in hardware wallet developers and the firmware update process a problem? Note: I was mostly talking about Bitcoin and other popular open blockcha
From playlist English Subtitles - aantonop Videos with subtitles in English
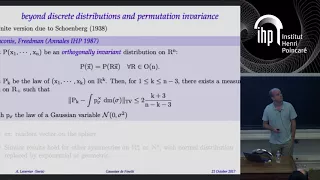
A Gaussian de Finetti theorem and application (...) - A.Leverrier - Workshop 2 - CEB T3 2017
Anthony Leverrier / 23.10.17 A Gaussian de Finetti theorem and application to truncations of random Haar matrices de Finetti theorems are pervasive in finite-dimensional quantum information theory as they state that permutation invariant quantum systems are in some sense close to convex
From playlist 2017 - T3 - Analysis in Quantum Information Theory - CEB Trimester

The Apocalypse and How to Avoid It
In billions of years, the sun will expand to engulf the Earth and life on this planet will become impossible. But there are plenty of ways it could end much sooner! Subscribe for regular science videos: http://bit.ly/RiSubscRibe Join Lewis Dartnell and a panel of scientists and disaster e
From playlist Ri Talks

Viewers like you help make PBS (Thank you 😃) . Support your local PBS Member Station here: https://to.pbs.org/DonateSPACE Learn through active problem-solving at Brilliant: https://brilliant.org/SpaceTime/ The Sun is getting brighter and the planets in our solar system that are habitable
From playlist The End(s) of the World

Introduction to Quantum Information and Computing by Barry Sanders
Dates: Thursday 03 Jan, 2013 - Saturday 05 Jan, 2013 Venue: ICTS-TIFR, IISc Campus, Bangalore The school aims to provide students and researchers an introduction to the field of quantum information, computation and communication. Topics that will be covered include introduction to quantu
From playlist Mini Winter School on Quantum Information and Computation

Primality (1 of 2: Fermat's Test)
From playlist Cryptography
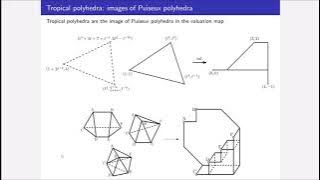
Ben Smith: Face structures of tropical polyhedra
Many combinatorial algorithms arise from the interplay between faces of ordinary polyhedra, therefore tropicalizing these algorithms should rely on the face structure of tropical polyhedra. While they have many nice combinatorial properties, the classical definition of a face is flawed whe
From playlist Workshop: Tropical geometry and the geometry of linear programming

