
Let’s Travel to The Most Extreme Place in The Universe
The new 12,023 Human Era Calendar is here! https://kgs.link/calendar WORLDWIDE SHIPPING AVAILABLE. This time you can join us on a journey through the microcosm. Curious? Head over to our shop and get it while supplies last. Sources & further reading: https://sites.google.com/view/sources-
From playlist Medicine & Biology

More resources available at www.misterwootube.com
From playlist Using Complex Numbers
Chapter 5 of the Dimensions series. See http://www.dimensions-math.org for more information. Press the 'CC' button for subtitles.
From playlist Dimensions

Chapter 2 of the Dimensions series. See http://www.dimensions-math.org for more information. Press the 'CC' button for subtitles.
From playlist Dimensions

Chapter 1 of the Dimensions series. See http://www.dimensions-math.org for more information. Press the 'CC' button for subtitles.
From playlist Dimensions

MegaFavNumbers: Number of possible Bridge deals
My favorite big number. It is the number of possible Bridge deals. A contribution to the #MegaFavNumbers initiative
From playlist MegaFavNumbers
Chapter 6 of the Dimensions series. See http://www.dimensions-math.org for more information. Press the 'CC' button for subtitles.
From playlist Dimensions

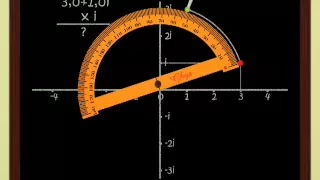
Polynomials with Trigonometric Solutions (2 of 3: Substitute & solve)
More resources available at www.misterwootube.com
From playlist Using Complex Numbers

22C3: Covert Communication in a Dark Network
Speakers: Ian Clarke, Oskar Sandberg A major new version of freenet At Defcon 13, we presented our ideas for creating scalable networks where only trusted friends speak directly to each other. In this talk, we will elaborate on this, discussing further experiments and results, as well as
From playlist 22C3: Private Investigations

DEFCON 13: Routing in the Dark: Scalable Searches in Dark P2P Networks
Speakers: Ian Clarke, Project Coordinator, FreenetProject Inc. Oskar Sandberg, Department of Mathematical Sciences, Chalmers Technical University, Sweden With peer to peer networks under fire by organizations using the legal system to attack participants, it seems that the only sustaina
From playlist DEFCON 13

Computer Networks: Crash Course Computer Science #28
Today we start a three episode arc on the rise of a global telecommunications network that changed the world forever. We’re going to begin with computer networks, and how they grew from small groups of connected computers on LAN networks to eventually larger worldwide networks like the ARP
From playlist Computer Science

The Rise and Fall of Route 66 (Why America's Greatest Road Fell into Oblivion)
Thanks to Bespoke Post for sponsoring this video! Head to https://bespokepost.com/itshistory20 and use code ITSHISTORY20 to learn more and get 20% off your first box.” U.S. Route 66, also known as the Will Rogers Highway, was one of the original highways constructed by the U.S. Highway Sy
From playlist IT'S HISTORY Feature Videos

Living With Nepal's Last Nomads (Global Documentary) | Real Stories
In a demanding and emotional journey, Kate Humble travels with the Raute, Nepal's very last nomadic community of just 140 hunter-gatherers. Facebook - https://www.facebook.com/RealStoriesChannel Instagram - @realstoriesdocs Twitter: https://twitter.com/realstoriesdocs Content licensed fr
From playlist Global Documentaries

Stanford Seminar - Border Gateway Protocol: the Good, Bad, and Ugly of Internet Routing
"Border Gateway Protocol: the Good, Bad, and Ugly of Internet Routing" - Jim Cowie of Dyn Colloquium on Computer Systems Seminar Series (EE380) presents the current research in design, implementation, analysis, and use of computer systems. Topics range from integrated circuits to operatin
From playlist Engineering

What Is The Interplanetary Transport Network? Free Travel Across the Solar System
Sure, if you've got lots of energy, you can zip around the Solar System. But if you’ve got time and rocket fuel is in short supply, you can take the Interplanetary Superhighway. References: http://www2.esm.vt.edu/~sdross/papers/AmericanScientist2006.pdf http://www.gg.caltech.edu/~mwl/publ
From playlist The Solar System

Let's talk about routing security
This talk covers how (in)secure in the routing at the global scale, covers about IRR in detail. Includes examples, tools and challenges with IRR based BGP filtering. It also gives a brief introduction to RPKI as well as latest developments in this domain (AT&T doing RPKI based filtering, G
From playlist Center for Applied Cybersecurity Research (CACR)

DEFCON 15: Routing in The Dark: Pitch Black
Speakers: Nathan S. Evans Ph.D. Graduate student, University of Denver Christian Grothoff, Ph.D. Assistant professor of computer science at the University of Denver There is a pervasive dream about a free Internet which is robust, fully decentralized yet efficient, and which ensures priv
From playlist DEFCON 15

DEFCON 16: Stealing The Internet - A Routed, Wide-area, Man in the Middle Attack
Speakers: Anton Kapela, Security Researcher Alex Pilosov, Security Researcher In this presentation we're going to show Defcon how broken the Internet is, how helpless its users are without provider intervention, and how much apathy there is towards routing security. With the method descr
From playlist DEFCON 16

Chapter 4 of the Dimensions series. See http://www.dimensions-math.org for more information. Press the 'CC' button for subtitles.
From playlist Dimensions
