
[c][explained] Demystifying Pointers — Function Pointers
Find the complete program on https://www.notion.so/theteachr/Function-Pointers-9848de630cae47a7ad1ca5552d23a66d.
From playlist Demystifying Pointers

From playlist CS124 - Full Course

Evaluating Recurrence Relations (1 of 4: When do you apply Recurrence Relations?)
More resources available at www.misterwootube.com
From playlist Further Integration

Coin Vs Token: What Is The Difference Between A Cryptocurrency Coin And A Token? | Simplilearn
This video on "Coin vs Token" covers all the differences between Crypto Coin and Crypto Token in detail. This "Coin vs Token" video will help you understand the individuality of Cryptocurrencies and Crypto Tokens in the Crypto Market and how they function differently from each other on the
From playlist Blockchain Tutorial Videos 🔥[2022 Updated] | Simplilearn

DevOpsDays Boston 2018 - Vault At Scale by Matt Surabian
DevOpsDays Boston 2018 - Vault At Scale by Matt Surabian As an organization with 25 production environments and over 6,000 containerized applications we have a lot of secrets to manage. Enough to run 12 geographically distributed HA Vault deployments across multiple cloud providers. Even
From playlist DevOpsDays Boston 2018
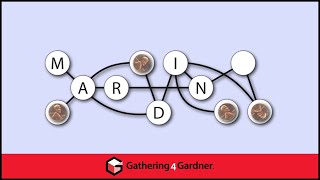
Bob Hearn - How Martin Gardner Inspired an Area of Theoretical Computer Science - CoM Oct 2021
Reconfiguration: How Martin Gardner Inspired an Area of Theoretical Computer Science A popular area in theoretical computer science for the past ten or fifteen years is known as “combinatorial reconfiguration”, or just “reconfiguration”. What is not widely appreciated is the debt this fie
From playlist Celebration of Mind 2021

From PhD to PhD: A Conference Mapping the Network on Lebanese Mathematics - Day 3 - June 3, 2021
“I dislike frontiers, political or intellectual, and I find that ignoring them is an essential catalyst for creative thought. Ideas should flow without hindrance in their natural course.” Michael Atiyah In the midst of social-political turmoil, financial meltdown, disease induced lockdown,
From playlist From PhD to PhD: A Conference Mapping the Network on Lebanese Mathematics - June 1-3, 2021

0313 [ MMO/MUD ] -- Refactoring
This is #313 in my series of live (Twitch) coding streams. This stream I worked on refactoring the unit tests for the Executor portion of my game server. Notebook page: https://tinyurl.com/vjnamjz -- Watch live at https://www.twitch.tv/rhymu8354
From playlist Excalibur

How To Build A Decentralized Crypto Exchange Operating On Ethereum | Introduction | #ethereum
Don’t forget to subscribe! In this project series, we are going to build a decentralized crypto exchange, a website where we can deposit ether and tokens. You will learn how to withdraw tokens and also to develop, sell and buy orders, where we can trade the tokens for a price. A crypto e
From playlist Build A Decentralized Crypto Exchange

An overview of the Token Classification task. You can learn more about token classification in this section of the course: https://huggingface.co/course/chapter7/2 This video is part of the Hugging Face course: http://huggingface.co/course Related videos: - Inside the Token classificatio
From playlist Hugging Face Tasks

Robert Ghrist, Lecture 3: Topology Applied III
27th Workshop in Geometric Topology, Colorado College, June 12, 2010
From playlist Robert Ghrist: 27th Workshop in Geometric Topology

Distributed systems, Microservices and Web APIs taking us to new challenges regarding authentication and authorization. - "One does not simply log in!" The standards OAuth2, OpenID Connect, and JSON Web Tokens (JWT) can help us mastering the auth* challenges in these architectures. We'll d
From playlist Talks

XCiT: Cross-Covariance Image Transformers (Facebook AI Machine Learning Research Paper Explained)
#xcit #transformer #attentionmechanism After dominating Natural Language Processing, Transformers have taken over Computer Vision recently with the advent of Vision Transformers. However, the attention mechanism's quadratic complexity in the number of tokens means that Transformers do not
From playlist Papers Explained

DevOpsDays NYC 2016 - Learning How to Dev in an Ops World by Frank Mitchell
DevOpsDays NYC 2016 - Learning How to Dev in an Ops World by Frank Mitchell Six months ago my team decided to take a RESTful web service (Conqueso) and rewrite it in a more scalable, auditable, highly-available fashion (propsd). As operations people, this was our first foray into deliveri
From playlist DevOpsDays NYC 2016

Crypto Explained: What are Token Burns? Why would someone want to destroy tokens forever?
What happens when you remove tokens from circulation? What are token burns and why would people want to remove tokens from supply? Chapters 0:00 What are token burns? Why are they necessary in the first place? What do they accomplish? 0:44 What happens when you remove money from circulati
From playlist What is... and What about...? A playlist that answers the most common crypto newbie questions.

Trusted CI Webinar: The NSF CC-DNI SecureCloud Project with Casimer DeCusatis
Originally recorded March 25th, 2019 Slides: http://hdl.handle.net/2142/103384 Cyberinfrastructure is undergoing a radical transformation as traditional data centers are replaced by cloud computing. Cloud hosted applications tend to have a poorly defined network perimeter, large attack s
From playlist Center for Applied Cybersecurity Research (CACR)

Rails Conf 2013 Rails' Insecure Defaults by Bryan Helmkamp
Out of the box, Rails provides facilities for preventing attacks like SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and more. As a result, it's considered one of the most secure web application frameworks available. Digging deeper, however, you can find a nu
From playlist Rails Conf 2013

How To Build A Decentralized Crypto Exchange Operating On Ethereum | Session 02 | #ethereum
Don’t forget to subscribe! In this project series, we are going to build a decentralized crypto exchange, a website where we can deposit ether and tokens. You will learn how to withdraw tokens and also to develop, sell and buy orders, where we can trade the tokens for a price. A crypto e
From playlist Build A Decentralized Crypto Exchange

