
Integration 12 Trigonometric Integration Part 2 Example 4.mov
Another example of trigonometric integration.
From playlist Integration

Irrigation Efficiencies - Part 1
From playlist TEMP 1
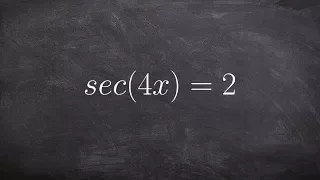
Solving trigonometric equations with multiple angles
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric equations, they include by factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the given
From playlist Solve Trigonometric Equations with Multi Angles
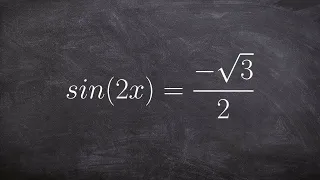
Solving trigonometric equations with multiple angles
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric equations, they include by factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the given
From playlist Solve Trigonometric Equations with Multi Angles

Integration 12 Trigonometric Integration Part 2 Example 1.mov
An example of trigonometric integration.
From playlist Integration
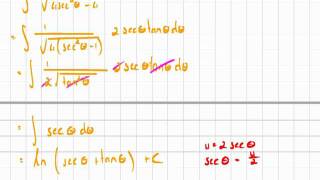
Integration 12_5_4 Trigonometric Integration.mov
Another example of trigonometric substitution.
From playlist Integration

Lawsplainer: There's No Such Thing as Collusion (It's Worse)
⭐️ Get my videos early & ad free (plus my exclusives!) only on Nebula. Save $10 per year! https://legaleagle.link/getnebula ⭐️ What counts a “collusion?” It’s a long list... The first 200 Legal Eagles can try Dashlane free for 30 days: https://www.dashlane.com/legaleagle 10% off Dashla
From playlist Law 101! The Law Explained.
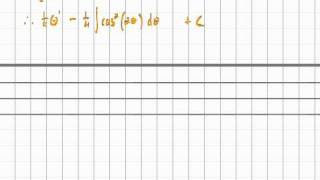
Integration 12 Trigonometric Integration Part 2 Example 2.mov
Another example of trigonometric integration.
From playlist Integration

Adam Savage's One Day Builds: Excalibur Henchmen Armor!
Among Adam's armor collection is another suit made by master armorer Terry English for the film Excalibur: one made for the villain Mordred's lead lieutenant. But this armor is missing key pieces from its ensemble, and Adam recalls his training from Terry to rebuild those parts and chemica
From playlist Adam Savage's One Day Builds
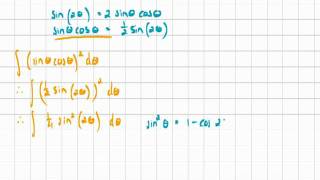
Integration 12 Trigonometric Integration Part 2 Example 3.mov
Another example of trigonometric integration.
From playlist Integration

16. Constitutional Government: Locke's Second Treatise (7-12)
Introduction to Political Philosophy (PLSC 114) In the opening chapters of his Second Treatise, Locke "rewrites" the account of human beginnings that had belonged exclusively to Scripture. He tells the story of how humans, finding themselves in a condition of nature with no adjudicating
From playlist Introduction to Political Philosophy with Steven B. Smith

"Please Commit More Blatant Academic Fraud" – A fellow PhD student's response.
A broadcast of, discussion and response to "Please Commit More Blatant Academic Fraud" blog post by Jacob Buckman. Made by a fellow PhD student and her Coffee Bean. ▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀▀ 🔥 Optionally, pay us a coffee to boost our Coffee Bean production! ☕ Patreon: https://www.patreon
From playlist Ms. Coffee Bean's How To

[ML News] Anthropic raises $124M, ML execs clueless, collusion rings, ELIZA source discovered & more
#mlnews #anthropic #eliza Anthropic raises $124M for steerable AI, peer review is threatened by collusion rings, and the original ELIZA source code was discovered. OUTLINE: 0:00 - Intro 0:40 - Anthropic raises $124M 3:25 - 65% of execs can't explain AI predictions 4:25 - DeepMind release
From playlist All Videos

29C3: Long live the protocoletariat! (EN)
Speakers: Eleanor Saitta | Smári McCarthy We're winning! The future looks like network politics! Wait, what the hell are network politics and how do they work? Is that like the Pirate Party, or the IETF, or Anonymous? In this talk, We'll try to answer this question, or at least confuse t
From playlist 29C3: Not my department

Why do firms collude, and why is this behavior inherently unstable? "EPISODE 30A: Collusion" by Dr. Mary J. McGlasson is licensed under a Creative Commons Attribution-NonCommercial-NoDerivs 3.0 Unported License.
From playlist Microeconomics modules

CERIAS Security:Framework for Identifying Compromised Nodes in Sensor Networks 3/6
Clip 3/6 Speaker: Ting Yu · North Carolina State University Sensor networks are vulnerable to physical attacks. Once a node's cryptographic key is compromised, an attacker may completely impersonate it, and introduce arbitrary false information into the network. Most existing techniqu
From playlist The CERIAS Security Seminars 2005 (2)

Obligation to Obey the Law - Political | WIRELESS PHILOSOPHY
In this Wireless Philosophy video, Matthew Chrisman (University of Edinburgh) explores the nature of our obligations to obey the law. Thanks for watching! To learn more about philosophy and critical thinking, please subscribe! http://bit.ly/1vz5fK9 More on Matthew Chrisman: https://goo.g
From playlist Introduction to Political Philosophy

Integration 12_5_3 Trigonometric Integration.mov
Another example of trigonometric substitution.
From playlist Integration

Cryptography and Preventing Collusion in Second Price (Vickery) Auctions - Michael Rabin
Michael Rabin Harvard University and Columbia University April 29, 2013 We present practically efficient methods for proving correctness of announced results of a computation while keeping input and intermediate values information theoretically secret. These methods are applied to solve th
From playlist Mathematics
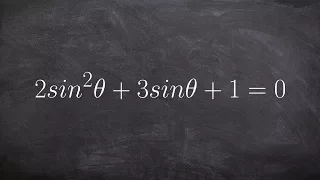
Solve for all of the solutions of an equation when you have to factor
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric equations, they include factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the given eq
From playlist Solve Trigonometric Equations by Factoring