Key Management & Distribution: Part 1
Fundamental concepts of Distribution of public & private keys are discussed. PKI and PKIX are analyzed. Digital certificates standards are presented
From playlist Network Security

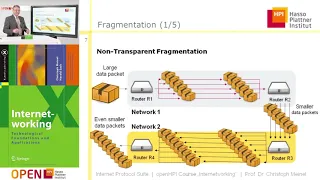
An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

Network Security, Part 1 : Basic Encryption Techniques
Fundamental concepts of network security are discussed. It provides a good overview of secret Key and public key Encryption. Important data encryption standards are presented.
From playlist Network Security

Cybersecurity Tutorial | Demo On Man In The Middle Attack | Cybersecurity Training | Edureka
🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl This "Cybersecurity tutorial" video presented by edureka gives an indepth information about the Cyber Security world and talks about its basic concepts.
From playlist Cyber Security Training for Beginners | Edureka

Communications and Network Security | CISSP Training Videos
🔥 Enroll for FREE CISSP Course & Get your Completion Certificate: https://www.simplilearn.com/learn-cloud-security-basics-skillup?utm_campaign=CCSP&utm_medium=DescriptionFirstFold&utm_source=youtube Communication and Network Security : Domain 4 of the CISSP certification course offered by
From playlist Cyber Security Playlist [2023 Updated]🔥

What is Man-in-the-Middle Attack | MITM Attack Explained | Edureka | Cybersecurity Rewind - 4
🔥Edureka Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training This Edureka video on "What is Man-in-the-Middle Attack" will help you understand what is Man-in-the-Middle Attack and how you can prevent it. Cybersecurity Training Playlist: https://bit.ly/2NqcTQ
From playlist Edureka Live Classes 2020

Network Security Tutorial | Introduction to Network Security | Network Security Tools | Edureka
🔵 Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl This Edureka video gives an introduction to Network Security and its nuances. Topics covered in this video are: 1.Need for Network Security 2.What is
From playlist Cyber Security Training for Beginners | Edureka

CISA Domain 4 | Information Systems Operations | Simplilearn
This CISA domain, provides information on assurance that the processes for information systems operations, maintenance and support meet the organization’s strategies and objectives. 🔥Free CISA Course: https://www.simplilearn.com/learn-information-systems-fundamentals-skillup?utm_campaign=C
From playlist Cyber Security Playlist [2023 Updated]🔥

IoT Crash Course | IoT Course | Internet Of Things | Internet Of Things Full Course | Simplilearn
This IoT crash course video introduces you to the IoT Technology and how it is revolutionizing the world today. Internet of things or IoT allows devices to connect with one another and communicate over the internet. This IoT crash course video describes what IoT is, its architecture and th
From playlist IoT Traning [2022 Updated]

What Is IoT? | What Is IoT Technology And How It Works | Internet Of Things Explained | Simplilearn
Internet of Things is the next big thing. It is extending its power beyond just traditional computers or smartphones. It involves several physical devices interconnected and capable of transferring data over a network. The Internet of Things is actually a pretty simple concept, it means ta
From playlist IoT Traning [2022 Updated]

IOT Tutorial | IOT Tutorial For Beginners | IOT - Internet Of Things | IOT Course | Simplilearn
🔥 Enrol in our IOT Course: https://www.simplilearn.com/iot-certification-training-course?utm_campaign=IOTTutorialAug2021-hdZzNOQV5vU&utm_medium=DescriptionFF&utm_source=youtube This IoT tutorial video introduces you to IoT Technology and how it is revolutionizing the world today. Internet
From playlist IoT - Internet of Things Training Videos [2022 Updated]

🔥IoT Full Course 2022 | IoT Tutorial For Beginners | Internet Of Things Full Course | Simplilearn
🔥FREE IoT Course With Completion Certificate: https://www.simplilearn.com/learn-iot-basics-skillup?utm_campaign=IoTFullCourse&utm_medium=Description&utm_source=youtube This IoT Full course video introduces you to IoT Technology and how it is revolutionizing the world today. The Internet o
From playlist Simplilearn Live

Cyber Security Full course - 11 Hours | Cyber Security Training For Beginners | Edureka
🔥𝐄𝐝𝐮𝐫𝐞𝐤𝐚 𝐂𝐲𝐛𝐞𝐫 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 (𝐔𝐬𝐞 𝐂𝐨𝐝𝐞: 𝐘𝐎𝐔𝐓𝐔𝐁𝐄𝟐𝟎) : https://www.edureka.co/cybersecurity-certification-training This Edureka video on "Cyber Security Full Course" will help you understand and learn the fundamentals of Cyber Security. This Cyber Security Tutorial is ideal for both be
From playlist Cyber Security Training for Beginners | Edureka

Cryptography is a complex and confusing subject. In this talk you will learn about the core components of cryptography used in software development: securing data with encryption, ensuring data integrity with hashes and digital signatures, and protecting passwords with key derivation funct
From playlist Blockchain