Fundamental concepts of Digital Signatures are discussed. ElGamal and Schnorr Digital Signature schemes are analyzed. Digital signature standard is presented.
From playlist Network Security

Back To Signatures Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Certificates And Signatures Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Fundamental concepts of Digital Signatures are discussed. ElGamal and Schnorr Digital Signature schemes are analyzed. Digital signature standard is presented.
From playlist Network Security

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

zkSNARKs -- Recent progress and applications to blockchain protocols by Chaya Ganesh
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

MPC in the Head With Applications to Blockchain (Lecture 1) by Carmit Hazay
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

Privacy-preserving Information Sharing: Tools and Applications: Dr Emiliano De Cristofaro
Short Bio: I am a Reader (Associate Professor) in Security and Privacy Enhancing Technologies at University College London (UCL), where I am affiliated with the Computer Science Department and the Information Security Group. Before joining UCL in 2013, I was a research scientist at Xerox
From playlist Turing Seminars

Zero Knowledge Proofs - Seminar 1 - Introduction
This seminar series is about the mathematical foundations of cryptography. In this series Eleanor McMurtry is explaining Zero Knowledge Proofs (ZKPs), a fascinating set of techniques that allow one participant to prove they know something *without revealing the thing*. You can join this s
From playlist Metauni

CERIAS Security: Secret Handshakes 2/6
Clip 2/6 Speaker: Stanislaw Jarecki · University of California at Irvine Secret Handshake is an authentication protocol with non-standard and strong anonymity property: Namely, the secrecy of the *affiliations* (i.e. the certificates) of party A who engages in this authentication prot
From playlist The CERIAS Security Seminars 2005 (1)
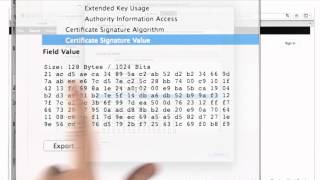
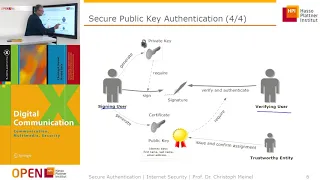
Certificates And Signatures - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

CERIAS Security: Secret Handshakes 3/6
Clip 3/6 Speaker: Stanislaw Jarecki · University of California at Irvine Secret Handshake is an authentication protocol with non-standard and strong anonymity property: Namely, the secrecy of the *affiliations* (i.e. the certificates) of party A who engages in this authentication prot
From playlist The CERIAS Security Seminars 2005 (1)

Theory and Practice of Cryptography
Google Tech Talks December, 12 2007 ABSTRACT Topics include: Introduction to Modern Cryptography, Using Cryptography in Practice, Proofs of Security and Security Definitions and A Special Topic in Cryptography Speaker: Steve Weis Steve Weis received his PhD from the Cryptography and In
From playlist Cryptography, Security

CERIAS Security: Protocols and Systems for Privacy Preserving Protection of Digital Identity 2/5
Clip 2/5 Speaker: Abhilasha Bhargav-Spantzel In this presentation I introduce a number of techniques that address the above problems. The approach is based on the concept of privacy preserving multi-factor identity verification. The main technique consists of verifying multiple identi
From playlist The CERIAS Security Seminars 2007

IMT4889 Spec.in Decentralised Tech
IMT4889 Specialisation in Decentralised Tech Lecture, Monday, 27.09.2021
From playlist Decentralisation

Efficient Verification of Computation on Untrusted Platforms - Yael Kalai
Computer Science/Discrete Mathematics Seminar I Topic: Efficient Verification of Computation on Untrusted Platforms Speaker: Yael Kalai Affiliation: Massachusetts Institute of Technology/Microsoft Date: February 13, 2023 Efficient verification of computation is fundamental to computer sc
From playlist Mathematics