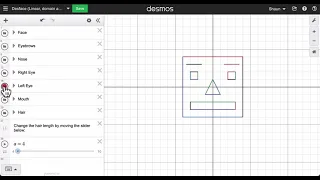
Here we show a quick way to set up a face in desmos using domain and range restrictions along with sliders. @shaunteaches
From playlist desmos

👉 Learn how to define angle relationships. Knowledge of the relationships between angles can help in determining the value of a given angle. The various angle relationships include: vertical angles, adjacent angles, complementary angles, supplementary angles, linear pairs, etc. Vertical a
From playlist Angle Relationships
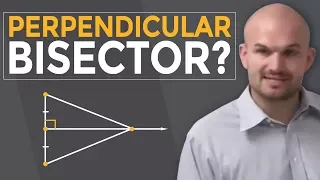
What is a perpendicular bisector
👉 Learn the essential definitions of triangles. A triangle is a polygon with three sides. Triangles are classified on the basis of their angles or on the basis of their side lengths. The classification of triangles on the bases of their angles are: acute, right and obtuse triangles. The cl
From playlist Types of Triangles and Their Properties

CCSS What is an angle bisector
👉 Learn how to define angle relationships. Knowledge of the relationships between angles can help in determining the value of a given angle. The various angle relationships include: vertical angles, adjacent angles, complementary angles, supplementary angles, linear pairs, etc. Vertical a
From playlist Angle Relationships

EEVblog #1374 - DIY Trezor Crypto Hardware Wallet - Part 1
How easy is it to take the open source Trezor Model T crypto hardware wallet files and manufacture your own? Or to modify or improve the design? The Trezor is open source hardware, so Dave checks out the Github and looks at the hardware files available and imports into Eagle and KiCAD. Whe
From playlist Cryptocurrency

Dimensions (1 of 3: The Traditional Definition - Directions)
More resources available at www.misterwootube.com
From playlist Exploring Mathematics: Fractals

28C3: TRESOR: Festplatten sicher verschlüsseln (de)
For more information visit: http://bit.ly/28C3_information To download the video visit: http://bit.ly/28C3_videos Playlist 28C3: http://bit.ly/28C3_playlist Speaker: tilo Herkömmliche Festplattenverschlüsselungen legen notwendige Schlüssel im RAM ab. Dadurch sind sie schutzlos Angr
From playlist 28C3: Behind Enemy Lines

EEVblog #1062 - Trezor Model T Hardware Wallet Review
Unboxing and review of the new Trezor Model T cryptocurrency bitcoin hardware wallet. And a comparison with the Ledger Nano S. Also a talk on Ethereum contracts, Myetherwaller and ICO's Crypto Currency: https://www.eevblog.com/crypto-currency/ https://kit.com/EEVblog/crypto-hardware Hard
From playlist Cryptocurrency

EEVblog #1048 - Ledger Nano S Crypto Hardware Wallet
A review and teardown of the Ledger Nano S crypto currency hardware wallet. Installation, setup, and transferring bitcoin cash, ethereum, and ripple. And a comparison with the Trezor, which one is better? Buy them here: https://kit.com/EEVblog/crypto-hardware Secure chip: http://www.st.co
From playlist Product Reviews & Teardowns

30C3: Trezor: Bitcoin hardware wallet (EN)
For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speaker: Pavol "stick" Rusnak TREZOR is a hardware wallet for Bitcoin. We identified security of the end users' computer as one of the main problems that block Bitcoin mass
From playlist 30C3
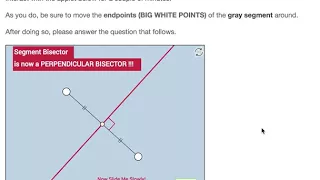
Perpendicular Bisector (Definition + 1 Theorem)
Link: https://www.geogebra.org/m/pFyDfP2D
From playlist Geometry: Dynamic Interactives!

wallet.fail (or How to Break the Most Popular Cryptocurrency Wallets)
n this presentation we will take a look at how to break the most popular cryptocurrency hardware wallets. We will uncover architectural, physical, hardware, software and firmware vulnerabilities we found including issues that could allow a malicious attacker to gain access to the funds of
From playlist Blockchain

👉 Learn the essential definitions of triangles. A triangle is a polygon with three sides. Triangles are classified on the basis of their angles or on the basis of their side lengths. The classification of triangles on the bases of their angles are: acute, right and obtuse triangles. The cl
From playlist Types of Triangles and Their Properties

EEVblog #1006 - Trezor Bitcoin Hardware Wallet Teardown
What's inside the Trezor hardware bitcoin wallet? A teardown to look at any physical hardware security, and a look at a possible side channel power line attack. http://amzn.to/2uk2ccP https://kit.com/EEVblog/crypto-hardware UPDATE: A technical detailed reply from the Trezor developer! htt
From playlist Cryptocurrency
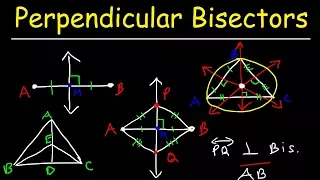
Perpendicular Bisector of a Line Segment and Triangle
This geometry video tutorial provides a basic introduction into the perpendicular bisector of a line segment and a triangle. it discusses the perpendicular bisector theorem and the definition of perpendicular bisectors in addition to how to use them in a geometry two column proof problem
From playlist Geometry Video Playlist

Bitcoin Q&A: Threshold Signatures and Shamir Secret Sharing
What are keyless, seedless threshold signatures? Does it have advantages over multi-signature schemes? What are the best practices for key storage by organizations? What is SLIP-39? How do I turn a BIP-39 recovery seed into K-of-N Shamir sharing scheme? Chapters 0:00 What are keyless, see
From playlist Bitcoin Q&A

André JOYAL - New variations on the notion of topos
The notion topos is a prominent member of a family of notions which includes that of abelian category, of locally presentable category and of higher topos. We propose two new members: the notion of locus and that of para-topos. The category of pointed spaces and the category of spectra are
From playlist Topos à l'IHES

Should I Update the Firmware on My Hardware Wallet? Cryptocurrency Security Explained
Your private key doesn't leave a hardware wallet, so why do you need to update the firmware? In this video, Andreas explains how firmware updates improve security. Chapters 0:00 The private key never leaves the hardware wallet. Why does it matter to update the device for security and safe
From playlist Key Management: How to Store and Use Bitcoin

Der Nürnberger Prozess - Die Verteidigung (5/8) / Hauptkriegsverbrecher-Prozess
Julius Streicher, Adele Streicher, Walther Funk, Verbrechen gegen die Humanität, Ausplünderung von besetzten Gebieten, Hjalmar Schacht, Reichswirtschaftsminister, Präsident der Reichsbank, Führerprinzip, Gregor Strasser, NSDAP, Adolf Hitler, Hermann Göring, Vizepräsident der Reichsbank, Em
From playlist Der Nürnberger Prozess - Die Verteidigung

👉 Learn the essential definitions of triangles. A triangle is a polygon with three sides. Triangles are classified on the basis of their angles or on the basis of their side lengths. The classification of triangles on the bases of their angles are: acute, right and obtuse triangles. The cl
From playlist Types of Triangles and Their Properties