
Can You Validate These Emails?
Email Validation is a procedure that verifies if an email address is deliverable and valid. Can you validate these emails?
From playlist Fun

In this video we look at translating a verbal expression to an algebraic one.
From playlist Algebra 1 Test 1

Verifying Particular Solutions to Differential Equations Calculus 1 AB
I reintroduce Differential Equations including the definition of a differential equations, the order of differential equations, the difference between particular solutions and general solutions, and the number of arbitrary constants you can expect when solving these equations. I then work
From playlist Calculus

Differential Equations: Verification Introduction
Given a possible solution to a differential equation, how can one verify whether or not it is an actual solution? The method depends on whether the possible solution is implicitly or explicitly defined.
From playlist Differential Equations

Validation In JavaScript | Form Validation In JavaScript Using Regular Expression | SimpliCode
This video on Validation in JavaScript will let you know everything about how a user's data can be validated with the help of Regex in JavaScript. In this JavaScript tutorial, you'll learn How Form validation in JavaScript using Regular expressions is possible. In addition, you'll also un
From playlist JavaScript Tutorial Videos 🔥[2022 Updated]

From playlist Week 9 2014

Validate Postcodes with Regular Expressions
More videos like this online at http://www.theurbanpenguin.com Regular expressions can be daunting when you see them but breaking them down, like most things they are not so scary. In this video we learn how to validate UK post codes by building a regular expression from the start.
From playlist Linux

DEFCON 19: Chip & PIN is Definitely Broken
Speakers: Andrea Barisani Inverse Path S.r.l. | Adam Laurie Aperture Labs Ltd | Zac Franken Aperture Labs Ltd | Daniele Bianco Inverse Path S.r.l. The EMV global standard for electronic payments is widely used for inter-operation between chip equipped credit/debit cards, Point of Sales d
From playlist DEFCON 19

DEFCON 19: Chip & PIN is Definitely Broken ( w speaker)
Speakers: Andrea Barisani Inverse Path S.r.l. | Adam Laurie Aperture Labs Ltd | Zac Franken Aperture Labs Ltd | Daniele Bianco Inverse Path S.r.l. The EMV global standard for electronic payments is widely used for inter-operation between chip equipped credit/debit cards, Point of Sale
From playlist Payments
EMV 101: Fundamentals of EMV Chip Payment
Commonly used globally in place of magnetic stripe, EMV chip technology helps to reduce card fraud in a face-to-face card-present environment; provides global interoperability; and enables safer and smarter transactions across contact and contactless channels. EMV implementation was initia
From playlist Payments
Thomas Genet: Towards static analysis of functional programs using term rewriting and tree automata
Find this video and other talks given by worldwide mathematicians on CIRM's Audiovisual Mathematics Library: http://library.cirm-math.fr. And discover all its functionalities: - Chapter markers and keywords to watch the parts of your choice in the video - Videos enriched with abstracts, b
From playlist Mathematical Aspects of Computer Science

Verify that y = Ax + B(x^3 + 1) is a Solution to the DE (2x^3 - 1)y'' - 6x^2y' + 6xy = 0
In this problem we have a solution to a differential equation and we are asked to verify that it is actually a solution. To do this we simply take derivatives and plug the function and all of it's required derivatives into the DE. If you enjoyed this video please consider liking, sharing,
From playlist Differential Equations Problems
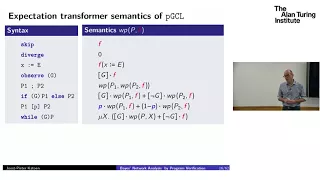
Bayesian Inference by Program Verification - Joost-Pieter Katoen, RWTH Aachen University
In this talk, I will give a perspective on inference in Bayes' networks (BNs) using program verification. I will argue how weakest precondition reasoning a la Dijkstra can be used for exact inference (and more). As exact inference is NP-complete, inference is typically done by means of sim
From playlist Logic and learning workshop

What if Current Foundations of Mathematics are Inconsistent? | Vladimir Voevodsky
Vladimir Voevodsky, Professor, School of Mathematics, Institute for Advanced Study http://www.ias.edu/people/faculty-and-emeriti/voevodsky In this lecture, Professor Vladimir Voevodsky begins with Gödel's second incompleteness theorem to discuss the possibility that the formal theory of f
From playlist Mathematics

OHM2013: Another Rambling Talk About EMV
For more information visit: http://bit.ly/OHM13_web To download the video visit: http://bit.ly/OHM13_down Playlist OHM 2013: http://bit.ly/OHM13_pl Speaker: Tim Becker A brief introduction to EMV, the protocol spoken between smart card based credit cards and terminals. A mixture of plast
From playlist OHM 2013

THIS is the most private and secure phone on the planet - GrapheneOS review and how to install
IMPORTANT UPDATE: The installation guide mentioned in the second half of this video is OUTDATED. Always follow the official the guide for proper up-to-date instructions: https://grapheneos.org/install/ There is only one spot available for the most private and secure phone you can get - and
From playlist TUTORIALS & HOW TO's

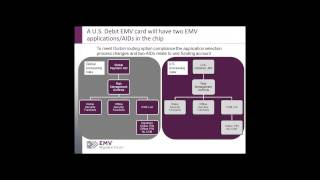
An Overview of EMV for the US Market
ACI Worldwide software powers electronic transactions for financial institutions, processors and retailers around the world - all the time, without fail. http://www.aciworldwide.com/emv ---------WEBINAR TRANSCRIPTION-------------- Today's topic is EMV: An Overview with Some US Considerat
From playlist Payments

27c3: Chip and PIN is Broken (en)
Speaker: Steven J. Murdoch Vulnerabilities in the EMV Protocol EMV is the dominant protocol used for smart card payments worldwide, with over 730 million cards in circulation. Known to bank customers as "Chip and PIN", it is used in Europe; it is being introduced in Canada; and there is
From playlist 27C3: We come in peace

Algebraic and Combinatorial Proofs: C(n,k)=C(n,n-k)
This video provides an algebraic proof and three combinatorial proofs for a binomial identity.
From playlist Counting (Discrete Math)
