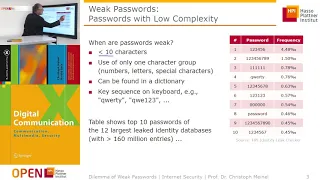
Why creating a strong password really matters
What is a “strong password”, exactly? What are some ways that you can create a password that is strong and easy to remember?
From playlist Internet Safety

Bitcoin Q&A: Why We Should Resist Financial Surveillance
Keywords/phrases: Privacy and transparency. Financial privacy has been the norm. Law enforcement has never had full access or visibility into our finances. Most law enforcement still use traditional mechanisms. We don't have to give away privacy to be safe. Privacy is not the antithesis of
From playlist Privacy and Surveillance

How to Create a Strong Password | Tips to Create Strong Passwords | Cyber Security | Simplilearn
In this video on how to create a strong password, we cover the reasons as to why having strong passwords for each individual account on the internet. We also take a look at some of the guidelines and tips to create strong passwords. In this chapter on cyber security, we also learn about pa
From playlist Cyber Security Playlist [2023 Updated]🔥

Staysafe.org: Protect your computer
The Internet is a global network that connects us to limitless information and opportunities. But there are risks involved with connecting to the Internet, such as downloading viruses and spyware onto computers and devices. Watch this video for four easy steps to help protect your computer
From playlist awareness

RSA Conference USA 2010: Will the Internet Ever Be Secure? Not Without Trust 1/3
Clip 1/3 Speaker: James Bidzos, Executive Chairman, VeriSign, Inc. Technologies and policies are important, but the future of Internet security rests upon trust. Without trust, people and organizations wont freely share information or purchase online. VeriSign has been building trust
From playlist RSA Conference USA 2010

The Global Financial Web Exposed: Britain’s Second Empire (Conspiracy Documentary) | Real Stories
The Spider’s Web: Britain’s Second Empire, is a documentary that shows how Britain transformed from a colonial power into a global financial power. At the demise of empire, City of London financial interests created a web of offshore secrecy jurisdictions that captured wealth from across t
From playlist War & History Documentaries

CERIAS Security: Secret Handshakes 2/6
Clip 2/6 Speaker: Stanislaw Jarecki · University of California at Irvine Secret Handshake is an authentication protocol with non-standard and strong anonymity property: Namely, the secrecy of the *affiliations* (i.e. the certificates) of party A who engages in this authentication prot
From playlist The CERIAS Security Seminars 2005 (1)

International Relations 101 (#39): Diversionary War
http://gametheory101.com/courses/international-relations-101/ How can leaders use asymmetric information for their own gain?
From playlist William Spaniel: International Relations 101

Off-the-Record Messaging: Useful Security and Privacy for IM
May 23, 2007 lecture by Ian Goldberg for the Stanford University Computer Systems Colloquium (EE 380). In this talk, Ian discusses "Off-the-Record Messaging" (OTR), a widely used software tool for secure and private instant messaging; he outlines the properties of Useful Security and Priva
From playlist Course | Computer Systems Laboratory Colloquium (2006-2007)

CERIAS Security: Secret Handshakes 1/6
Clip 1/6 Speaker: Stanislaw Jarecki · University of California at Irvine Secret Handshake is an authentication protocol with non-standard and strong anonymity property: Namely, the secrecy of the *affiliations* (i.e. the certificates) of party A who engages in this authentication prot
From playlist The CERIAS Security Seminars 2005 (1)

Cybersecurity: Crash Course Computer Science #31
Cybersecurity is a set of techniques to protect the secrecy, integrity, and availability of computer systems and data against threats. In today’s episode, we’re going to unpack these three goals and talk through some strategies we use like passwords, biometrics, and access privileges to ke
From playlist Computer Science

Nexus Trimester - Imre Csiszár (Renyi Institute, Budapest)
Secret Key Capacities for Source and Channel Models Imre Csiszár (Renyi Institute, Budapest) March 24, 2016 Abstract: This talk surveys fundamental limits for the problem of generating secret key (SK) for two or several parties, i.e., common randomness concealed from an eavesdropper. The
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme

CERIAS Security: Secret Handshakes 3/6
Clip 3/6 Speaker: Stanislaw Jarecki · University of California at Irvine Secret Handshake is an authentication protocol with non-standard and strong anonymity property: Namely, the secrecy of the *affiliations* (i.e. the certificates) of party A who engages in this authentication prot
From playlist The CERIAS Security Seminars 2005 (1)

19. Philip Roth, The Human Stain
The American Novel Since 1945 (ENGL 291) In this lecture on The Human Stain, Professor Hungerford traces the ways that Roth's novel conforms to and pushes beyond the genre she calls the Identity Plot. Exploring the various ways that race can be construed as category, mark, biology, or p
From playlist The American Novel Since 1945 with Amy Hungerford

What is the Black Knight satellite? Why do some people think it's a UFO? Tune in to learn more about the story of the Black Knight satellite in this episode. SUBSCRIBE | http://bit.ly/stdwytk-sub WEBSITE | http://bit.ly/stdwytk-home AUDIO PODCAST | http://bit.ly/stdwytk-audio-itunes
From playlist Most Popular

Confidentiality, Integrity, and Availability of Computer Security
http://www.365computersecuritytraining.com This video explains the CIA Triangle of computer security. For more FREE IT Security training videos visit our site! +CONFIDENTIALITY +INTEGRITY +AVAILABILITY These three are the fundamental characteristics of data that must be protected.
From playlist awareness