
Network Analysis. Course introduction.
Introduction to the Social Network Analysis course.
From playlist Structural Analysis and Visualization of Networks.
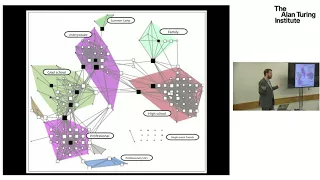
Social network analysis - Introduction to structural thinking: Dr Bernie Hogan, University of Oxford
Social networks are a means to understand social structures. This has become increasingly relevant with the shift towards mediated interaction. Now we can observe and often analyse links at a scale that far outpaces what was possible only decades ago. While this prompts new methodologies,
From playlist Data science classes

This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

From playlist Week 9: Social Networks

Why Study Criminology? | College Majors | College Degrees | Study Hall
What can you do with a Criminology major? In Criminology you can expect to study psychology, sociology, statistics, criminal justice and so much more. Basically, Criminology is the study of crime and the behavioral motivations of criminals. If you are able to think both analytically and
From playlist Fast Guides: To Electives and Majors

Network Analysis. Lecture 6. Link Analysis
Directed graphs. PageRank, Perron-Frobenius theorem and algorithm convergence. Power iterations. Hubs and Authorites. HITS algorithm. Lecture slides: http://www.leonidzhukov.net/hse/2015/networks/lectures/lecture6.pdf
From playlist Structural Analysis and Visualization of Networks.

CERIAS Security: USER AWARENESS OF SECURITY AND ITS IMPACT ON SYSTEMS MISUSE 5/6
Clip 5/6 Full title: USER AWARENESS OF SECURITY COUNTERMEASURES AND ITS IMPACT ON INFORMATION SYSTEMS MISUSE: A DETERRENCE APPROACH Speaker: John D'Arcy · Notre Dame Intentional insider misuse of information systems resources (i.e., IS misuse) represents a significant threat to organiza
From playlist The CERIAS Security Seminars 2009

'Engaging Students in Large Group Teaching' Dr Susan Keen
'Engaging Students in Large Group Teaching' Dr Susan Keen. UNILT Presentation UNSW
From playlist University Learning and Teaching

CERIAS Security: Dissecting Digital Data: Context & Meaning through Analytics 3/6
Clip 3/6 Speaker: Marcus Rogers · Purdue University This talk will look at how analytics can be used to increase our understanding of what digital evidence actually means. The real value of evidence is often related to the context and meaning of the data ; not just on its mere existence.
From playlist The CERIAS Security Seminars 2010

Network Analysis. Lecture 16. Social learning
Social learning in networks. DeGroot model. Reaching consensus. Influence vector. Social influence networks. Lecture slides: http://www.leonidzhukov.net/hse/2015/networks/lectures/lecture16.pdf
From playlist Structural Analysis and Visualization of Networks.

Network Analysis. Lecture 8. Network communitites
Cohesive subgroups. Graph cliques, k-plexes, k-cores. Network communities. Vertex similarity matrix. Similarity based clustering. Agglomerative clustering. Graph partitioning. Repeated bisection. Edge Betweenness. Newman-Girvin algorithm. Lecture slides: http//www.leonidzhukov.net/hse/201
From playlist Structural Analysis and Visualization of Networks.

Professor Mark Girolami: "Probabilistic Numerical Computation: A New Concept?"
The Turing Lectures: The Intersection of Mathematics, Statistics and Computation - Professor Mark Girolami: "Probabilistic Numerical Computation: A New Concept?" Click the below timestamps to navigate the video. 00:00:09 Introduction by Professor Jared Tanner 00:01:38 Profess
From playlist Turing Lectures

28 days of Tech Careers - Deveeshree Nayak - Data Analyst
28 days of Tech Careers - Day 17 - 2019.03.25 As we have learned two sessions on Data Scientists and Data Engineers from four amazing speakers, did you know there is also a Data Analyst position? But what do they do? If you have missed this session last time here is your chance to catch up
From playlist Kagglers on YouTube | Kaggle

CERIAS Security: USER AWARENESS OF SECURITY AND ITS IMPACT ON SYSTEMS MISUSE 1/6
Clip 1/6 Full title: USER AWARENESS OF SECURITY COUNTERMEASURES AND ITS IMPACT ON INFORMATION SYSTEMS MISUSE: A DETERRENCE APPROACH Speaker: John D'Arcy · Notre Dame Intentional insider misuse of information systems resources (i.e., IS misuse) represents a significant threat to organiza
From playlist The CERIAS Security Seminars 2009

Beyond the Screen: Jesenia Pizarro | ASU Online
Meet Jesenia Pizarro, a professor in Arizona State University’s School of Criminology and Criminal Justice and an affiliated faculty in the Office of Gender-Based Violence. In this episode of Beyond the Screen, Pizarro discusses her personal journey attending college as a first-generation
From playlist Beyond the Screen with ASU Online Faculty

CERIAS Security: USER AWARENESS OF SECURITY AND ITS IMPACT ON SYSTEMS MISUSE 2/6
Clip 2/6 Full title: USER AWARENESS OF SECURITY COUNTERMEASURES AND ITS IMPACT ON INFORMATION SYSTEMS MISUSE: A DETERRENCE APPROACH Speaker: John D'Arcy · Notre Dame Intentional insider misuse of information systems resources (i.e., IS misuse) represents a significant threat to organiza
From playlist The CERIAS Security Seminars 2009

24C3: I know who you clicked last summer
Speaker: Svenja Schröder A swiss army knife for automatic social investigation This talk introduces some techniques of social network analysis and graph theory. It aims at using simple approaches for getting interesting facts about networks. I will use the data of a popular community t
From playlist 24C3: Full steam ahead

DeepSec 2009: The Developmental Psychology of Intrusion Detection Systems
Thanks to the DeepSec organisation for making these videos available and let me share the videos on YouTube. Speaker: Stefan Schumacher Stefan Schumacher talks about psychologic aspects when designing intrusion detection systems. For more information visit: http://bit.ly/DeepSec_2009_i
From playlist DeepSec 2009

