position:fixed keyboard focus jump
If you have a keyboard input element in position fixed, and are scrolled away from the very top, the fixed element moves. Live in latest iOS.
From playlist position:fixed

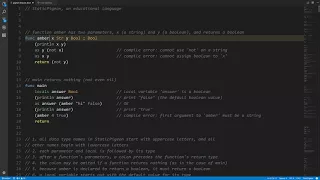
A Simple Programming Language - (part 13 of 13)
An introduction to programming with a reductively simple programming language. Part of a larger series teaching programming. Visit http://codeschool.org Please link to the playlist (http://www.youtube.com/playlist?list=PL2F1485C69B311408) rather than this video as individual videos may g
From playlist A Simple Programming Language

Jumping towards a Satoshi Nakamoto public key
In this video we discuss the public key and brute force for private keys. You find some more speed tuned applications as discussed on the bitcoin talk in the doc string of the code. You find the code here: https://gist.github.com/Nikolaj-K/b0bfd92a838733f5066091c8f7de5a23
From playlist Programming

Dustin Ingram: Static Typing in Python
In this talk, we’ll discuss the advantages and disadvantages to a static type system, as well as recent efforts to introduce static typing to Python via optional “type hints” and various tools to aid in adding types to Python code.
From playlist PyColorado 2019

From secret to WIF private key and address
In this video we discuss how to get from the secret private key number (a.k.a. exponent) to the WIF and how to get from the public key to address formats. He's the code: https://gist.github.com/Nikolaj-K/d548a12a45599070ea89ff376803758b
From playlist Programming

keyboard key not sensitive fix
Got a new keyboard recently and one of the keys wasn't very sensitive, so this is how I fixed it.
From playlist PC Peripherals

Raspberry Pi Setting a static IP Address
More videos like this online at http://www.theurbanpenguin.com Simple setting a static ip address from the command line of your Raspberian OS on RPi.
From playlist Raspberry Pi

Introduction of the Java programming language. Part of a larger series on learning to program. Visit proglit.com
From playlist Java (unit 1)

How To Create Grocery Delivery Web App In Python | Session 10 | #python | #webapp | #programming
Don’t forget to subscribe! In this project, we will create a simple grocery store web app in Python; Django, and PostgreSQL, we will learn how to create categories and subcategories, how to create products, manage stock, add to cart, completing an order, and creating a profile. Using Dja
From playlist Create Grocery Delivery Web App In Python

Writing an OS in Rust - Part 12d - Async Keyboard Input
This is my version of Philipp Oppermann's "BlogOS". It's a baremetal operating system that can boot off of a USB stick on any BIOS-compatible machine, which is pretty amazing. I'm going to be following the whole blog, one video at a time, and running the OS using QEMU instead of booting a
From playlist Rust OS

How To Create Multiplayer Minecraft Game Replica In Unity | Session 03 | #unity | #gamedev
Don’t forget to subscribe! In this project, we will create the Multiplayer Minecraft game Replica in Unity. We will build the game from scratch, but only the core game logic, in the second part we will be building server-side with UNET and connecting the two pieces together. Session 01
From playlist Create Multiplayer Minecraft Game Replica In Unity

Ruby Conference 2007 Deployable Ruby Runtimes by Rich Kilmer, Bruce Williams
Help us caption & translate this video! http://amara.org/v/FGcw/
From playlist Ruby Conference 2007

Black Hat USA 2010: WPA Migration Mode: WEP is Back to Haunt You 3/4
Speakers: Leandro Meiners, Diego Sor Cisco access points support WPA migration mode, which enables both WPA and WEP clients to associate to an access point using the same Service Set Identifier (SSID). If WEP clients are still around, we can use the traditional WEP cracking arsenal agains
From playlist BH USA 2010 - NETWORK

Software Development Course Day - 4 | Core Java Programming | Software Developer | Simplilearn
🔥 Enroll for FREE Java Course & Get your Completion Certificate: https://www.simplilearn.com/learn-java-basics-skillup?utm_campaign=SoftDevCourseOct14&utm_medium=DescriptionFirstFold&utm_source=youtube This software development course is a series of live sessions where we will understand
From playlist Simplilearn Live

Rails Conf 2013 Data Storage: NoSQL Toasters and a Cloud of Kitchen Sinks
By Casey Rosenthal What is the best data storage option for your application? We have an abundance of conventional wisdom when it comes to building applications on top of a relational database in the Ruby world. Building an application on top of a NoSQL database is a different story. I wi
From playlist Rails Conf 2013