
Kernel Recipes 2018 - CPU Idle Loop Rework - Rafael J. Wysocki
The CPU idle loop is the piece of code executed by logical CPUs if they have no tasks to run. If the CPU supports idle states allowing it to draw less power while not executing any instructions, the idle loop invokes a CPU idle governor to select the most suitable idle state for the CPU an
From playlist Kernel Recipes 2018

CERIAS Security: An Alternate Memory Architecture for Code Injection Prevention 3/4
Clip 3/4 Speaker: Ryan Riley · Purdue University ode injection attacks, in their various forms, have been in existence and been an area of consistent research for a number of years. A code injection attack is a method whereby an attacker inserts malicious code into a running computing sy
From playlist The CERIAS Security Seminars 2009

CERIAS Security: An Alternate Memory Architecture for Code Injection Prevention 4/4
Clip 4/4 Speaker: Ryan Riley · Purdue University ode injection attacks, in their various forms, have been in existence and been an area of consistent research for a number of years. A code injection attack is a method whereby an attacker inserts malicious code into a running computing sy
From playlist The CERIAS Security Seminars 2009

CERIAS Security: An Alternate Memory Architecture for Code Injection Prevention 2/4
Clip 2/4 Speaker: Ryan Riley · Purdue University ode injection attacks, in their various forms, have been in existence and been an area of consistent research for a number of years. A code injection attack is a method whereby an attacker inserts malicious code into a running computing sy
From playlist The CERIAS Security Seminars 2009

Writing an OS in Rust - Part 7 - Hardware Interrupts
This is my version of Philipp Oppermann's "BlogOS". It's a baremetal operating system that can boot off of a USB stick on any BIOS-compatible machine, which is pretty amazing. I'm going to be following the whole blog, one video at a time, and running the OS using QEMU instead of booting a
From playlist Rust OS
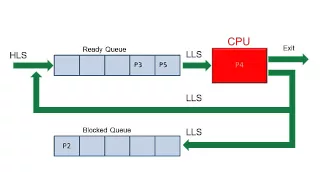
An animation showing the main features of a process scheduling system including the ready queue, blocked queue, high level scheduler and low level scheduler. It explains the principle of a round robin scheduling algorithm.
From playlist Operating Systems

RubyConf 2018 - Parallel programming in Ruby3 with Guild by Koichi Sasada
RubyConf 2018 - Parallel programming in Ruby3 with Guild by Koichi Sasada Do you want to write the parallel program with Ruby? Ruby 3 will offer new concurrent abstraction: Guild (code name) which enable to run Ruby programs in parallel without difficulties. This presentation will share o
From playlist RubyConf 2018

Meltdown and Spectre - Professor Mark Handley, UCL
The Meltdown and Spectre vulnerabilities in almost all modern CPUs have received a great deal of publicity in the last week. Operating systems and hypervisors need significant changes to how memory management is performed, CPU firmware needs updating, compilers are being modified to avoid
From playlist Data science classes

Object Serialization in Java | Serialization Interface | Java Tutorial | Edureka
**Java, J2EE & SOA Certification Training - https://www.edureka.co/java-j2ee-training-course ** This Edureka video on Serialization in Java will provide you with detailed knowledge about how the Serialization process in Java takes place along with the practical examples for a better unders
From playlist Java Tutorial For Beginners | Edureka

For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speaker: Andreas Bogk Violation of memory safety is still a major source of vulnerabilities in everyday systems. This talk presents the state of the art in compiler instrume
From playlist 30C3

How To Crack WiFi (Wireless) Networks Using Cow Patty and Air-Crack | Session 09 | #cybersecurity
Don’t forget to subscribe! In this tutorial series, you will learn to crack WiFi ( Wireless ) networks. We will use Cow Patty and Air-Crack in this tutorial to crack the WiFi networks. In this project, you will learn how to crack different Wireless networks including WEP, WPA, WPA2 netw
From playlist Crack WiFi (Wireless) Networks Using Cow Patty and Air-Crack

Gynvael Coldwind, Mateusz "j00ru" Jurczyk Beyond MOV ADD XOR -- the unusual and unexpected in x86
Intel x86 and the derived AMD64 architecture families are by far the most widespread and commonly known ones, powering millions and millions of desktop PCs, server racks and even some mobile devices. Although understanding low-level X86 assembly code has been subject to extensive study by
From playlist Gynvael's [EN] Talks and Interviews

22C3: "Xbox" and "Xbox 360" Hacking
Speakers: Felix Domke, Michael Steil 17 Mistakes Microsoft Made in the Xbox Security System & Xbox 360 Hacking A lot about Xbox hacking has been published earlier. This talk summarizes all this, explains some very cool new hacks and analyzes the 15 mistakes Microsoft made in the Xbox sec
From playlist 22C3: Private Investigations

CERIAS Security: An Alternate Memory Architecture for Code Injection Prevention 1/4
Clip 1/4 Speaker: Ryan Riley · Purdue University ode injection attacks, in their various forms, have been in existence and been an area of consistent research for a number of years. A code injection attack is a method whereby an attacker inserts malicious code into a running computing sy
From playlist The CERIAS Security Seminars 2009

How Meltdown and Spectre Make Your Computer Vulnerable
Another year, another security breach that could expose all of your information. Installing updates might be a good New Year's resolution. Check out the Crash Course Computer Science series at youtube.com/crashcourse We're conducting a survey of our viewers! If you have time, please give
From playlist Uploads

Kernel Recipes 2019 - Kernel hacking behind closed doors
The recent hardware security vulnerabilites exposed the kernel community to unprecedented restrictions and bureaucrazy. Pure software bugs which only affect the Linux kernel are a completely different category and the kernel community has established and well working ways to handle them.
From playlist Kernel Recipes 2019

RubyConf 2018 - Trash Talk: A Garbage Collection Choose-Your-Own-Adventure by Colin Fulton
RubyConf 2018 - Trash Talk: A Garbage Collection Choose-Your-Own-Adventure by Colin Fulton "Walking into work one day, you see a raccoon in an embroidered vest carefully picking through some dumpsters. Startled, the raccoon shouts, 'Ack! No one is supposed to notice me!' before running aw
From playlist RubyConf 2018

Firmware Security: Why It Matters and How You Can Have It
A system is only as secure as the least secure component it depends on. Hardening the kernel is a vital part of developing a secure operating system, but if the firmware underneath the kernel is insecure then attackers have an opportunity to sidestep your security and compromise you anyway
From playlist Security

UBUNTU enabling kernel crashdump
More videos like this online at http://www.theurbanpenguin.com In this video we look at enable the crash dump facility in the Linux kernel using Ubuntu. A Kernel Crash Dump refers to a portion of the contents of volatile memory (RAM) that is copied to disk whenever the execution of the ker
From playlist Learning Ubuntu Server

Hacking Livestream #43: Meltdown and Spectre
A much requested live about recent CPU vulnerabilities. A lot of links below. https://googleprojectzero.blogspot.ch/ https://www.youtube.com/watch?v=6O8LTwVfTVs http://pythonsweetness.tumblr.com/post/169166980422/the-mysterious-case-of-the-linux-page-table http://www.openwall.com/lists/os
From playlist Gynvael's [EN] Live