
What is a Shadow? | Don't Memorise
How can we describe a shadow? Is it just a spot of darkness? Yes that's correct! It is just a spot of darkness where the light is blocked by object(s)! To know more about it watch the entire video! To access all videos related to Shadows, enroll in our full course now: https://infinityle
From playlist Physics

Veritasium SLINKY video: http://bit.ly/SGD73o Veritasium channel... SUBSCRIBE: http://bit.ly/RoMMH7 A great Veritasium episode about using video to teach: http://bit.ly/VOsZVx Vsauce2 LEANBACK about shadows: http://bit.ly/VOt8rP Vsauce3 explains how realistic SimCity is... SUBSCRIBE: htt
From playlist Physics

Shadows of Computation - Lecture 1 - Making subtle ideas apparent
Welcome to Shadows of Computation, an online course taught by Will Troiani and Billy Snikkers, covering the foundations of category theory and how it is used by computer scientists to abstract computing systems to reveal their intrinsic mathematical properties. In the first lecture Will in
From playlist Shadows of Computation

You have likely heard of the dark web although you may have never had access to it. It’s one of the three internets ‘layers.’ But what are these three ‘layers’? First up is the surface web, which consists of anything you can find online with a quick search on Google. Second, there is the
From playlist Engineering Wonders
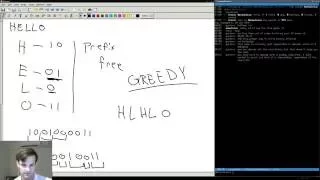
Making some huffman diagrams for my next video! -- Watch live at https://www.twitch.tv/simuleios
From playlist Huffman forest

Shadows of Computation - Lecture 2 - When are two mathematical objects the same?
Welcome to Shadows of Computation, an online course taught by Will Troiani and Billy Snikkers, covering the foundations of category theory and how it is used by computer scientists to abstract computing systems to reveal their intrinsic mathematical properties. In the second lecture Billy
From playlist Shadows of Computation

TUT1046 Secure by default anti exploit techniques and hardenings in SUSE products
This tutorial session was delivered at SUSECON in April 2019, in Nashville, TN. Abstract: Security is more important then ever. That's why we at SUSE enable anti-exploit techniques and hardenings in our products. This talk explains to you the basic of technologies like - Stack cannaries -
From playlist SUSECON 2019

For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speaker: Andreas Bogk Violation of memory safety is still a major source of vulnerabilities in everyday systems. This talk presents the state of the art in compiler instrume
From playlist 30C3

Creative Text Effects With CSS
So let’s have some fun with text! In this talk, the speaker will show you how to make effects with accessible, searchable, and selectable text (Without the need for complicated markup or JavaScript). Sometimes it’s easy to forget the power of CSS but there is a lot you can do with a little
From playlist Web Design: CSS / SVG

Lecture 10, T. S. Eliot, of UGS 303, Ideas of the Twentieth Century, at the University of Texas at Austin, Fall 2013
From playlist UT Austin: UGS 303 Political Philosophy - Ideas of the 20th Century | CosmoLearning.org Philosophy

CERIAS Security: The Best Defense is Information 2/5
Clip 2/5 Speaker: Jeremy Rasmussen · Sypris Electronics In the course of doing security vulnerability testing for government and commercial clients over the past 10 years, our Information Security Solutions team at Sypris Electronics has seen a lot of interesting things—perhaps none more
From playlist The CERIAS Security Seminars 2009
Shadows of Computation - Lecture 5 - What is Computation?
Welcome to Shadows of Computation, an online course taught by Will Troiani and Billy Snikkers, covering the foundations of category theory and how it is used by computer scientists to abstract computing systems to reveal their intrinsic mathematical properties. In the fifth lecture Will sp
From playlist Shadows of Computation

The Dark Souls of Idea Channel Episodes
Viewers like you help make PBS (Thank you 😃) . Support your local PBS Member Station here: https://to.pbs.org/donateidea The Dark Souls of Everything Tweet us! http://bit.ly/pbsideachanneltwitter Idea Channel Facebook! http://bit.ly/pbsideachannelfacebook Talk about this episode on reddi
From playlist Newest Episodes

An in-depth discussion about Rust Ownership and Borrowing, including memory management concepts. This Rust programming language tutorial series is aimed at easing your training step by step. Rust is a systems level language aimed at speed and safety and can be run cross-platform, includi
From playlist Rust Tutorial

27c3: I Control Your Code (en)
Speaker: Mathias Payer Attack Vectors Through the Eyes of Software-based Fault Isolation Unsafe languages and an arms race for new bugs calls for an additional line of defense in software systems. User-space virtualization uses dynamic instrumentation to detect different attack vectors a
From playlist 27C3: We come in peace

DEFCON 15: Remedial Heap Overflows: dlmalloc style
Speaker: Atlas Sometimes even the top dudes need a refresher course. Remedial Heap Overflows is not so much a lesson to the lame, but a refresher for the leet. One day the speaker was approached (in a subway, of course) by a top-notch dude (who has his own posse) and asked how they work.
From playlist DEFCON 15

I was tired. Sorry. -- Watch live at https://www.twitch.tv/simuleios
From playlist Huffman forest

Arindam Paul - JavaScript VM internals, EventLoop, Async and ScopeChains
This talk provides: 1. A crisp understanding of the JavaScript VM and how a single threaded engine can be massively parallel. 2. How event loop and callbacks works, example of blocking and non-blocking codes, ES6 generators for custom Async signaling. 3. How function definitions happen
From playlist Software Development Lectures

Live stream where I (Brooks) wake myself up in the morning with silly side projects and algorithm practice. This stream is scheduled for 7am Mountain Time every weekday. I tweet out shortly before I begin each stream, and definitely if I am going to miss a stream. Currently I am learning
From playlist Rust Book

What kind of particles comprise the dark matter?
Subscribe to our YouTube Channel for all the latest from World Science U. Visit our Website: http://www.worldscienceu.com/ Like us on Facebook: https://www.facebook.com/worldscienceu Follow us on Twitter: https://twitter.com/worldscienceu
From playlist Science Unplugged: Dark Matter