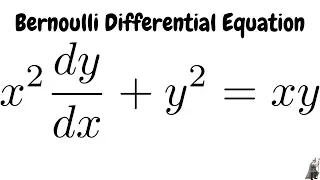Thomas Brierley grave cipher
The gravestone of Thomas Brierley (1785 – 1854 or -55) in Mellor, Greater Manchester, is one of the only ones in the United Kingdom known to incorporate masonic pigpen cypher in its inscription. Another is the gravestone of John Jennings within the St Peter and All Hallows Churchyard, West Huntspill. Still, another is the chest tomb of the Astles family, at St Laurence's Church, Frodsham, Cheshire. (See https://www.mysticmasque.com/history-mystery/masonic-cipher-grave-frodsham-church-cheshire). (Wikipedia).