Evaluating Expressions Involving Inverse Cosecant, Inverse Secant, and Inverse Cotangent
Evaluate inverse trigonometric expression. http://mathispower4u.wordpress.com/
From playlist Inverse Trigonometric Functions
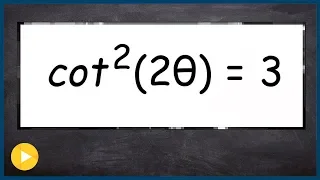
Find all the solutions of trig equation with cotangent
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric equations, they include by factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the given
From playlist Solve Trigonometric Equations
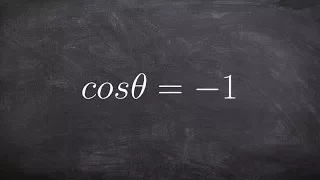
Solving a trigonometric equation with cosine equal to negative one
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric identities, they include by factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the give
From playlist Solve Trigonometric Equations

Introduction to Inverse Cosecant, Inverse Secant, and Inverse Cotangent
Introduction to the inverse functions of cosecant, secant, and cotangent http://mathispower4u.wordpress.com/
From playlist Inverse Trigonometric Functions
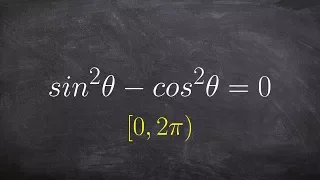
Solving a trigonometric equation with applying pythagorean identity
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric equations, they include factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the given eq
From playlist Solve Trigonometric Equations by Factoring
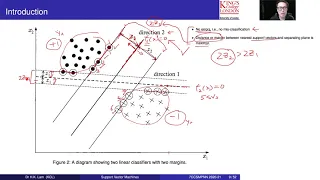
Support Vector Machines - Part 1: Introduction
This video is about Support Vector Machines - Part 1: Introduction Abstract: This is a series of videos about Support Vector Machines (SVMs), which will walk through the introduction, the working principle and theory covering a linearly separable case, non-separable case, nonlinear SVM an
From playlist Machine Learning
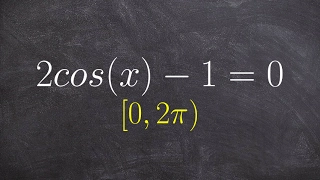
How to solve an equation with cosine
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric identities, they include by factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the give
From playlist Solve Trigonometric Equations

Totient Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

OpenGL - depth and stencil buffers
Code samples derived from work by Joey de Vries, @joeydevries, author of https://learnopengl.com/ All code samples, unless explicitly stated otherwise, are licensed under the terms of the CC BY-NC 4.0 license as published by Creative Commons, either version 4 of the License, or (at your o
From playlist OpenGL

Lehmer Factor Stencils: A paper factoring machine before computers
In 1929, Derrick N. Lehmer published a set of paper stencils used to factor large numbers by hand before the advent of computers. We explain the math behind the stencils, which includes modular arithmetic, quadratic residues, and continued fractions, including my favourite mathematical vi
From playlist Joy of Mathematics

Factor Stencils Review / HowTo
Factor stencils based on a design from the 1920s by D. N. Lehmer. His will factor any number up to 3,000,000,000,000. Mine are smaller, so only factor up to 200,000. This is episode 37 of my video series about calculating devices. Visit my site for PDFs and SVGs to download and make your
From playlist Calculating Devices Review / HowTos

Vacuum Tube Computer P.01 – Architecture and the MC14500B
In this episode, we take our first step towards building a vacuum tube computer! There’s a lot of different architectures out there, so we take a look at one that will hopefully work well for us. This is going to be a long road with lots of speedbumps and testing along the way. It should b
From playlist Vacuum Tube Computer

Totient - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Office Automation & Business Machines 1947 (IBM Chinese Character Typewriter, China, full video)
A Pre-Computer Look at Office Automation & Business Machines of 1947. This Vintage film describes many high-end business machines found in offices of the 1940’s, including the IBM Chinese Character Typewriter, and various machines for filming, stenciling, folding, lithographing, micofiche
From playlist Word Processing, Office Automation, Electronic Office Tools

EEVblog #415 - SMD Stencil Reflow Soldering Tutorial
Dave shows you how easy it is to do surface mount SMD reflow soldering with a solder paste stencil and a hot air gun: http://astore.amazon.com/eevblogstore-20 Hints and tips for quick and easy component placement, solder paste application, and reflow soldering using cheap easy to get tool
From playlist Soldering

Legend of Zelda Coding Tutorial - CS50's Intro to Game Development
Learn game development by creating a Legend of Zelda clone game using Lua and LÖVE2D. The principles you learn can apply to any programming language. This beginner's course teaches the foundations of game development. This video is lecture 5 of CS50's Intro to Game Development from Harvar
From playlist CS50's Introduction to Game Development

Adam Savage's One Day Builds: Painting Iron Man Armor!
What is Adam's favorite part of making? The paint, of course! Wanting a beaten-up, shiny metal finish for his Iron Man Mark I suit, Adam applies a gloss black undercoat, adds liquid chrome, then seals it all with a clear coat. But the job's only half done; Adam needs to wait a week for the
From playlist Adam Savage's One Day Builds

How to evaluate the composition of tangent inverse and cotangent
👉 Learn how to evaluate an expression with the composition of a function and a function inverse. Just like every other mathematical operation, when given a composition of a trigonometric function and an inverse trigonometric function, you first evaluate the one inside the parenthesis. We
From playlist Evaluate a Composition of Inverse Trigonometric Functions

Legend of Zelda - Lecture 5 - CS50's Introduction to Game Development 2018
00:00:00 - Introduction 00:06:04 - Legend of Zelda Demo 00:08:24 - Zelda Sprites 00:15:48 - Top-Down Perspective 00:17:52 - Dungeon Generation 00:24:08 - World Classes 00:32:18 - Infinite Dungeon Algorithm 00:38:30 - Room 00:44:48 - Entities and Game Objects as Data 00:56:03 - Stenciling 0
From playlist CS50's Introduction to Game Development 2018